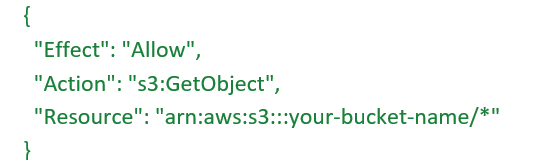
S3 buckets are exposed externally without any authorization or authentication.
Amazon S3 buckets are cloud storage units that can hold files, images, documents, etc. This vulnerability happens when a bucket is made publicly accessible without any authentication or authorization, either due to:
- Misconfigured bucket policies
- Misused ACLs (Access Control Lists)
- Public access settings turned ON
If anyone with a browser or a script can access your S3 files, your bucket is exposed.
Impact of the Vulnerability
- Sensitive data leaks – credentials, logs, source code, PII
- Data destruction – if write permissions are enabled
- Ransom or defacement of publicly available assets
- Violations of compliance standards like GDPR, HIPAA, PCI-DSS

Solution to Fix the vulnerability
1. Disable Public Access at Bucket Level
Go to AWS Console → S3 → [Your Bucket] → PermissionsTurn off all “Public access” options.

2. Use Bucket Policies to Explicitly Deny Public Access
This prevents all users (even anonymous) from reading the bucket files unless over HTTPS and via authenticated requests.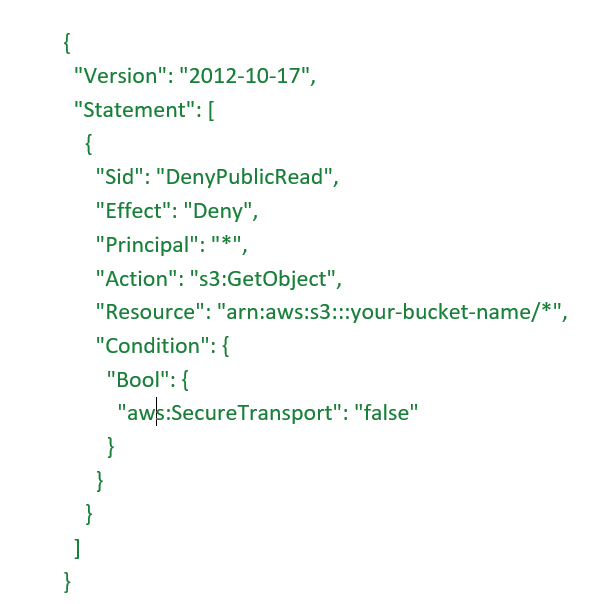
3. Audit and Remove Public ACLs
aws s3api get-bucket-acl --bucket your-bucket-nameLook for below and If found, remove it:

4. Use IAM Roles Instead of Public Access
- Give access to specific users, apps, or services
- Use IAM Roles with tight permissions (least privilege)