Penetration testing is performed on Win 7, Win Server 2008, Ubuntu form Kali being the attacker. All the Penetration test is performed on the Virtual…
Author: Nabashree
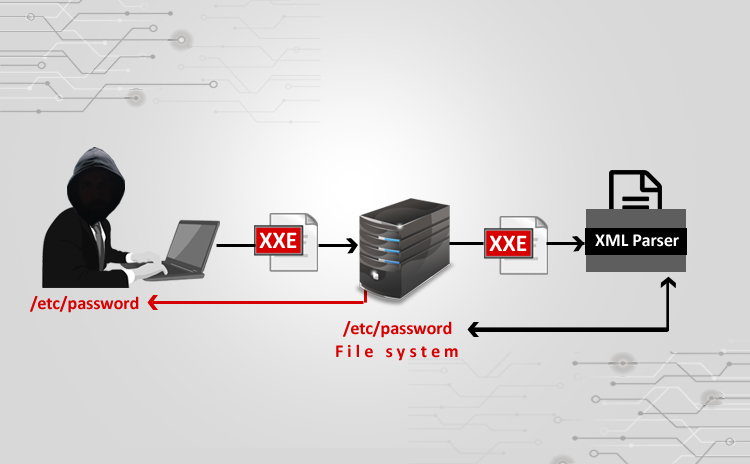
XXE Attack using Burpsuite
Steps: ⦁ I used a vulnerable website (⦁ http://testhtml5.vulnweb.com/#/popular) a)Pre-settings to be done b)Go to the vulnerable website: c) Do Forget password: ⦁ I have…
Fundamentals Of ISO 27001
What is the ISO 27001 standard? The ISO 27001 standard adopts a process approach for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving an organization’s…