OS Command Injection Vulnerability & Its Fixation
When an application sends untrusted user input to a system shell (such as bash, sh, or cmd) without adequate validation or sanitization, it creates a critical security flaw known as OS Command Injection. Attackers can insert extra commands that the operating system will run if user-controlled input is directly included in a command string that is run by functions like system(), exec(), popen(), or backticks.
Example of vulnerable code in python:
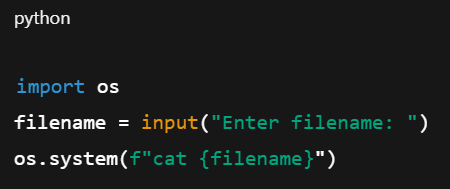
If a user inputs:
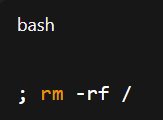
The resulting command becomes:
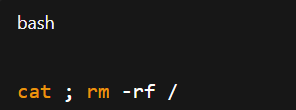
This allows the attacker to run arbitrary system commands — in this case, potentially deleting all files on the server.
Impact of the Vulnerability
Because it gives attackers direct access to the host operating system, frequently with the same privileges as the web server or backend application, OS Command Injection is extremely dangerous. Possible repercussions:
Arbitrary command execution:
Attackers have the ability to install malware, read, write, or remove files, and open reverse shells through arbitrary command execution.
Privilege Escalation:
The system as a whole may be compromised if the program is executed with elevated privileges (such as root/admin).
Data Breach:
Database dumps, credentials, logs, and environment variables are examples of sensitive data that can be exfiltrated.
Denial of Service (DoS):
Attackers have the ability to erase important files or overload system resources.
Persistence and Lateral Movement:
Attacks on other internal systems can be launched from compromised systems.
Solution to fix the Vulnerability:
Mitigating OS Command Injection involves strict input handling, avoiding unsafe execution methods, and using secure alternatives wherever possible.
Avoid Using Shell Execution:
- Do not invoke shell commands directly using untrusted user input.
- Use built-in functions or libraries instead of shell commands.
- Bad
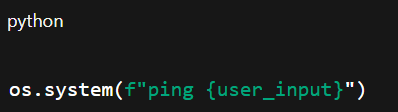
- Better alternative (In python):
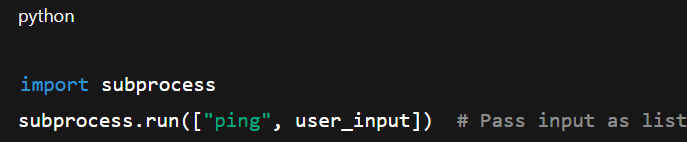
Use Parameterized APIs and Libraries:
- Always use language-native libraries or functions that do not invoke shell interpreters.
- These APIs treat inputs as data, not executable code.
Validate and Sanitize Input:
- Whitelist allowed characters or patterns. For example, only allow alphanumeric filenames or domain names.
- Reject input with special characters like ;, &, |, >, etc.
Apply Principle of Least Privilege:
- Ensure the application runs with minimal OS permissions.
- Even if compromised, an attacker should have limited access.
Use Web Application Firewalls (WAF):
- Deploy a WAF to detect and block typical command injection payloads.
- While not a replacement for secure coding, it adds an extra layer of defense.

