Avoid Storing Sensitive Data in Plaintext on Android Devices
In Android development, storing user data locally is common—but if done carelessly, it can open the door to data leakage, identity theft, and legal violations. One of the most overlooked yet dangerous practices is storing sensitive information in plaintext—especially in areas that persist even after app uninstallation. Let’s break down why this is a risk and how you can fix it.
What’s the Risk?
- Plaintext storage (e.g., in files or shared preferences) means that no encryption is used, making it easy for attackers or malware to read the data.
- If stored in external storage (/sdcard, getExternalStorageDirectory()), files can persist even after the app is uninstalled.
- These files are accessible by other apps, including malicious ones.
- This can lead to:
- Data leakage
- Identity theft
- Regulatory violations (e.g., GDPR, HIPAA)
Solution: How to Fix It
1. Store Data in Internal Storage
Use internal storage (private to your app) via: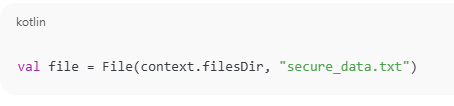 This location is:
This location is:
- Not accessible by other apps
- Automatically deleted when the app is uninstalled
2. Encrypt Sensitive Data
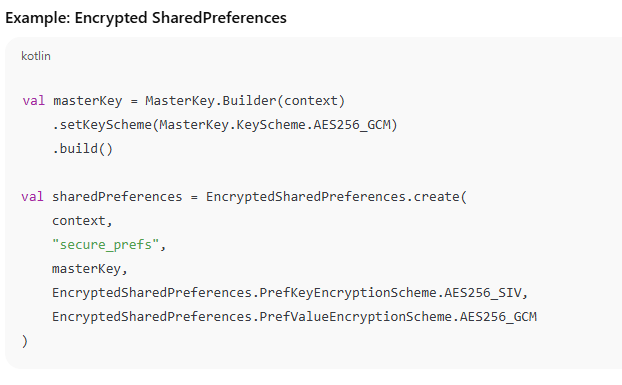
Before saving any sensitive data (e.g., tokens, credentials, personal info):- Use Android Keystore for encryption keys
- Encrypt data using AES or EncryptedSharedPreferences:
3. Avoid External Storage for Sensitive Data
Do not store sensitive information in:- getExternalFilesDir()
- /sdcard/
- Any public folder (Downloads, Documents, etc.)
- Are shared across apps
- Persist after uninstall
- Are vulnerable to tampering or theft

