Cyber Attacks Wireless Attacks
Wireless networks are everywhere, from home to corporate data centers. They make our lives easy by avoiding bulky cables and related problems, while ensuring seamless connectivity of network nodes. As it is a benefit, there is certainly a threat which comes along with that.
Wireless networks are prone to security attacks and we are going to learn about it in this article. We will also discuss few techniques to protect FOSS networks, which must be implemented by system administrators to achieve adequate security.
How Wi-Fi Works?
Before we talk about wireless security and vulnerability attacks, we must understand the basic radio transmissions and the IEEE 802.11 protocol, also commonly known as WLAN protocol. This protocol links two or more devices over a short distance, using spread spectrum signals. Spread spectrum at its core, is based on radio communication frequencies to establish a point to point wireless communication between a transmitter and a receiver, while achieving resistance to signal jamming and signal fading.
As shown in Fig 1., to establish a wireless network, you need a wireless access point and also a wireless adapter for each node to be connected. The access point is also called as a hot-spot and it hosts a radio transmitter and receiver very similar to a walkie-talkie unit. It also contains necessary hardware to convert digital data into radio signals and vice-a-versa.
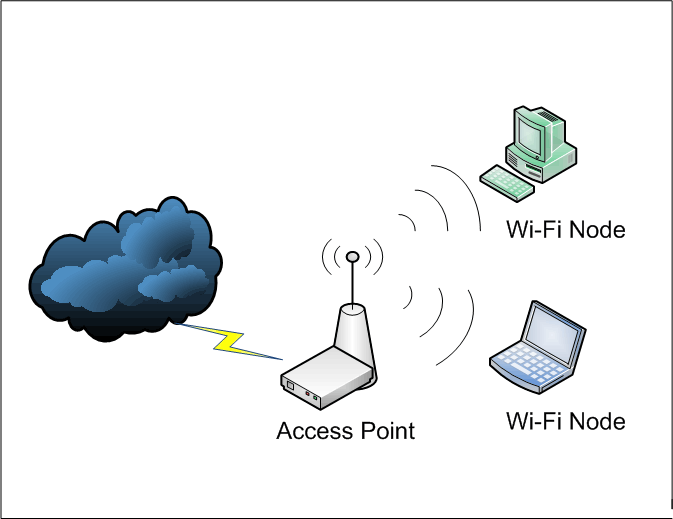
The access point has a unique feature called as a beacon transmission, whereby it keeps on sending a digitized signal on wireless radio spectrum, typically few times every second. This signal contains the network identification; the service set identifier (SSID),and some trivial error correction information. The node such as a laptop or any wireless device, detects this signal in order to show it in the list of available wireless networks. It also detects whether or not the access point is using any security, and what level of security protocol etc. The access point contains TCPIP stack which responds to ARP requests when a node tries to connect to it. Since wireless can allow multiple nodes at any instance, it is essential to have an authentication layer prior to letting the data transfer take place. It is the responsibility of the access point to ensure this security and monitor the packet transmission and data integrity.
Wi-Fi Security
Since the wireless networks don't have built-in security mechanisms, a secure layer on top of the wireless protocol stack. This is achieved by encryption and authentication techniques such as WEP (Wired Equivalent Privacy) or WPA (Wi-Fi Protected Access). This is especially important because unlike a wired network, wireless signals can be easily intercepted using a signal trapping device. Let's discuss how these encryption techniques work in bit of details. To establish a secure channel, the client first sends an authentication request to the access point, and receives a challenge from it in text form. Client machine encrypts this text using the preconfigured key and sends it back. Access point decrypts it and upon success it replies back to the client. If the keys don't match, the request is dropped and client cannot connect to the access point. This method is called as a pre-shared authentication. In an improved version, the shared key is combined with SSID of the wireless access point, to further toughen the encryption key logic. The WEP encryption uses RC4 algorithm to all packets as those travel between the access point and the node.
Unfortunately these security mechanisms are either flawed by design, or those are certainly not adequate for IT infrastructures, where the data being carried by wireless channels is of sensitive nature. With this basic understanding of Wi-Fi security, let us now discuss few security attacks. In general there are four categories of possible wireless attacks.
Passive attacks - In this type the attacker listens or eavesdrops on an open wireless channel by using a wireless modem rigged to work in a promiscuous mode. All traffic packets are stored which contain important information such as MAC addresses, packet sequences etc. Passive attacks may not necessarily be malicious in nature, but those in fact help provide information to the active attacks. Since passive attacks take place silently, those are almost impossible to detect and stop. Attackers using passive methods usually capture and store data, and use a packet deciphering tool to decrypt it, and steal information. This is especially true in case of WEP protocol due to its inherent in-security. Passive attacks are also called as wireless war driving.
Active attacks
Using passive attacks, once the sufficient information is gathered by attacker, an active attack can be planted on a network. The common examples are denial of service attack, IP spoofing etc. In case of spoofing, the attacker gains access to an unauthorized wireless station, and performs packet crafting to impersonate as a valid and authorized station. The wireless nodes are incapable of detecting this and end up connecting to attacker's station and thus revealing the information. By extending this technique further, the attacker can now plant a denial of service attack on a particular node in order to disrupt its services. Typically a SYN flood method is used because it is sufficient enough to generate a packet storm on the given wireless connection bandwidth.
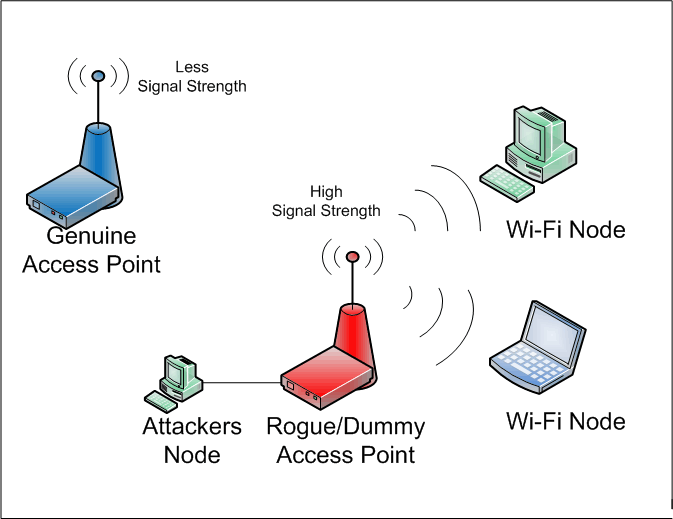
MITM attack
We have learnt man in the middle (MITM) attack in one of the previous articles, and it's no different in case of wireless networks. The only technical difference here is that the attacker gains information of an actively used SSID of an access point, instead of an on-the-wire session. As shown in Fig 2., a dummy access point with exactly the same name is created by attacker, and the signal power is raised to such an extent that the wireless nodes are fooled to believe that it is the access point to which they should connect to, thus creating a man in the middle situation. These dummy access points, also called as rogue points, are usually setup in a close proximity of the nodes to be hacked.
Signal Jamming attacks
Unlike the above techniques, this method uses wireless radio transmission techniques to create an attack. In this type, the attacker uses a powerful antenna and a signal generator, and creates frequency patterns in the range same as wireless signals. The frequency patterns are modulated with powerful radio frequency ripples, to create a wireless signal storm. This results in the jamming the access points as well as the nodes, thus disabling their connectivity. While such an attack was just a theory previously, with a growing number of wireless networks, these attacks are found more often that earlier.
Besides these, there are few other types, which make use of one or more types of the attacks mentioned above.
802.11 Injection attacks
Modern attacker are found to go deep below in the protocol stack in order to plant an attack. For wireless networks, an attacker can first perform a passive attack to understand the protocol frame structure, and then create 802.11 protocol datagram frames and insert those into the network. This is usually done either to create a false packet stream to create hindrance into a wireless network, or to sniff the network further, in an active mode. The response 802.11 frames are then captured again, interpreted and modified to perform a man in the middle attack. Since this attack happens at Layer-2, it is very tough to detect it.Wireless packet injection
Attackers use passive attacks to capture the traffic which is then analyzed. However there can be situations where there won't be enough traffic to generate sufficient data traffic, which can lead to time consuming or futile hacking efforts. Hence the attackers use wireless packet injection techniques whereby besides the 802.11 frames, IP datagram are sent to the target access point. Though the access point is going to drop such packets as being unauthorized, this gives attacker the necessary amount of traffic which is captured and fed into the key cracking utilities. Since attacker is in control of the packet generator utility, specific data patterns are intentionally created to map the access point's behavior in terms of response packets, which further helps in reducing the cracking time.PSK Guessing
As we learnt earlier, a pre-shared key is used between wireless access point and the node to encrypt the communication. Typically the administrators setting up Wi-Fi networks tend to leave the vendor provided default key in place. Smart attackers usually try first to detect the manufacturer of wireless access points, and if that information is not available, they try to guess it and attempt to break the key.Key cracking
Usually a pre-shared key should be enough to establish the security. However in case of WEP base Wi-Fi networks, the attackers can use passive method to sniff and capture lot of data packets and subject it to key cracking algorithms. As we saw earlier, the WEP is a simple RC4 XOR type of encryption, and it only takes some amount of time to break into it. It had been demonstrated by attackers that a packet capture of more than 40000 can result into sufficient data, to crack a WEP key in minutes. With the introduction of WPA security features in a wireless access point, it became tough to break the key. However other brute force attacks such as statistical key guessing, dictionary attacks etc can be used to crack it.Wireless Attack Detection
Before we talk about protecting the infrastructure, it is imperative to understand few detection techniques. Unlike the wired networks, a wireless network signal can be compromised easily which makes the detection difficult but certainly not impossible.
Access point monitoring
As we learnt, securing the SSID of an access point or wireless router is very important. In a large organization, keeping track of SSID can be a challenge; hence programmatically this information should be stored in a secure database. Other crucial details such as the MAC ID, the IP restrictions, the wireless channel used, the beacon settings, wireless signal strength and bandwidth type etc. are stored for each corresponding SSID. A wireless monitoring device or a mobile device running monitoring software is used to detect all stations and access point periodically, and are compared with the baseline database created earlier. Such a routine check audits ensure integrity of the router settings and thus the overall wireless network security.Wi-Fi node monitoring
Along with the access points, each node needs to be monitored too. The technique is bit different though. For the nodes, a MAC based security on the access points can be configured whereby a particular access point would support only a set of MAC addresses. This ensures that the wireless client node cannot roam around beyond the configured zone, and if such a need arise, the request can be fulfilled via an authorization and approval process. For large organizations, this can result into a system administration overhead, in which case the nodes can be allowed to connect to all access points; however each of those connections and disconnection can be logged and parsed for anomalous behavior.Traffic monitoring
Besides above techniques, network administrators can periodically take samples of data from each access point and check those for denial of service and SYN flood attacks. Multiple connections and disconnection on a particular access point from one or more client nodes should also trigger a warning. As for Layer-2 attacks, a signal spectrum detection tool can be incorporated too, to detect signal jamming situations.Protecting FOSS systems
Along with the monitoring techniques, additional measures of security are essential for wireless networks. For small networks, changing the default password and SSID of the access point is a must. Modern routers are equipped with a feature to disable the broadcasting of SSID, which should be turned on to ensure that the sniffing passive attacks are thwarted to some extent. Periodically changing SSID is highly recommended though it can be a tough task for large number of wireless access points. To protect a Linux server farm hosted in a datacenter, the wireless signal strength of access points should be adjusted in such a way that, it should be adequate for client nodes to connect and transfer data seamlessly, and at the same time it should not cross physical building boundaries whereby it can be detected by a "drive-by" attacker.
Using WPA2 security instead of WEP is recommended. Furthermore, the shared key of WPA security should be long and complex enough to stop the directory brute force attacks. For large corporations, the Layer-7 wireless security software should be installed on client nodes as well as access points to further strengthen the encryption process. For FOSS systems, using an X.509 certificate on the either ends of wireless communication can help achieve cheaper yet effective security. Most famous flavors such as Dabien and Ubuntu distros support WPA2 security with security trimmings such as AES, TKIP and LEAP. Configuring those along with the MAC address filtering and enabling the firewall features can protect a serious server farm, yet enjoying the benefits of wireless networks.
Summary
Wireless attacks are unfortunately an easy type and is difficult to detect. Modern data centers allow presence of wireless networks connected to the product server farms, thus needing implementation of security measures. While there is no single solution to protect wireless networks, an appropriate combination of techniques mentioned above can achieve adequate security. Wireless monitoring audit is important activity to be followed by network administrators at regular intervals.

