Formula Injection: When Spreadsheets Turn Against You
When an application exports user-controllable data into spreadsheet formats (such as.csv or.xls) without sanitizing inputs, it is referred to as formula injection, CSV injection, or Excel injection. Certain characters (=, +, -, or @) at the start of a cell are treated as formulas by spreadsheet programs like Google Sheets and Microsoft Excel.
An attacker can run undesired commands or payloads if they add formula syntax to fields like name, email, or address and then export and open the data in a spreadsheet program. This gets risky when:
-
Spreadsheet functions like =HYPERLINK("http://malicious.site") are injected by the attacker.
-
Alternatively, in older or incorrectly configured environments, malicious scripts such as =CMD|' /C calc'!A0
Example:
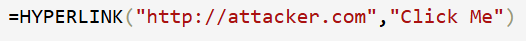
When the application admin downloads and opens user data in Excel, the formula executes as a hyperlink — potentially leading to phishing or malware download.

Impact of the Vulnerability
Although Formula Injection may not directly target the web application or server, its true impact is felt by users, frequently those working in internal systems or handling exported data.
What can go wrong is as follows:
- Phishing attacks: Infected formulas can produce links that appear to be innocuous but actually point to dangerous websites.
- Command execution: Payloads may occasionally use Excel macros to initiate system commands.
- Data exfiltration: Spreadsheet data can be sent by scripts to a server under the control of an attacker.
- Credential theft: Users may be tricked into entering their credentials into phoney login prompts by a deceptively disguised formula.
- Supply chain risk: Inaccurate information in shared reports has the potential to spread throughout organizations or departments.
The risk is in the degree of trustworthiness of exported spreadsheets. Because employees might not anticipate being compromised, this attack is particularly successful.
Solution to Fix the Vulnerability
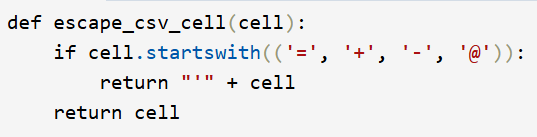
1) Escape Dangerous Character:
-
Prepend a single quote (') to any cell starting with one of the following characters: =, +, -, or @.
-
This prevents the spreadsheet application from treating the input as a formula, rendering it as plain text instead.
2) Make Use of Reliable Libraries:
Use libraries with built-in escaping/sanitization when creating CSV or Excel files. For instance:
- Python: pandas.to_csv() (with sanitisation logic), csv
- Node.js: xlsx (manually escape), csv-writer
- Java: Apache POI (use escaping prior to assigning cells).
3) Verify and Clean the Input:
Make sure that when entering data, inputs are verified. Inputs that appear suspicious or contain formula characters in fields you didn't intend to use should be rejected or flagged.

