How Authentication Can Be Bypassed
Authentication:
The process where the user who is trying to gain access is being verified before getting the access. This is done by asking for user to enter his/her credentials by entering username/ user ID and password.
Authentication Bypass:
Trying to fool the system and bypassing the authentication process by not entering the right credentials is called authentication bypass. Or in other words having a loop hole in the application which allows a user to access application resources without being authenticated is called authentication bypass.
Server side:
It is where the webserver is placed and performs its action.
Client side:
It is the action that takes place on the user's computer.
Some common ways through which authentication can be bypassed are:
- Direct page request
- Parameter modification
- Session ID Prediction
- SQL Injection
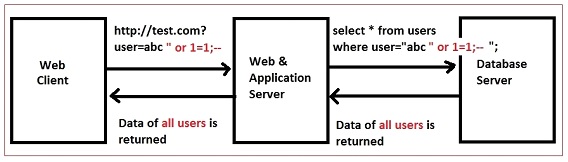
Fig.1: Authentication bypass using SQL Injection
Authentication bypass is a result of improper authentication mechanism followed for application resources. Unauthenticated access to critical content could result to improper access control and session management or improper input validation (SQL Injection).
Ways through which authentication bypass could be prevented are:
- Request and response must be sent over HTTPS
- Add userid in the response, add some random characters and encrypt it. This will add uniqueness to the request and its corresponding response.










