Choosing testing environment for VAPT Typically applies for Web Applications and APIs Vulnerability Assessment and Penetration Testing is usually performed either on UAT environment or…
Tackling XSS – The Right Way to Fix Vulnerabilities
As the CTO of Valency Networks, I’ve seen many software developers struggle with cross-site scripting (XSS) vulnerabilities. Unfortunately, a common mistake is to focus on…
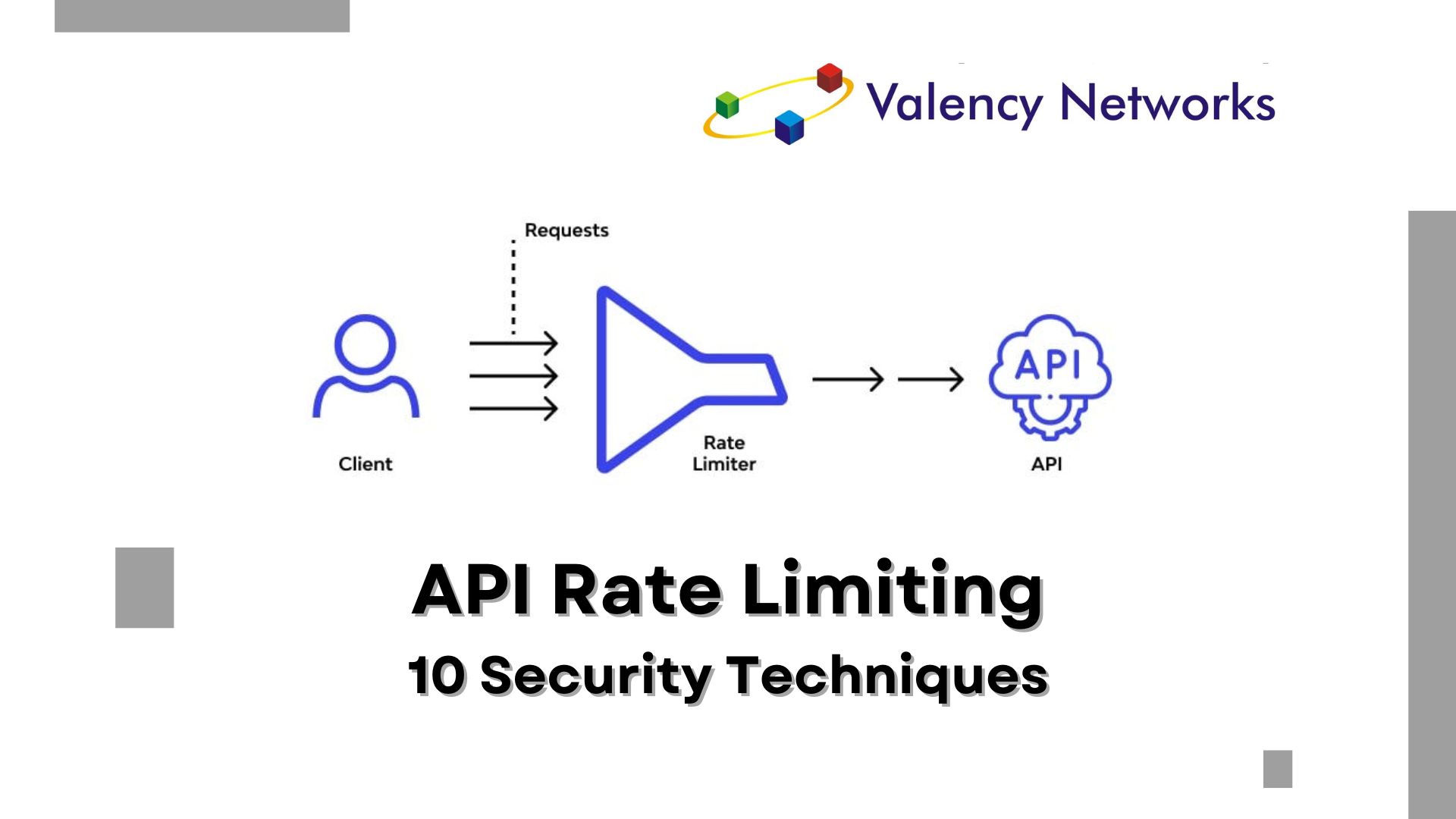
10 Rate Limiting Techniques for Securing Your REST API
As the Chief Technology Officer at Valency Networks, I understand the critical importance of securing your REST API against misuse and abuse. Rate limiting is…
Are Android Apps More Secure or iOS Apps
Are Android Apps More Secure or iOS Apps? When it comes to mobile app security, developers play a crucial role regardless of the platform they…
Is XSS Vulnerability Possible on Mobile Apps
Cross-Site Scripting (XSS) is a common vulnerability found in web applications that allows attackers to inject malicious scripts into web pages viewed by other users….
Difference Between Information Security and Cyber Security
Definitions Information Security (InfoSec): Information security is the practice of protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. It focuses on ensuring…
Difference Between Privilege Escalation Attack and IDOR Attack
Privilege Escalation Attack: Definition: Privilege escalation is a type of cyber attack where an attacker exploits vulnerabilities to gain unauthorized access to higher-level permissions or…
Employee Responsibilities in an ISO 27001 Certified Organization
Understanding ISO 27001 Compliance ISO 27001 is an international standard for Information Security Management Systems (ISMS). It provides a framework for establishing, implementing, maintaining, and…
Exploring TISAX Version 6 – A Comprehensive Guide
Exploring TISAX Version 6: A Comprehensive Guide Introduction: In the ever-evolving landscape of cybersecurity, TISAX (Trusted Information Security Assessment Exchange) plays a crucial role, providing…
TLS Based Attacks
TLS Attack TLS Attacks This is a follow up article for another interesting topic which is titled as “Are TLS vulnerabilities considered critical for internal…