HTTP Header Data Leakage Vulnerability
HTTP stands for Hyper Text Transfer Protocol. As the name itself reveals, http is a protocol that is used by World Wide Web (www) to define how the message has to be transmitted, what has to be transmitted and what actions should be taken in response of the requests. In short it is used for fetching of messages in the form of html pages/documents between the server and the client. These messages are called http request and http response.
This HTTP that acts as an underlying protocol for the WWW, contains 2 main parameters in the request and response message format: HEADER and BODY.
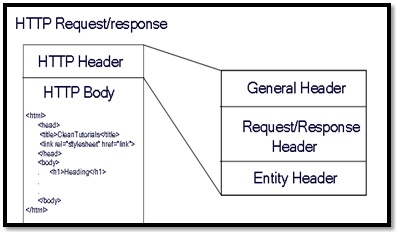
Information regarding the HTTP Body and the Request/Response are contained in the http header. All though this is natural that all headers contain those information, it is important to make sure that sensitive information such as Auth is not mentioned in the http header as a parameter.
Including any authentication validating parameter on the header can tempt the hacker to brute force the key/algorithm to get the corresponding page. Therefore any sensitive information should not be added on the http header because this leaks sensitive information unnecessarily and can be used for further attacks.
The solution for this problem is as simple as it sounds that is to not enter any validating parameter on the header. Even if you are to add a sensitive parameter, make sure you encrypt it strongly so that any hacker cannot guess and decrypt the values easily.










