Latest posts by Nabashree (see all)
- Vulnerability Assessment Of Windows 7 using Nexpose Tool - 05/04/2021
- XXE Attack using Burpsuite - 06/01/2020
- Fundamentals Of ISO 27001 - 03/01/2020
Steps:
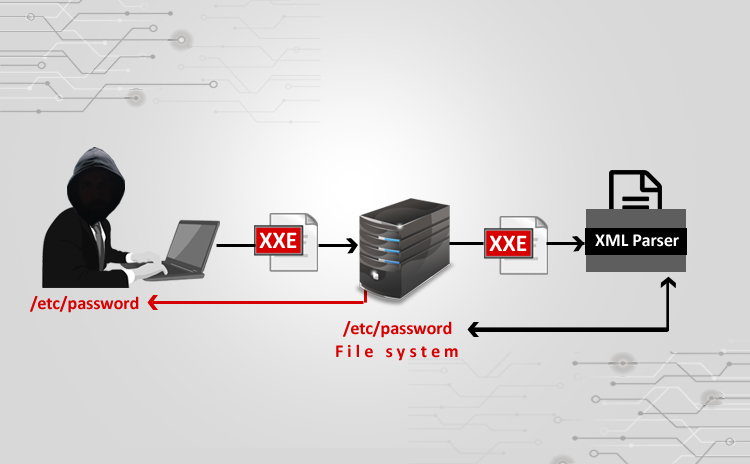
⦁ I used a vulnerable website (⦁ http://testhtml5.vulnweb.com/#/popular)
a)Pre-settings to be done
b)Go to the vulnerable website:
c) Do Forget password:
⦁ I have used Burpsuite to Intercept the data
⦁ Generated a request to generate new password
⦁ The request was using “Explicit XML entities” as we can see above in the screenshot.
⦁ Since we were able to understand the method, how the XML was used, we injected a different entity in the code(payload) and generated the request. Hence causing Breach.