Cyber Attacks Botnets
This month we are going to learn about yet another dangerous type of attack which is prevailing even in the modern computer systems. The attacks covered so far in the previous articles were based on exploiting technical vulnerabilities to steal data or destroy data.
Botnet attack is of an advanced type whereby the attacked computer system becomes an attacker itself. This causes serious concerns in the IT world which should be known to every system administrator and senior technology management. We will also discuss how FOSS systems should be protected by such an attack.
Botnets
The word botnet is derived from the phrase "network of robots". It is essentially a widespread collection of a large number of infected computer systems. Each infected system runs a piece of software program called as a "Bot".
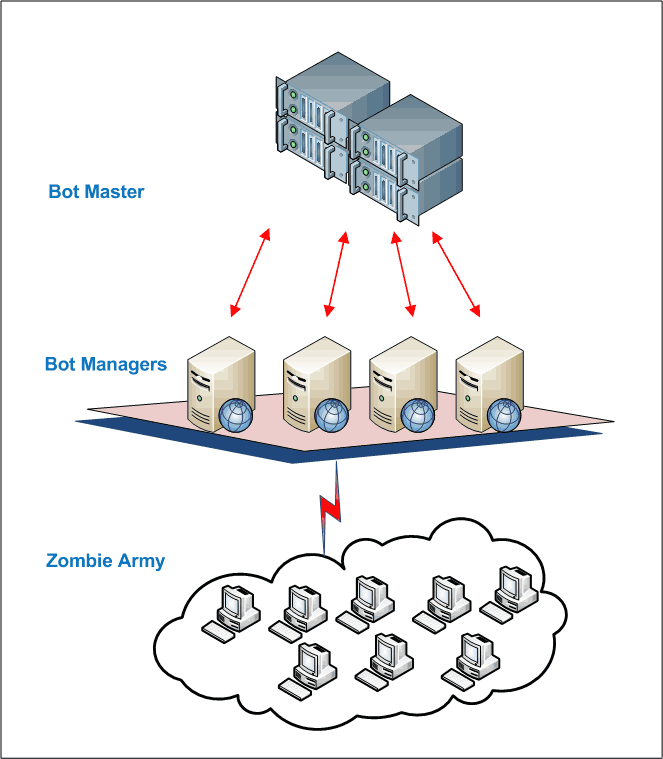
As shown in Figure 1., there is a Bot-Master system which keeps a track of total number of machines infected and the tasks they should perform. For carefully choreographed systems, which need orchestration between millions of such systems, another layer of Bot-Managers is created too. Bot-Managers perform the tasks to accept commands from the master, to spread out those commands to the bots and also to report the number of systems infected under its jurisdiction. The manager botnets are also found to be sending updated software patches to fix bugs or improve functionality, very similar to a security patch management system. The Bot-Master is in control of the hacker who has evil intentions to create this army. However since the hacker is supposed to be hiding from getting caught, the master systems and software running on it are always operating in a stealth mode. In few modern botnet attacks, the botmasters were found to delegate and rotate the master's role between its botmanagers, thus making it extremely tough to detect. These role changes were further found to be rotating their ownership based on the country of presence, in order to ensure vast infractions across the globe. Usually botnets are designed for a specific operating system, and if a wider spread has to be achieved, botnets prefer web code, or java language, to infect all the possible operating system platforms.
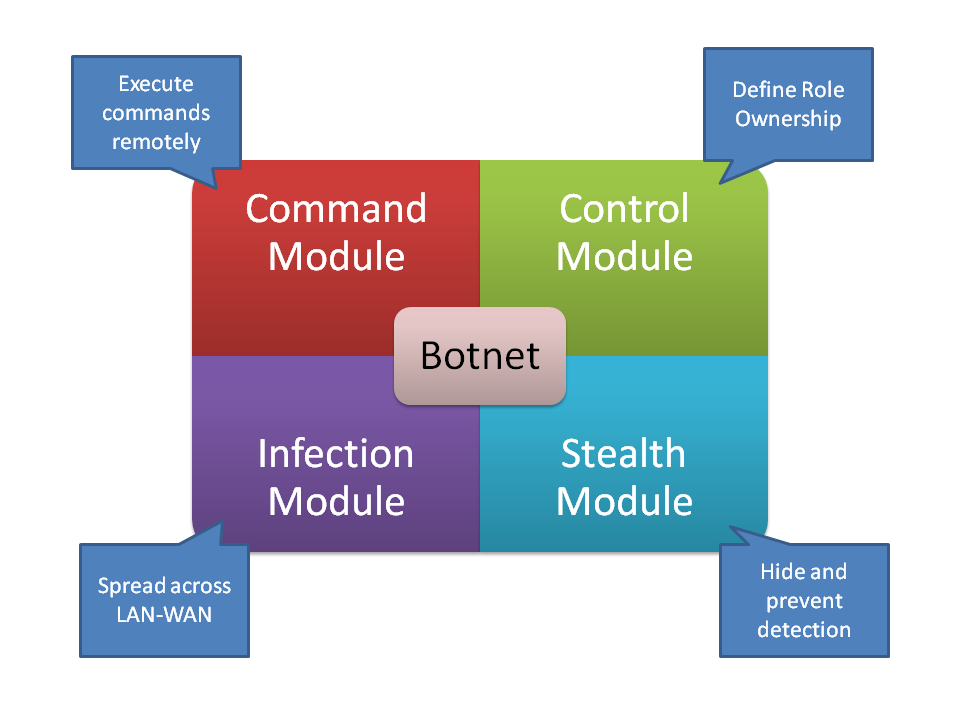
Now let's look into the internal operations of a typical Bot. As shown in Figure 2., there are 4 main modules of a botnet. Command module sends commands to the child botnets, whereas the control module controls the ownerships, to decide who should listen to whom. The infection module carries important responsibility of finding non-patched servers in the network and infecting those with the most updated copy. The stealth module is essentially a set of software programs which does the crucial job such as disabling antivirus; achieve root access or kernel access. It also ensures that its own footprint on the infected machine is invisible in terms of running processes and disk space, and also keeps a watch on new antivirus software being installed. In some cases, the stealth module and control module work together to fetch a most recent patch of itself from the master or manager, and seamlessly upgrades itself. Some stealth modules are also capable of erasing themselves using a self-destruct mechanism or shutdown the system, to thwart the aggressive detection techniques.
The way botnets interact with the master or manager is very interesting too. All bots are given a unique identification number, which is usually a product of the infected system's configuration and location, but not necessarily the ip address of the system. The master always has a most updated count of these identification numbers used, and is capable of limiting the spread or expand it. Bots use a specific range of TCP ports; however the exact port being used is picked up randomly. It is always the duty of the botnet itself to report the TCP port number it plans to use, to the master or manager. This reporting occurs upon every reboot of the infected system. In most cases the inter-Bot communications are base-64 or md5 encrypted, while in some cases a self signed digital certificate is found to be used too.
The main purpose behind injecting a botnet into a system is to create an army of infected systems, also called as zombie machines. The table below explains various types of botnets and the purpose behind injecting those into a network. The overall purpose behind such an attack is ultimately, to disrupt computer systems or to steal data. Since a whole army of computer zombies are in action, unfortunately the hacker can easily and quickly succeed in his evil mission, this is because planting a botnet attack is always a low risk, high profit job.
| Botnet Type | Purpose |
| DoSBot | DoS and Distributed DoS attack using Layer 3 to 7 protocols |
| SpamBot | Email spamming by collecting address books |
| BrowseBot | Gather user's browsing trends and feed into advertisement network |
| AdSenseBot | Same as BrowseBot but targeted to Google adsense |
| ChatBot | Collect chat transcripts to find user's chatting trends |
| idBot | Collect userid and password information |
| CCBot | Collect credit card information from e-commerce portal screens |
| PollBot | Manipulate online polls meant for products and services |
| BruteForceBot | Attack websites with TCP and application layer attacks |
| NetBot | Attack networks using Layer 2 and 3 protocols |
How Botnets are injected
In early days of internet, a botnet code piece was developed to programmatically traverse through multiple websites and to further gather and collate the contents to create meaningful data. While this method forms the heart of today's search engines, it was tweaked at some point in the past by hackers to their benefits. Before we talk about how botnets are injected, let's understand why it is done. To make a website famous in a search engine, it is imperative to get lots of web requests. This is especially true for websites which show advertisements and earn money for every click on a published advertisement. It is possible to spread botnets across the networks, to access the webpage and programmatically click one or more advertisements on it. If such a campaign is carefully orchestrated, it is tough to figure out which click is initiated by a human being legitimately, and which one is originating from a botnet code. The website hosting person, usually a hacker in such a case, can end up earning lots of money. In another variety called as phishbots, an email campaign can be started to achieve similar results. This tells us that the effects of botnet are beyond mere reputational or data loss.
Injecting a botnet is usually a very well thought and strategic approach taken by the hacker. The process usually starts by infecting one or more systems, these systems are then responsible to replicate the malicious code on to other machines and eventually cross the boundaries of the network to spread the infection to a wider and global area. In order to infect one system, the attacker needs to rely on multiple ways of intrusions. Very commonly used method is to lure a browser to a website hosted with malicious JavaScript code or a page written in similar low level scripting language such as python. This script is merely a bootstrap, which executes and creates a stealth resource space on the machine. The script then connects to one or more web pages of the same website, which contain the real payload of a botnet. The payload files are then downloaded and kept hidden under a stealth space. This payload contains all the modules explained above, which take control of the machine, and the machine can be said to be infected at this point. Enhanced botnets do not require the machine to be rebooted, and are capable of turning the machine into a zombie the moment those are downloaded. Another famous injection method is to put the botnet malicious code in the form of installable files on a USB drive, and inject the code on a machine which allows easy physical access and is vulnerable or insecure. There are few advanced methods such as forcing user to run a script sent as an attachment, or hide the code in a music file and distribute it using peer to peer shares.
The process mentioned above is usually possible when enough security measures are not in place. For example, a machine not running antivirus software, or running with stale antivirus definitions can fall prey easily. Similarly an un-patched or improperly patched system or network can expose a lot of vulnerabilities to be exploited. In case of network perimeter defense, leaving security holes in a firewall configuration help worsen the situation. As for servers, implementing insecure policies or measures which do not harden the server operating system or leaving application exploits unfixed, can cause the damage. While dealing with Linux distros, exploits such as buffer overflows and remote command execution are usually penetrated. Typical rudimentary methods such as sending phishing emails, spyware attachments etc, are used to increase the spread. It is very important to remember that infecting one machine in a network is enough, because that machine acting as a zombie, can easily replicate the botnet code to other machines in the same network.
Famous Botnets
At this point, it is important to discuss few botnets which are famous due to their notorious ways of infecting systems and still being tough to detect.
Conficker
Originally thought to be a virus, Conficker had built-in software routines which could allow the infected machine to be controlled remotely, making it a bot threat. While it was written for windows operating systems, few variants were created later, to infect Unix and Linux systems too. It used the hidden file share vulnerability of windows, to get into the machine and then turn it into a zombie to spread the infection further. With an infection count of over 10 million machines across the globe, Conficker is still found in systems which are improperly configured or not protected by a strong perimeter defense system.
Mariposa
This botnet used spywares and malwares as a vehicle to inject machines and install a payload of command and control center modules. The purpose of Mariposa was to run in stealth mode and keep an eye on passwords, credit card numbers being typed on the machine. It was also programmed to intercept internet browser requests, and lure it to pages hosting updated copies of the botnet itself, as well as the advertisement pages.
Srizbi
This botnet was specifically designed to create billions of spam email messages every day. It spread mainly via pirated and free downloaded software on internet, turning multiple machines into zombies. It had a very small footprint which made the detection very difficult. It had a different control module by which an infected server would be the owner controlling zombie army, while other infected servers simply keeping a watch on it, and would take over if the controller server fails or shuts down. Srizbi is known to have created massive email spam attacks causing denial of service on the mail servers.
BredoLab
This is the most recent botnet army which infected over 20 million machines worldwide. While the main purpose was to create massive email spam, this botnet also incorporated spywares and viruses in its payload. It is known to infect Linux operating systems of various distros, and deploying root kits on those, to run in a stealth mode. It was dismantled by law authorities, but is believed to still exist in the form of variants.
Protecting FOSS systems
As we learnt, the botnets exploit all the possible vulnerabilities and create their own eco-system for evil cause. While botnets are difficult to detect and tackle, there are few preventive mechanisms that every network administrator should adopt in their infrastructure. The first and foremost security mechanism that should be deployed is the perimeter defense system. A properly configured router and a firewall must be in place, and the firewall should be configured with auto-updating anti-spam filters. As for physical security, disabling USB drives, CD drives would help to a great extent. It is important for Linux administrators to know that Linux distros are not secure from botnets either, though the percentage of infection is somewhat lesser than windows machines. For FOSS systems, performing a rigorous routine check for root kits and malwares is a must. Linux systems which typically host web servers and FTP farms are usually the first targets to deploy the payload. Strengthening and locking file systems is advised too. Attackers who plan to inject a botnet can use simple methods of breaking into authentication systems, via SSH protocol or over web. Thus using a strict and complex password scheme is very important. It has been found that running un-necessary services on a production Linux server is a common practice, which should be discouraged as it opens up stray ports which are left unmonitored and thus become a backdoor for attackers. Just to summarize, cyber security is all about processes and practices, than just the products. Hence understanding how botnets attack is imperative for system administrators to devise a security strategy based on their network scenarios.

