HTTP HEAD method is found to be enabled.
The HTTP HEAD method is similar to a GET request but only retrieves the headers (no body). While it's designed for lightweight checks (like validating links or resources), if left enabled, especially on sensitive endpoints, it can:
- Reveal server details
- Allow attackers to enumerate valid endpoints
- Bypass security filters designed for GET/POST

Impact of the Vulnerability
- Information Disclosure: Headers may reveal framework versions, tech stack, or other fingerprinting data.
- Attack Surface Expansion: HEAD method might behave differently than GET in certain misconfigured apps.
- Security Evasion: HEAD is less logged, giving attackers a stealthier way to map your app.
Solution is to Disable HTTP HEAD Method
Disabling the HTTP HEAD method is recommended to reduce your server’s attack surface. Here’s how to disable or restrict the HTTP HEAD method across various web servers and platforms:
-
Apache HTTP Server (httpd)
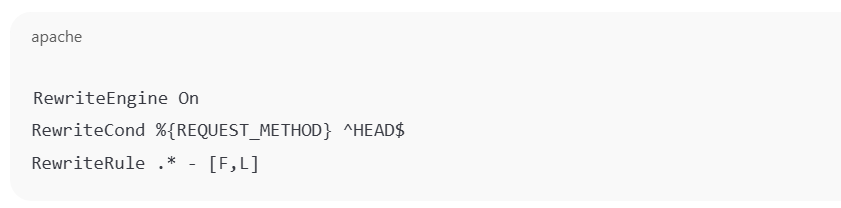
- Option A: Disable HEAD via mod_rewritE
- Add this to your .htaccess file or inside your Apache config (e.g., httpd.conf, virtualhost block).
- Option B: Disable All Methods Except GET/POST
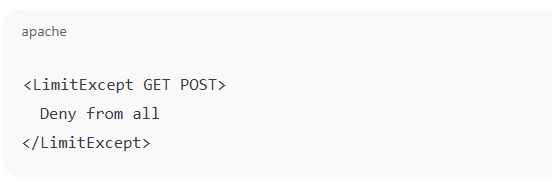
-
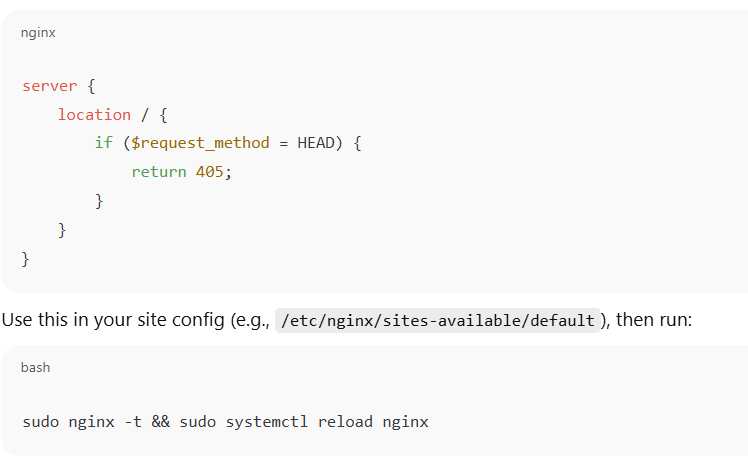
Nginx
- Nginx treats HEAD as implicit (handled like GET without a body), so it can’t be disabled directly. But you can explicitly block it like this:
-
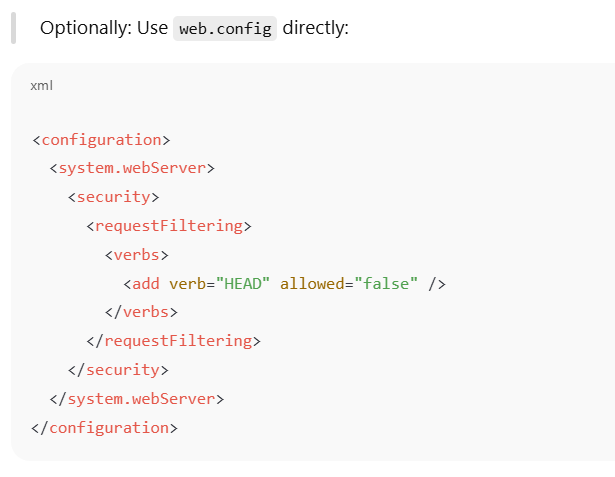
Microsoft IIS
- Steps to block HEAD method:
- 1. Open IIS Manager.
- 2. Select your site.
- 3. Go to Request Filtering.
- 4. In the HTTP Verbs tab, click “Deny Verb...”
- 5. Enter: HEAD
- 6. Click OK and restart IIS.
-
Tomcat (Java Web Apps)
- Tomcat uses HTTP methods as implemented by your servlets.
- To block HEAD in web.xml:
- Or, in your servlet code:
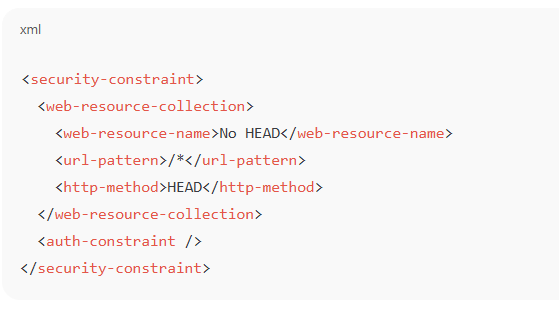
-
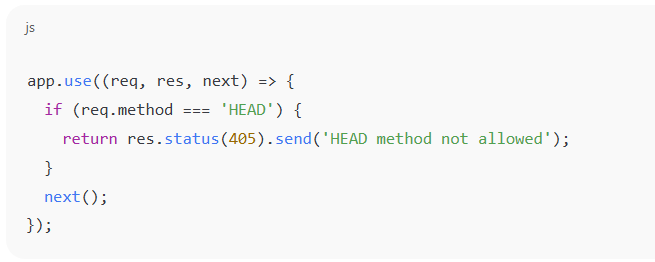
Express.js (Node.js)
- Manually handle or block HEAD: