Sensitive Information Exposure via System Logs (Logcat Leakage)
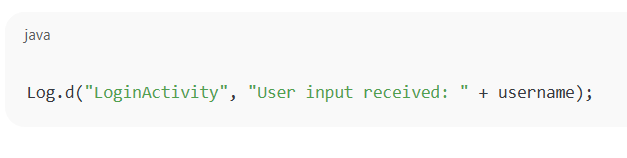
This vulnerability occurs when an app logs sensitive information; such as usernames, passwords, tokens, API responses, or personal data; using methods like Log.d(), Log.e(), or Log.i() in Android. On rooted or debug-enabled devices, other apps can access these logs. If the device is compromised or stolen, attackers can extract the logged data. Even harmless-looking logs might reveal backend details, authentication headers, or user-specific debug info. Since logs stay on the device for some time, they pose a serious risk, especially in production environments.
Vulnerability Impact
This vulnerability can expose personal information, login credentials, or session tokens, and allow unauthorized access to backend systems. The risk is higher if the device is rooted, infected, or lost, and it may also violate security policies or privacy laws like GDPR or HIPAA.

Vulnerability Solution
- Avoid logging sensitive data such as passwords, tokens, payment info, or personal user details, and be cautious when logging API responses or user-related content.
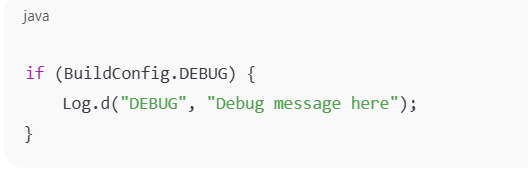
- se logs only for debugging (not in production) Log only in debug mode using a condition like
- if logging is necessary, always mask or hide sensitive parts