VULNERABILITIES FIXATION TOOL USED FOR SCAN – WPSCAN. PLUGIN USED FOR FIXATION Full path disclosure: Many websites running WordPress are exposing the internal path/full path…
Code Security
Vulnerability Assessment in 3 PHP Frameworks
Vulnerability Assessment in 3 PHP Frameworks PHP is the most widely used server side language to build web applications and has a good variety of…
PHP Security Best Practices-2
PHP security PHP is a powerful and flexible tool. This power and flexibility comes from PHP being a very thin framework sitting on top of…
PHP Security Best Practices – 1
Title: PHP Security Scope of article In the open source world, PHP programming is always given first choice due to its availability and flexibility. It…
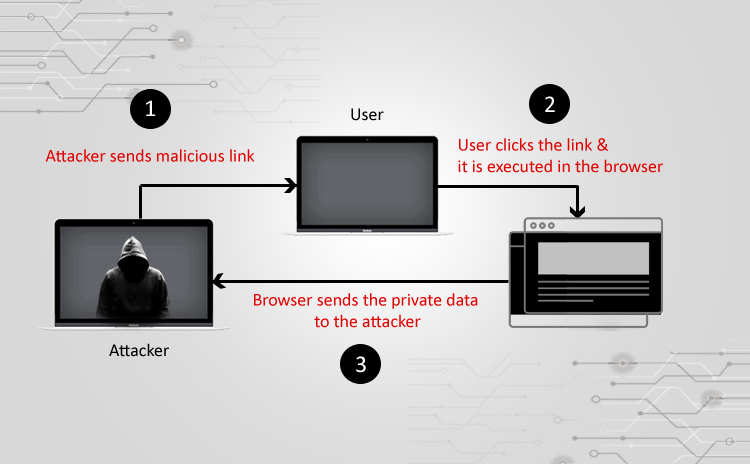
How to handle Non Persistent XSS injection
How to handle Non Persistent XSS injection Cross-site scripting (XSS) attacks are a type of injection, in which malicious scripts are injected in the client…
Angular JS Security Fundamentals
AngularJS Vulnerability Assessment on Web ⦁ Introduction: In this era of digitization, technology has been changing at a rapid pace and businesses are always looking…