Backups enabled in AndroidManifest.xml
Vulnerability Title
The android:allowBackup attribute is enabled in the AndroidManifest.xml, which allows app data to be backed up. This can lead to potential data theft through local attacks using tools like adb backup, particularly if USB debugging is enabled on the device.

Vulnerability Explanation
This vulnerability occurs when the android:allowBackup attribute in the AndroidManifest.xml is set to true or left unspecified (as it defaults to true). This allows the application’s data to be backed up and restored using tools like adb backup, which can be exploited on a device with USB debugging enabled.
Attackers with physical access to the device or access over ADB can extract sensitive data stored in the app's private storage; such as user credentials, tokens, databases, and cached files; especially if proper encryption is not enforced.
Vulnerability Impact
Enabling backup makes it easier for attackers to steal app data through local attacks (ex., using ADB commands). This can lead to exposure of sensitive information, bypassing of in-app protections, and potential user data leakage, especially on rooted or debug-enabled devices.
Vulnerability Solution
-
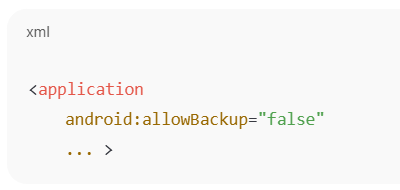
Disable backup in production apps. Explicitly set android:allowBackup="false" in the application tag of your AndroidManifest.xml to prevent backup of app data.
- Even if backups are disabled, always store sensitive data securely using encrypted shared preferences, encrypted databases (like SQLCipher), or Android Keystore.
- Ensure USB debugging is disabled on production/test devices or require authentication for access.


