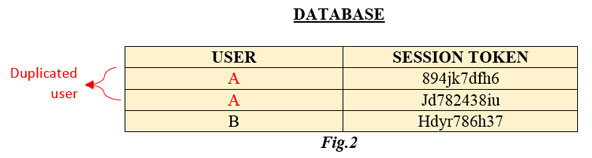
Session Vulnerabilities in Web Applications
What is session?
Session is about authenticating the communication between the user and the server. To understand this concept better see the following scenario shown in Fig.1.
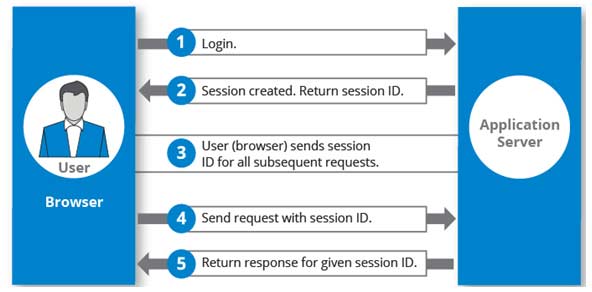
Fig 1
Here it?s shown how the sever grants a session id/token to the user when he is logging in. Every time the user requests the server to show a new page, the user has to send the session id/token along with it. The server validates the requested session id/token and responds to the user. So through this it can be understood that every login page has a session. But the important question is, whether it is secure? Sessions can be implemented using one of these ways ? Session Cookies, Header parameters, HTTP body parameters, Authentication tokens, etc.