Web Vulnerability – Options Method
About the OPTIONS method
The OPTIONS method is primarily used for diagnostic and debugging purposes; it essentially reports which HTTP methods are allowed on the web server. However, there is a possibility that it could enable an attacker to perform malicious actions or gain knowledge about the system.
How to fix it
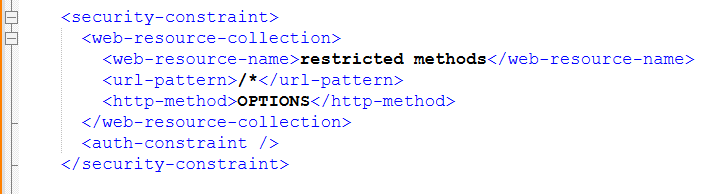
The HTTP OPTIONS method should be disabled.
How to do it
Methods to disable OPTION method may vary depending upon the type and version of the web server.
IIS (For new versions)
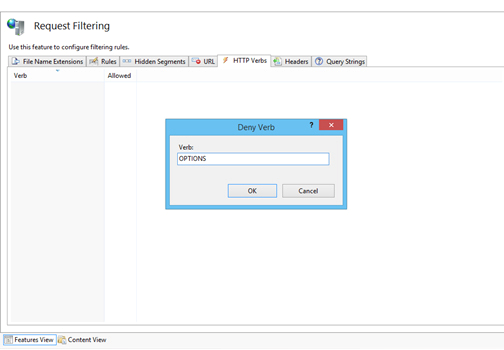
In IIS, this can be done by denying the OPTIONS verb from the HTTP Verb Request Filtering rules in IIS.
- Open IIS Manager.
- Select the name of the machine to configure this globally (or change to the specific web site for which you need to configure this).
- Double click on "Request Filtering".
- Change the HTTP Verbs tab.
- From the Actions panel and select "Deny Verb".
- Insert 'OPTIONS' in the Verb, and press OK to save changes.
IIS (For old versions)
In IIS, this can be done by denying the OPTIONS verb from the HTTP Verb Request Filtering rules in IIS.
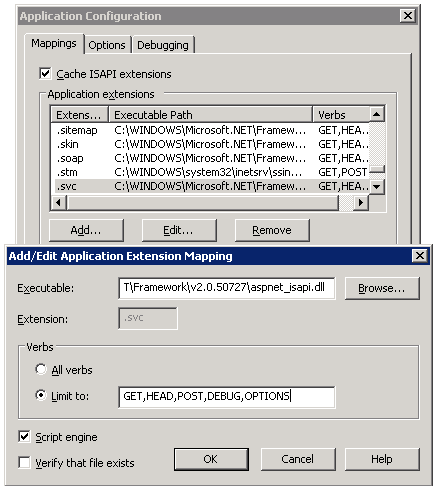
- In IIS Manager, right click on the website and select Properties.
- Switch to the Home Directory tab, and click the Configuration button.
- In the list of application extensions, locate the extension that your web application uses and click the Edit button.
- In the Limit To field, specify the method you want to support and delete the ones you don't.
Apache
To disable the OPTION Method in the Apache web server, you can use the “mod_rewrite” module. This module is a rules-based, rewriting engine that can be incorporated into the standard Apache configuration file or as part of an “.htaccess file”. Each mod_rewrite rule consists of four main components: the directive to load the module, the directive to activate the rewrite engine, a rewrite condition, and a rewrite rule.
Before creating an “.htaccess” file under the document root directory and adding the code, make sure that the Apache rewrite module and .htaccess are enabled.
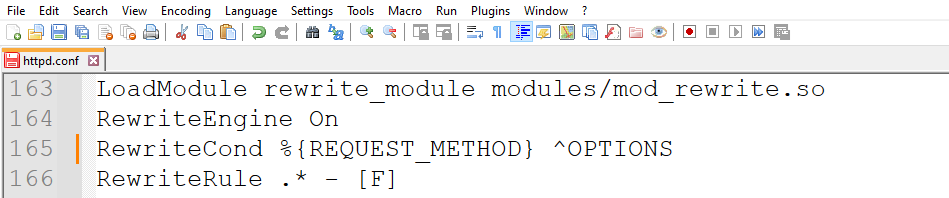
Search your apache configuration file(s) for mod_rewrite.so. If it is not found, you need to add 3 lines one below the other in your apache configuration file (typically known as httpd.conf). Assuming you are using a Windows server, the Apache configuration file is typically located at C:\Program Files\Apache\conf\httpd.conf
Steps:
Add the following 3 lines under “LoadModule rewrite_module modules/mod_rewrite.so”
To rewrite the engine-
- RewriteEngine On
To disable the engine-
- RewriteCond %{REQUEST_METHOD} ^OPTIONS
To disable the HTTP requests-
- RewriteRule .* - [F]
( [F] flag results in a 403 Forbidden response to any requests using the OPTION method, effectively disabling them.)
- Next, restart the Apache webserver to apply changes.
Note: By default, Rewrite configurations are not inherited across virtual servers. Add “RewriteEngine On” to each virtual host.