- Vulnerability Assessment Of Windows 7 using Nexpose Tool - 05/04/2021
- XXE Attack using Burpsuite - 06/01/2020
- Fundamentals Of ISO 27001 - 03/01/2020
Penetration testing is performed on Win 7, Win Server 2008, Ubuntu form Kali being the attacker. All the Penetration test is performed on the Virtual machine by creating a test lab environment setup Win7, Win Server 2008 and Ubuntu on one base machine while Kali installed on a different base machine. In accordance with the case given pen test had to be performed on that given scenario which includes tools like wamp server to deploy a PHP page on port 80 in Win Server 2008 and install Active directory to that OS.
Vulnerability Assessment and Penetration Testing is performed using Nmap and Nexpose tool to find the loopholes in the network so that preventive measures are to be taken and the attacker cant exploit it.
NMAP Scanning:
Nmap is a network mapping tool used in the Reconnaissance stage of a network penetration testing. There are mainly two reasons for a system being vulnerable, the first one is misconfiguration and the other once is incorrect programming practices. In the case of networks, devices such as servers, routers, ports, switches as well as firewalls and IPS systems are either misconfigured or not configured at all.
Therefore, Nmap is performed to search the open TCP ports present in the network:
# nmap IP Address
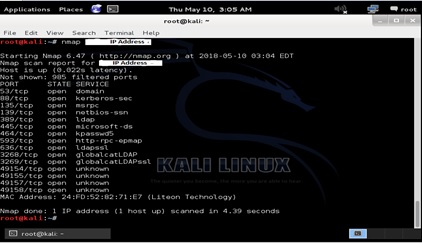
Nmap Identifies open ports on the target host in preparation for auditing and helps in finding vulnerabilities in the network.
For Scan for every TCP and UDP open port:
# Nmap -n -PN -sT -sU -p- remote_host
The output is captured below:
All the TCP and UDP open ports are listed out.
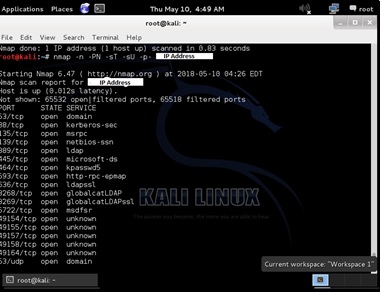
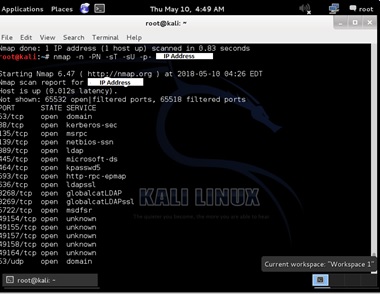
For a secure network all the default ports should be closed. Because an open port exposes the services that are listening to those ports to be exploited. Therefore, it is very much necessary to have firewall to restrict intruders’ connection.
For Nexpose Scan:
Nexpose generates audit reports, xml reports for internal as well for external IPs. These tools is one of the leading vulnerability assessment tool that gives graphical output of the scan along with the assessment repot. It is a product of rapid7.It gives an adaptive security, real risk score and policy assessment.
Nexpose needs a strong machine to run on:
- 2 GHz + processor
- 4 gb RAM available (8 gb recommended)
- 1 gb available disk space (50 gb recommended)
Before starting the installation of nexpose these pre-steps to be done:
Run # service postgresql stop
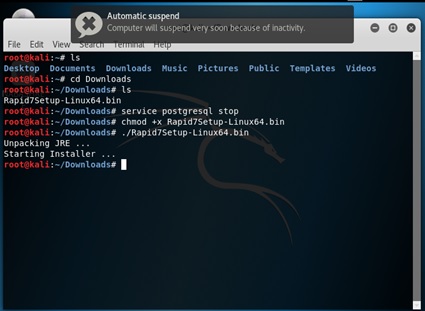
After giving execution permission to the nexpose bin file and running it, the installation pages pops up.
Once the installation of nexpose tool is done, to run the console we need to execute the command below on the terminal.
# sudo systemctl start nexposeconsole.service
While in the browser we need to go to https://localhost:3780
The loading of console takes about 45 mins,until we get the login page for nexpose.
Once the Nexpose is installed, we login with our credentials, that was set during the installation process.
Nexpose Execution:
A set of IP address can be scanned all together using this tool.
At the end of the scan the vulnerabilities existing are pointed out along with the audit report which gives an executive summery of the vulnerabilities present with a graph about the criticality and severity of that vulnerability and how that vulnerabilities could be exploited by the attackers and thus help in prioritising the vulnerabilities.
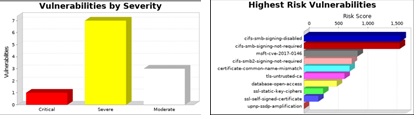
This tool also categorises the vulnerabilities
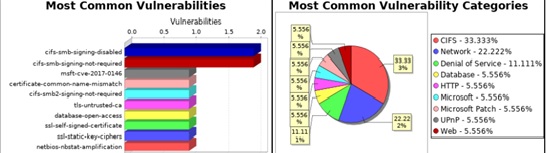
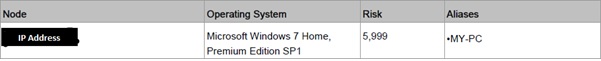
The report also contains the discovered systems, that was found during the scan process, the risk count of that system
A detailed description on each of the critical vulnerabilities, severe vulnerabilities, moderate vulnerabilities and how it could be exploited, the affected nodes, vulnerability solution and references are mentioned.
In the report the discovered services like CIFS(Common Internet File System), are mentioned in detail and what are the instances discovered on the services, protocol, port, device and vulnerabilities. Nexpose also discover the users, groups, databases, files, directories, spidered websites .Thus this VAPT tool helps to identify the vulnerabilities and suggest measures to safeguard them by pointing out the loopholes that could be exploited by the attackers.

