Securing Xen Virtualization
The concept of virtualization was created in IT industry to achieve easy management and maintenance of the server infrastructure. While there are many production environments running on robust virtual servers, there are underlying security challenges which should be carefully addressed while designing virtualization solutions.
This article talks about a Xen virtualization solution and also explains the measures to make it cyber secure. Network administrators are urged to learn these techniques to protect their virtual server infrastructure.
Virtualization
Simply put, a virtual server is an instance of operating system, which shares system resources such as CPU time, memory to simulate a computer machine. At the heart of operating system lies a component called as HAL (hardware abstraction layer), which converts CPU instruction set into meaningful operating system calls, which are further used by high level application layer. Virtualization is a software layer that runs along with the HAL and operating system, to allow creation of machine instances called as guest systems. Guest systems which are simulating a computer are capable of running any operating system such as windows, Linux etc. This becomes possible because each instance owns a configurable amount of CPU time and memory resources. Thus on a powerful physical machine, multiple varieties of guest operating systems can run in parallel. This is similar to an operating system running several applications in multi-tasking mode, with a difference that in this case several operating systems are running using a shared CPU model in a multi-threading mode.
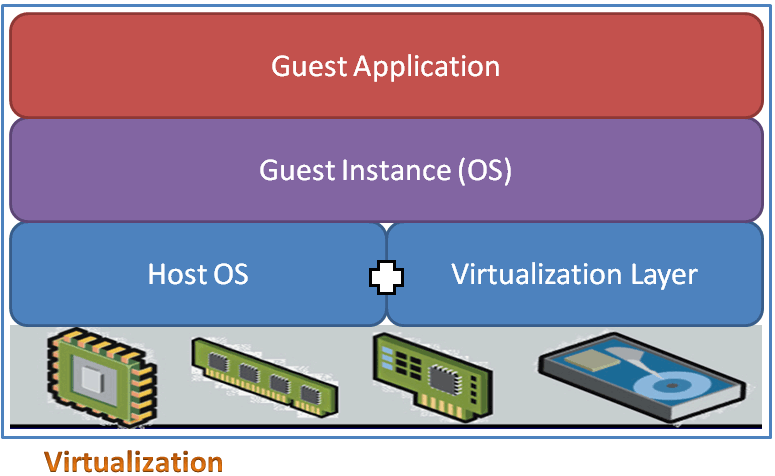
Fig 1. shows typical virtualization architecture. It is important to note that, other than just the CPU and memory resource sharing, the peripherals such as CDROM, USB ports are shared too. The most important component being shared is network interface card. Typically in a physical server hosting virtual guests, two or more network cards are hosted which are shared in a teaming mode, to provide redundancy if one interface fails. It is also important to note here, that a virtual session manager is running in parallel, to keep track of all guest instances, and hence consumes some amount of systems resources too. There are three high level types of virtualization. The first being full virtualization also called as hypervisor, wherein all guest instances are kept separate from each other.
In the second type called as para-virtualization, the guest systems know about each other, which is achieved by semi-abstraction of physical and OS layers. The benefit in this method is that it takes lesser toll on the system resources to result into faster guests, but compromises on the security. The third type is called as OS level virtualization in which the abstraction layer simulates multiple instances of the host OS. In this method, a variety of operating systems are not possible to be hosted. Hypervisor is the most commonly used method, and is not only limited to servers but also to networks, desktops, storage networks, applications and databases.
The main purpose behind virtualization is to reduce hardware costs and take maximum benefit out of the hardware investment thus increasing ROI (returns on investment). It is also observed that modern data centers are using virtualization to reduce real estate costs, as well as to reduce heat emission from the infrastructure, in order to form eco-friendly (green) data center. While there are multiple advantages of virtualization, this technology is cursed too with the cyber security problems observed in physical infrastructures. We will now learn about a famous open source virtualization solution and then discuss various security challenges.
Xen Open Source Virtualization
We chose Xen platform as an example for this article solely because it is a famous and versatile solution, which is being used by major cloud hosting players such as Amazon. It is a highly scalable platform which can result into multiplying the given physical hardware into powerful virtual instances, and is also backed by industry leaders' open source communities in terms of support and solution engineering.
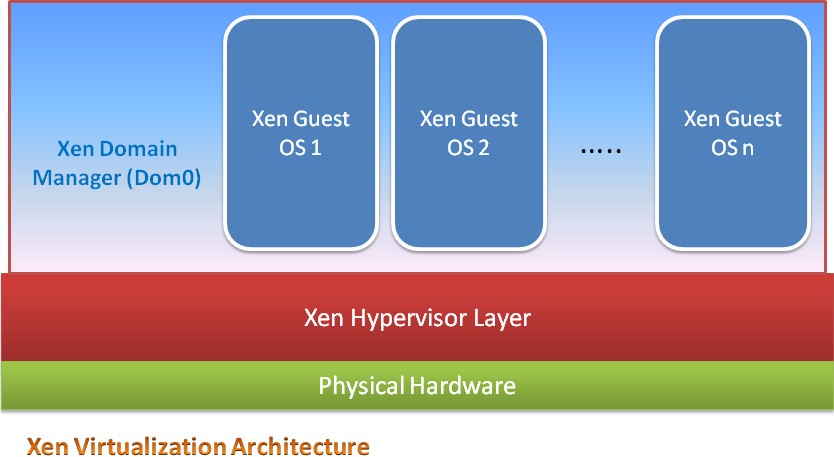
Speaking technically, Xen virtualization has a hypervisor component at its heart, which is a software layer that runs between physical hardware and the operating system to be able to create multiple guest instances. This layer also distributes and schedules the CPU time, partitions memory spaces, and performs a seamless process multiplexing. As shown in Fig 2., Xen architecture contains 3 components, the hypervisor layer, domain manager and guest instances.
Xen domain manager is a kernel component which gets installed as first domain and it is a virtual instance by itself. It has special and elevated rights and access to the physical resources. Domain manager runs before any other guest instance can be started, and provides functions such as allowing creation of child domains, creating and managing virtual devices for guest domains and also to control network and disk resources to give justice to the guest instances in terms of resource utilization. Guest instances, also called as underprivileged DomainU components, are not allowed to access hardware resources directly. Guests communicate to domain manager through proxy calls to ask for access, and also keep the manager posted about their online or offline status. As for the benefits, besides saving cost, the virtualization solutions are used as a sand box to test the software code before it is deployed into production environment. Xen is also effective for server migrations wherein the virtual server is simply copied over to another powerful physical hardware platform, where it works without a glitch.
Securing Xen
As mentioned earlier, though the Xen virtualization brings lot of benefits, it can be susceptible to cyber security challenges if the hypervisor technology is not carefully studied. It is very important to keep in mind, that virtualization is a software component and can be affected by programmatic as well as man-made cyber attacks, just as any physical server infrastructure. In fact it is observed that virtualization brings more security challenges that physical hardware, we will learn these reasons below.
Hypervisor security
Since this is a layer sitting between physical hardware and the operating system, it is bound to have vulnerabilities which can directly impact the security. Like most of the operating system patches, Xen platform timely provides service patch updates and security hot fixes to repair the bugs or vulnerabilities respectively. The same goes for domain manager too. During the installation phase, a tested and well written security patching process needs to be put in place, to ensure continuous security improvement.
Guest OS security
From a system administrator's point of view, the virtual machines are pretty much the same as physical servers. Careful configuration and regular patching is essential for the Xen DomainU instances running the operating systems installed on them. The correct way to achieve this is to follow the OS hardening guide for the particular OS being used. This applies to the applications installed on each guest as well. It is important to remember that one vulnerable machine in a virtual environment can act as the weakest link from security standpoint and malwares and viruses can spread to other guest instances resulting into a wider security problem.
Guest communication security
Unlike physical servers where the TCPIP communication between hosts can be sniffed and captured to detect security attacks, virtual machines' communication cannot be visible on the physical network interface. This happens because the network interface card is actually being abstracted by the Xen hypervisor layer. As a result, traditional intrusion detection systems fail to detect vulnerability exploitations happening within virtual machines. A correct way to resolve this situation is to have one guest virtual machine dedicated to the sniffing purpose, for all the other instances on that physical host. The data gathered thus, can be fed into an IDS system to find out potential exploitations.
Host External communication security
The physical machine hosting multiple Xen guests, is going to be susceptible to network Layer-2 to Layer-7 based attacks such as eavesdropping and man-in-the-middle attacks etc. Implementing security solutions for the corresponding network layers such as IPSec, SSL etc is always a good idea. Implementing firewalls and UTL devices to ensure perimeter defense for a physical host is required.
Besides these there are few challenges which are worth noting. During an installation phase, it is common to have virtual guest instances created for testing purpose which are later forgotten to be removed. Such instances are usually not patched and hence become a source for vulnerabilities or a weakest link. It is a best practice to delete such instances by using Xen configuration manager. Since various guests may be running different versions and flavors of operating systems, a unified patch management solution which can deal with multiple distros is highly recommended. The same goes true for the antivirus software. Virtual infrastructure calls for a tighter physical security as well, because in a very rare situation if a physical host is stolen, it is effectively loosing multiple servers.
Summary
While securing a virtualization platform such as Xen, emphasize should be first given on the concepts of guest instances and how those work with the physical host. Most of the security challenges in Xen can be mitigated with a proper configuration management, deployment of best practices and security patching. It is important for network administrators in the modern world to know about various open source virtualization platforms and the methods to secure their environments.

