Cloud Delivery Models In a IaaS model too, infrastructure is provided to run applications. The cloud computing approach provides a pay-per-use model for the client…
Year: 2020
Top 5 Web Predictions for Year 2020
We at Valency Networks, keep on studying various attack patters, while performing application security penetration testing for our customers. We also keep an eagle’s eye…
FedRAMP Cyber Security Certification 5
Q. What is FedRAMP? A. The Federal Risk and Authorization Management Program (FedRAMP) is a US government program that provides a unique approach toward security…
FedRAMP Cyber Security Certification 4
Goals and Benefits of FedRAMP The Goals of FedRAMP are to 1. Ensure use of cloud services adequately protects and secures federal information. 2. Enable…
FedRAMP Cyber Security Certification 3
FEDRAMP SECURITY ASSESSMENT FRAMEWORK FedRAMP SAF is compliant with FISMA and is based on NIST Special Publication 800- 37. Federal Agencies are needed to assess…
FedRAMP Cyber Security Certification 2
FedRAMP Features: FedRAMP was created out of the Federal Cloud Computing Initiative to remove the barriers to the adoption of the cloud. • Cloud computing…
FedRAMP Cyber Security Certification 1
OVERVIEW FedRAMP, The Federal Risk and Authorization Management Program is a United States Government program that standardizes how Federal Information Security Management Act (FISMA) is…
Cloud Fundamentals and Cyber Security Assessment -1
Cloud Fundamentals and Cyber Security Assessment Cloud Computing Cloud computing refers to a model in which computing resources and applications are accessed on demand, from…
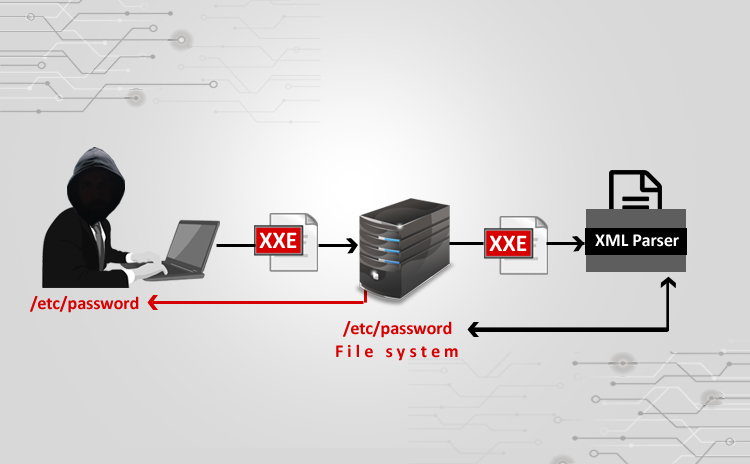
XXE Attack using Burpsuite
Steps: ⦁ I used a vulnerable website (⦁ http://testhtml5.vulnweb.com/#/popular) a)Pre-settings to be done b)Go to the vulnerable website: c) Do Forget password: ⦁ I have…
WordPress VAPT And Fixation Techniques
VULNERABILITIES FIXATION TOOL USED FOR SCAN – WPSCAN. PLUGIN USED FOR FIXATION Full path disclosure: Many websites running WordPress are exposing the internal path/full path…