XML-RPC Vulnerability – Risk and Mitigations Previous versions of WordPress (i.e., below version 3.5) were making use of XML RPC for the application to be…
Author: Jemima
Choosing testing environment for VAPT
Choosing testing environment for VAPT Typically applies for Web Applications and APIs Vulnerability Assessment and Penetration Testing is usually performed either on UAT environment or…
What is the ideal web session timeout?
One of our customers for whom we had performed Mobile App VAPT asked us, what should be the ideal session timeout for their FinTech App?…
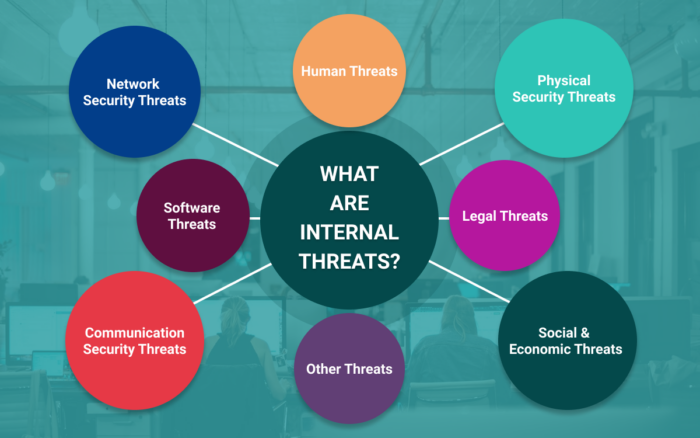
Why is it important for companies to plan for internal threats?
Internal threats refers to risks to data that stem from inside the organization due to poorly managed security of network, resources, assets and much more….
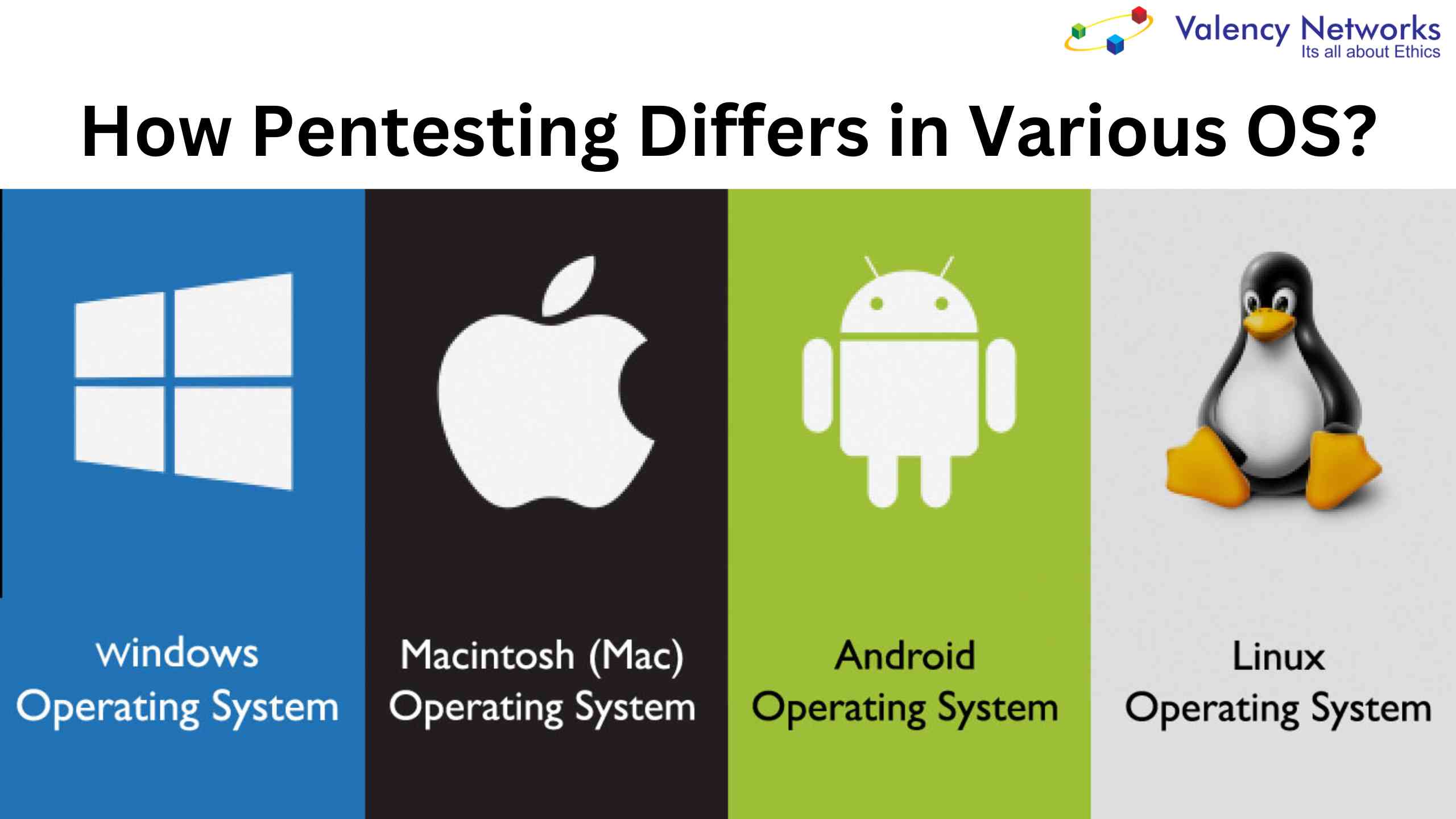
How pentesting differs in various operating systems?
Different operating systems are based upon different ideologies. Linux based operating systems like Kali, Parrot OS, Backbox Linux are specifically made with certain inbuilt tools,…
What are the 4 types of IT security?
Every organization has some data to protect. The data, if stolen can cause huge damage to an organization both reputational and financial. Hence, it becomes…
What are major cyber security risks?
Cyber security risk is a risk that could potentially harm the confidentiality, integrity and availability of the data through an attack either on asset, network…
Patch management tricks and techniques
I. What is a patch? In technical terms, “Patch” are the changes performed on a computer program/software to enhance its security shield against newly rising…
Cyber Security Webinar – Working From Home – For Senior Management
Cyber Security Tips – Working From Home For Senior Management Note – Enable sound – this video has an audio track.
Cyber Security Webinar – Working From Home – Securing Workstations
Cyber Security Tips – Working From Home Securing Workstations Note – Enable sound – this video has an audio track.