Server-Side Request Forgery (SSRF) vulnerability & Its Fixation
Server-Side Request Forgery (SSRF) occurs when an attacker manipulates a server to send HTTP requests to unintended internal or external systems.

Attacker can pass internal URLs like http://localhost:8080/admin, potentially exposing internal services.
Impact of SSRF
- Access to internal-only resources (e.g., cloud metadata, admin panels).
- Port scanning internal networks.
- Bypassing firewalls and network segmentation.
- In severe cases, remote code execution or cloud credential theft (e.g., AWS IAM keys).

Solution to Fix SSRF
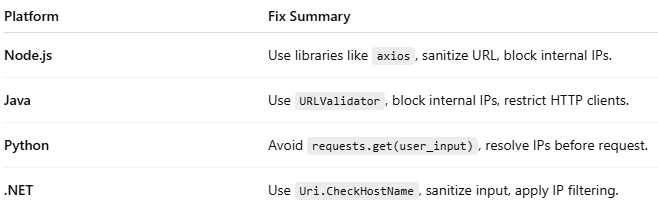
To prevent or fix SSRF (Server-Side Request Forgery) vulnerabilities, you need to implement strong input validation, network restrictions, and safe request handling. Below is a structured SSRF mitigation checklist and sample solutions based on common environments.1. Input Validation and Whitelisting
Only allow requests to explicitly defined, trusted domains/IPs.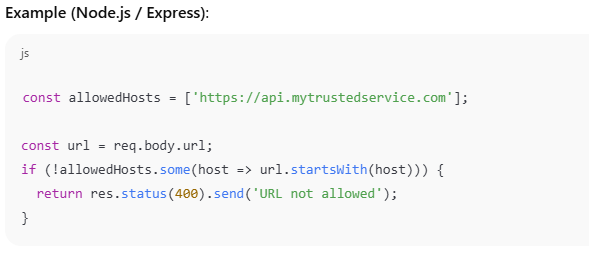
2. Avoid Direct Use of User Input in HTTP Requests
Block:- 127.0.0.1, localhost
- Private IPs: 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16
- AWS/GCP metadata services: 169.254.169.254
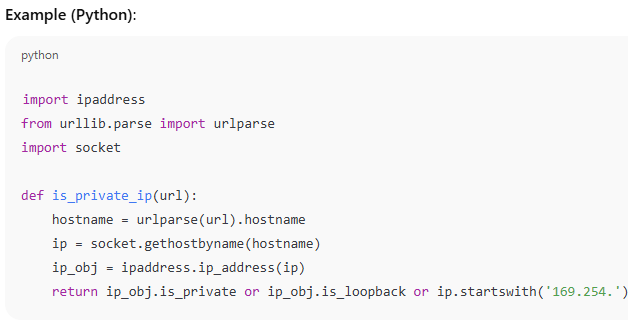
3. Use a Network Firewall / egress filtering
- Deny the web app from accessing the internal network unless explicitly needed.
- Example: AWS Security Groups, Docker --network=none.
4. Enforce DNS Rebinding Protections
- Perform DNS resolution and validate IP against blocklists.
- Re-validate after redirection (e.g., avoid redirecting to internal IPs).