DAR Vulnerability: Android:Debuggable set to true
This vulnerability happens when the android:debuggable flag is manually set to true in AndroidManifest.xml. This lets attackers inspect internal processes, access sensitive data, modify app logic, and reverse engineer the app.
Normally, the Android build system sets this flag automatically: true for debug builds and false for release builds. Manually setting it to true overrides this default and creates serious security risks.
If debuggable is true, attackers can:
- Use Android Debug Bridge (ADB) to connect to your app
- Bypass app protections
- Extract sensitive data
- Use reverse engineering tools more easily

Fixation Steps
1. Ensure android:debuggable is false (or not set) in AndroidManifest.xml
In AndroidManifest.xml, check for:

Remove the android:debuggable attribute entirely (best practice), OR Set it to false:
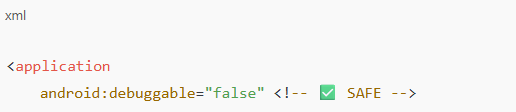
Note: If omitted, the build system automatically sets it based on the build type (debug vs. release).
2. Confirm release build is used when generating APK or AAB
In build.gradle:
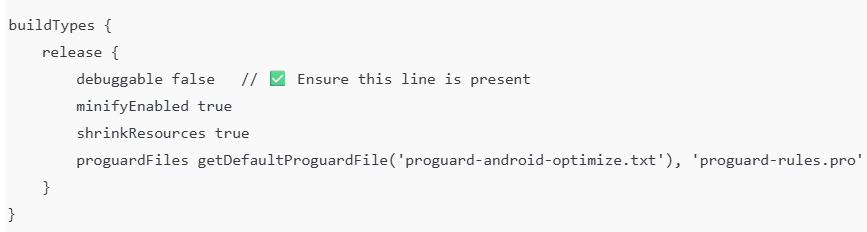
3. Verify build type before publishing
Build the app using:
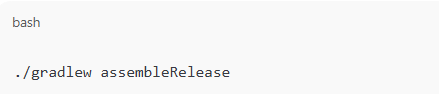
And sign with your production keystore. Avoid using debug builds.

