What is Clickjacking?
Clickjacking is an interface-based attack that tricks a user into clicking on content in a decoy website, while the actual click interacts with actionable content in a hidden website. This can cause users to unwittingly download malware, visit malicious web pages, transfer money, provide credentials or sensitive information, or make online purchases.
Defending against Clickjacking
- Using content/ad blockers- Customers can protect themselves when visiting websites by using ad or content blockers. These tools use updated block lists to prevent malicious content from rendering on your browser, reducing the risk of clickjacking attacks.
- Vulnerability Scanning- Compromised WordPress social media plugins may redirect likes and shares to malicious content. Scan your applications with a vulnerability scanner for protection.
- X-Frame-Options-
X-Frame-Options is an HTTP header option that is used to specify whether a page can be embedded in a <frame >, <iframe >, <embed> or <object> element.
There are three possible values for X-Frame-Options: - Content-Security-Policy-
Content-Security-Policy, like X-Frame-Options, includes a set of several HTTP-based headers that help you secure your web application.
- To allow restricting of frames to self (similar to selforigin) which allows only embedding from the same website-
Content-Security-Policy: frame-ancestors 'self'; -
To allow only the defined sites for embedding and deny everything else-
Content-Security-Policy: frame-ancestors www.example.com www.example2.com;
- To allow restricting of frames to self (similar to selforigin) which allows only embedding from the same website-
X-Frame-Options: deny
The page cannot be displayed in a frame, regardless of the site attempting to do so.
X-Frame-Options: sameorigin
The page can only be displayed in a frame on the same origin as the page itself.
X-Frame-Options: allow-from http://example.com
The page can only be displayed in a frame on the specified origin.
Configuring Apache
To configure Apache to send the X-Frame-Options header for all pages, add this to your site's configuration file(httpd.conf):
Header always append X-Frame-Options SAMEORIGIN
Header append X-FRAME-OPTIONS "SAMEORIGIN"
Configuring IIS
To configure IIS to add an X-Frame-Options header to all responses for a given site, follow these steps:
- Open Internet Information Services (IIS) Manager.
- In the Connections pane on the left side, expand the Sites folder and select the site that you want to protect.
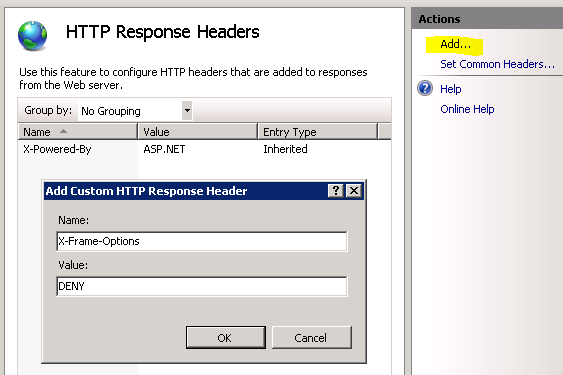
- Double-click the HTTP Response Headers icon in the feature list in the middle
- In the Actions pane on the right side, click Add.
- In the dialog box that appears, type X-Frame-Options in the Name field and type SAMEORIGIN or DENY in the Value field.
- Click OK to save your changes.
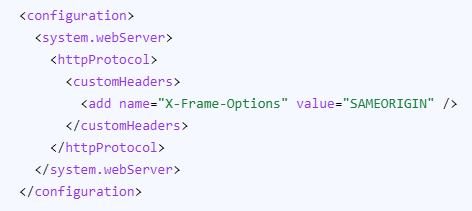
To configure IIS to send the X-Frame-Options header, add the following code to your site's Web.config file:
<configuration><system.webServer>
<httpProtocol>
<customHeaders>
<add name="X-Frame-Options" value="SAMEORIGIN" />
</customHeaders>
</httpProtocol>
</system.webServer>
</configuration>