- DORA Compliance – A Complete Guide by Valency Networks - 31/01/2025
- Is ICMP Timestamp Request Vulnerability worth considering - 31/12/2024
- Understanding Threat Intelligence in ISO 27001-2022 - 21/11/2024
FEDRAMP SECURITY ASSESSMENT FRAMEWORK
FedRAMP SAF is compliant with FISMA and is based on NIST Special Publication 800- 37. Federal Agencies are needed to assess and authorize the information systems in accordance with FISMA. FedRAMP specifies a set of controls for Low and Moderate security impact level systems based on NIST baseline controls (NIST SP 800-53, as revised) with a set of control enhancements. It pertains to the unique security requirements of cloud computing.
FedRAMP uses the documents and deliverables same as the NIST requires Agencies to use, as described in NIST SP 800-37. The only part of the FedRAMP process that is new to Federal Agencies involves the Control Implementation Summary.
FedRAMP simplifies the NIST Risk Management Framework by creating four process areas. It encompasses the six steps detailed within NIST SP 800-37. Those steps are: Document, Assess, Authorize, and Monitor as shown in figure below.
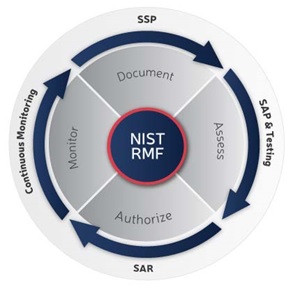
source: fedramp.gov
1. Document
Document phase of the SAF of Risk Management Framework includes the following:
1.1. CATEGORIZE THE INFORMATION SYSTEM
The Cloud Service Provider (CSP) determines the information types and categorizes the types of data (or can be) contained within the system. It determines the impact to the system. The categorization is based on NIST Special Publication 800-60 (Volumes I and II) Guide. It Maps the types of Information and Information Systems to Security Categories.
1.2. SELECT SECURITY CONTROLS
Once the CSP is selected then the FedRAMP security control baseline. The next step involves the implementation of the security controls related to that impact level. For most of the providers, many controls are already implemented but those needs to be described within the FedRAMP templates. Some of the controls might require the implementation of new capabilities, and some might require a re-configuration of the existing implementations.
1.2.1. SYSTEM SECURITY PLAN
Once the security controls are implementation is completed, The CSPs must document the details of implementation in a System Security Plan. All cloud providers must have use the FedRAMP template, regardless of what type of ATO they are vying for.
1.2.2. INHERITING CONTROLS FROM A LOWER-LEVEL SYSTEM
Many cloud systems rely on other cloud systems in the cloud space. It is to provide a comprehensive set of services to the end customer. For an example, a software provider utilizes an infrastructure provider to deliver the Software as a Service (SaaS). Here, the software provider will inherit security controls from the infrastructure provider.
1.2.3. ADDITIONAL SECURITY CONTROLS FOR SPECIFIC NEEDS
Agencies may need additional security controls in addition with the FedRAMP baseline due to specific Agency mission requirements.
1.2.4. SUPPORTING DOCUMENTS
CSPs have to submit supporting documents in order to completely and accurately document the security control implementation in the SSP. This needs to be done at the same time when the SSP is submitted. These supporting documents include following: a Privacy Threshold Analysis, the CSP’s Information Security Policies, User Guide for the cloud service, an e-Authentication Worksheet, Rules of Behaviour, a Configuration Management Plan, a Control Information Summary (CIS), IT Contingency Plan and an Incident Response Plan.
2. ASSESS
CSPs should make use of an independent assessor to test the information system. This demonstrates that the controls are effective and implemented as documented in the SSP. The assessment starts with documenting the methodology and process for testing the control implementation in the SAP (Security Assessment Plan).
2.1. USE OF A THIRD-PARTY ASSESSMENT ORGANIZATION
CSPs that seek JAB P-ATO needs to make use of a 3PAO to perform the testing phase of the process.
2.2. USE OF A NON-ACCREDITED INDEPENDENT ASSESSOR
CSPs submitting Agency ATO FedRAMP packages should have the system tested by a third party vender; but they are not required to use a FedRAMP accredited 3PAO. Federal Agencies will require to submit an attestation describing the independence and technical qualifications of the IA utilized to assess that CSP package if a non-accredited IA is used.
2.3. COMPLETE THE SECURITY ASSESSMENT PLAN
The Security Assessment Plan (SAP) is developed by the 3PAO or IA. The 3PAO or IA creates a testing plan using the FedRAMP SAP template. The SAP identifies all the assets within the scope of the assessment, that include hardware, software, and physical facilities. It provides the roadmap and methodology for execution of the tests. It indicates that the 3PAO or IA will use the FedRAMP associated security test cases that are provided in the form of a worksheet.
2.4. USE TEST CASE PROCEDURES
All 3PAOs and IAs should use the FedRAMP baseline security test cases while assessing a cloud system slated for FedRAMP compliance.
2.5. PERFORMSECURITYTESTING
The 3PAO or IA performs the testing of the CSP’s system by following the procedures mentioned in the SAP and in accordance with the test case procedures.
3. AUTHORIZE
The next step after completion of testing is for AOs to make an authorization decision and the risks identified during the testing phase.
3.1. ANALYSIS OF RISKS
This step involves the analysis of the risks and presents the results in a Security Assessment Report (SAR) using the FedRAMP template.
3.2. PLAN OF ACTION AND MILESTONES
The CSP develops a Plan of Action & Milestones (POA&M) after receiving the SAR. The CSP needs to demonstrate a plan in place and is complete with staffing, resources, and a schedule, for correcting each security weakness identified.
3.3. SUBMIT A SECURITY PACKAGE FOR AUTHORIZATION
In this step, the CSP must assemble a final package and submit the package for authorization review.
3.4. AUTHORIZATION LETTER
After AO makes a risk-based decision to authorize a CSP environment for use, this decision is formalized in an ATO letter.
3.5. LEVERAGING FEDRAMP SECURITY PACKAGES
In this stage, Agencies may want to review the list of security packages available before attempting to acquire services from a CSP that is not in FedRAMP Secure Repository.
3.6. REVOKING AN AUTHORIZATION
CSPs with an authorization implement continuous monitoring and maintain an appropriate risk level to maintain an authorization.
4. MONITOR
This is the final process for cloud services in FedRAMP. Once a CSP receives a FedRAMP Authorization, it must implement a continuous monitoring capability to ensure the cloud system maintains an acceptable risk posture.
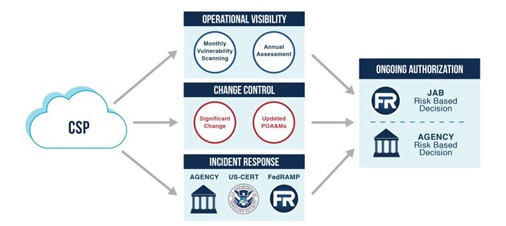
source: fedramp.gov
4.1. OPERATIONAL VISIBILITY
The goal of this step is to reduce the administrative burden associated with demonstrating compliance, instead to shift it toward real-time oversight monitoring.
4.2. CHANGE CONTROL
CSPs might include periodic changes to the system with reference to the procedures found in the system’s Configuration Management Plan. These changes must be reported in order to meet the FedRAMP requirements.
4.3. INCIDENT RESPONSE
The single incident may have an impact on the multiple Federal Agencies which are leveraging the cloud services. FedRAMP works with US-CERT in order to coordinate the incident response activities in accordance with the FedRAMP Incident Communications Procedure.

