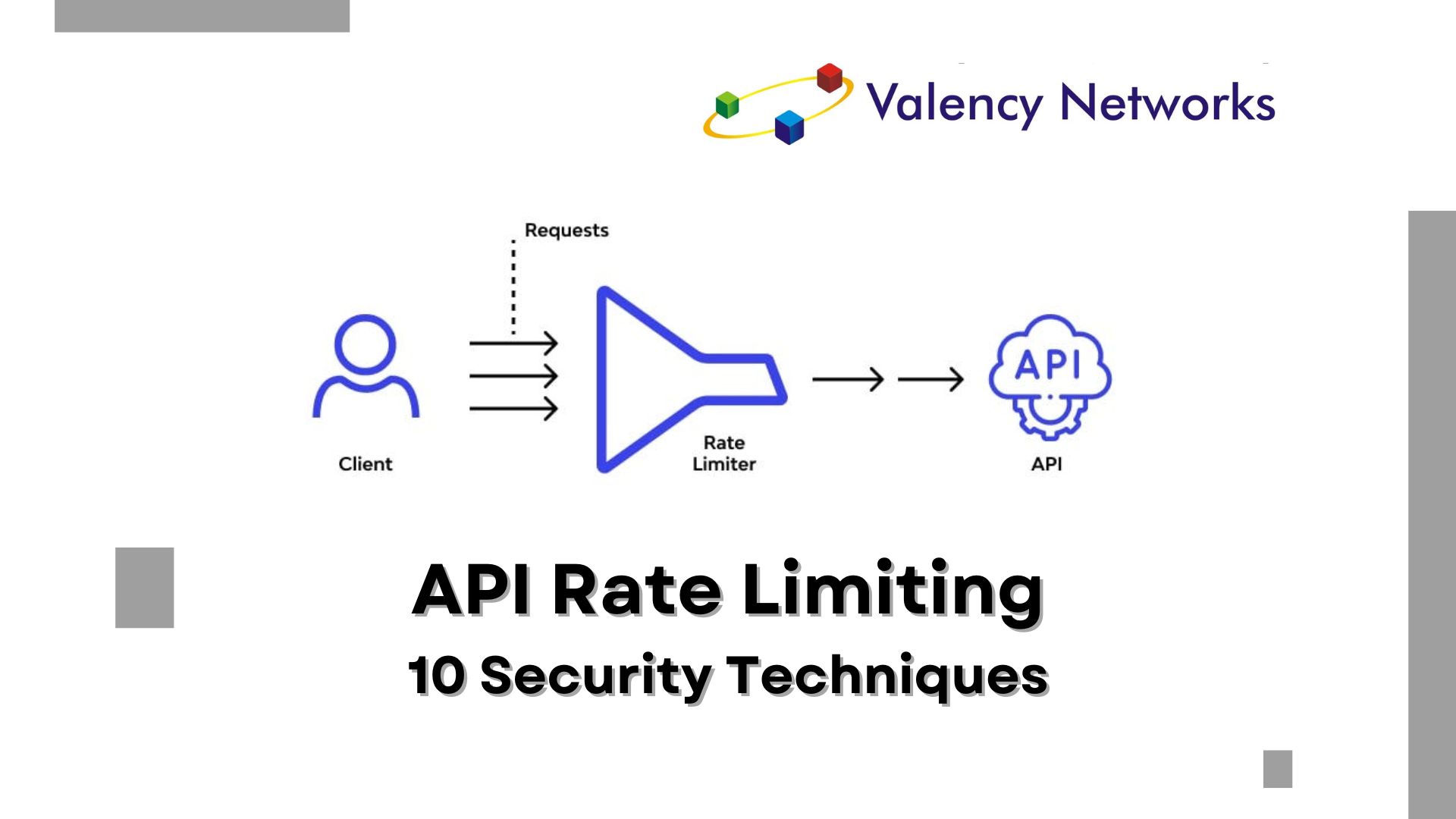
As the Chief Technology Officer at Valency Networks, I understand the critical importance of securing your REST API against misuse and abuse. Rate limiting is…
Cloud Security
Benefits of ISA 62443 Compliance
A flexible framework to manage and mitigate present and future security risks in industrial automation and control systems is provided by the ISA/IEC 62443 series…
Difference Between Web Based application and Cloud Based Application
This article talks about basic differences between web and cloud apps. It further explains what a pentester needs to think about, while performing vulnerability assessment…
Top Threats In Cloud Security
“Top Threats to Cloud Computing”, provides needed background to help organizations in making refined risk management decisions regarding their cloud adoption strategies. #Threat1- Misuse of…
Cloud Fundamentals and Cyber Security Assessment -4
Major attacks • Back-door: A back-door attack takes place using asynchronous external connections or dial-up modems. Here, the strategy is to gain access to a…
Cloud Fundamentals and Cyber Security Assessment -3
Security threats 1. Misuse of Cloud Computational Resources: In order to conduct cyber-attacks on computer systems, a large amount of computing power is required. So,…
Cloud Fundamentals and Cyber Security Assessment -2
Cloud Delivery Models In a IaaS model too, infrastructure is provided to run applications. The cloud computing approach provides a pay-per-use model for the client…
Cloud Fundamentals and Cyber Security Assessment -1
Cloud Fundamentals and Cyber Security Assessment Cloud Computing Cloud computing refers to a model in which computing resources and applications are accessed on demand, from…
Cloud Star Certification For Cloud Services Providers
Cloud Star Certification for Cloud Services Providers 1.What is CSA STAR Certification? CSA STAR Certification is a unique new scheme developed to address specific issues…
Cloud Application Pen Testing
Cloud Application Pentesting With the growth of cloud computing, Penetration testing deployment is becoming bit difficult due to its shared responsibility model. Cloud computing brings concept of…