- DORA Compliance – A Complete Guide by Valency Networks - 31/01/2025
- Is ICMP Timestamp Request Vulnerability worth considering - 31/12/2024
- Understanding Threat Intelligence in ISO 27001-2022 - 21/11/2024
Cyber Attacks Explained: Database Hacking
Scope of article
In this article we are going to delve into database security attacks. Database is the heart of any website or application and hacking into it can cause serious losses. First we will discuss possible database specific attacks and then talk about various means to protect infrastructure from them. We will also touch upon the FOSS infrastructure protection mechanism too.
Database fundamentals
We all know that databases are a structured collection of data in a digital form. The structure consist of schema definitions, tables which store the data in an organized form, views which are virtual tables and stored queries to improve performance etc. Database engine is responsible to accept SQL query requests, execute those and provide data back to the querying computer.
For this purpose, database service listens on one or more TCPIP ports. The service also runs very closely with the operating system, in order to gain better control on the disk and memory resources. Modern database engines provide many features such as web services, data encryption etc.
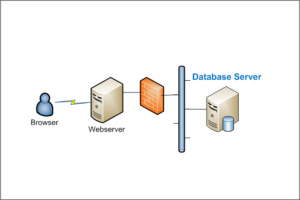
Fig 1 shows a typical database hosting architecture for a website. A database server may or may not use the authentication services and access controls provided by the operating system, it is very common to use the controls provided by the engine itself. Each user who is supposed to login to database to access information is bound by basic security features such as rules and roles. Database security is designed around the data integrity as well as the database performance. It is important to know that, too tight security can jeopardize database performance, which may not be acceptable in a business scenario.
Database Hacking
Database contains mission critical data of the corporate firm, which makes it an obvious target by hackers. Please refer to Fig 2, which shows the module stack that forms database security model. We will first see few ways by which a hacker tries to gain control of a database, followed by few protection mechanisms that we can deploy to address these problems.
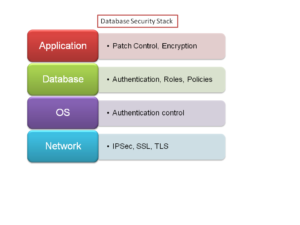
Usually a database server is not hosted in a less secure demilitarized zone; hence the hacker has to go pass the web layer to access the database. Database is a widely and continuously accessible component, which makes it more vulnerable and susceptible to attacks. Database security requirements touch all networking layers, and hence, need careful design
Password guessing – Once the hacker gains control of web server, he looks for the application configuration files which typically contain the database server name, userid and password to access it. If the file is encrypted or if the information is hard-coded in the code for security reasons, hacker is left with an option to guess the password. It is found to be a common thing to leave the database system administrators account name unchanged, which solves half of hackers’ problem. In most cases the username and password are kept the same, if not, hacker can use guess work, or brute force method to gain access to the database. Depending upon the access level granted to the user, hacker gains control and is capable of doing further damage.
Packet sniffing – Modern hackers gain control of the network in which the database server is hosted, and deploy a sniffer to capture packets flowing to and from the database server. These packets are then analyzed to decipher username and password combinations and the real target is to get this information for root database administrator.
Query string manipulation – When a web server gets a request from a browser, it receives it in the form of a web url containing a query string parameter which directs the web application to database to fetch the requested data. If the application developer is not security aware, and not following best coding practices, this simple method of fetching data can lead to opening up loopholes. For example, if a list of doctors is being asked for on an insurance website, the code must ensure that a blank value in the zip code field should not be allowed. Doing so, the hacker can run a query and fetch entire data which he may not have access to, in ideal scenario.
Privilege elevation – As mentioned earlier, database servers use roles and rules to control access of a user to a particular database or a table or resource in general. An attacker usually inject scripts which try to find out most generous level of privileges and upon finding one, uses it to create further damage. Few FOSS database servers such as MangoDB, were found to be victim of these bugs which were eventually fixed.
Vulnerability exploitation – Like operating systems, even the database servers do have bugs resulting into serious vulnerabilities. Attackers can explore and exploit those either through the web layer, or by injecting a Trojan in the system dedicated for this purpose. Hackers are always looking for unpatched database system for this purpose.
SQL Injection – This attack is not a pure database attack, but in fact a combination of database and web vulnerability. It’s a very well known type, in which an attacker uses webpages to plant the attack. It is done by including parts of SQL query statements in the web form, which is usually to be filled up by web user with relevant information. If the web page is not capable of handling this situation in a secure manner, it ends up sending this bogus request to the database. The attacker can simply run a select query to dump the entire database on his machine by this method, which makes it a favorite of hackers and hence dangerous from firm’s security standpoint.
Database DoS – As a typical denial of service attack, the attacker plants a code either on the web server or the database server itself, which sends requests to the database in order to overwhelm it. For example, the queries can be either at application layer to dump database contents in a loop, or at TCP layer, it can be a SYN packet storm. The end result is, the database gives up at one point and stops responding to the queries, thus resulting into a complete website or application failure.
Protecting FOSS systems
Since database servers are an important component of the whole system, multiple measures are to be deployed to ensure security. Following few methods help achieve that.
Patching is a first level of defense for databases. A robust patching system must be deployed to secure all the servers connecting to a database server. Sticking to one authentication method, and that too the one provided by database service should be used. When we don’t use operating system based authentication, we automatically keep unauthorized users away, making the access control job easier.
As for roles, a minimum set of roles should be created to avoid future confusions, and the roles should be application specific, rather than purpose specific. This helps in keeping track of which user did what, in terms of accessing the resources. Disabling unwanted database features and services is a good idea too.
In terms of data integrity, using SSL or TLS encryption is useful, especially to avoid packet sniffing of the data flowing between requesting server and the database server. As for data encryption, there are built-in features available for database server, whereby the encryption can be achieved for entire database, or at a granular level such as table or schema. This helps achieving data security without compromising on the server performance.
In modern architectures, a dedicated firewall for database server or farms is very common, allowing only the database port to be accessible from only a set of IP addresses. In case of a mission critical data handling, IPSec security along with NAT (network address translation) is encouraged. Firms who store massive amount of business critical data for their customers, can also think of deploying honeypots, whereby a hacker trying to invade into the network, is lured to a fake database server, thus keeping him away from the real critical data.
Summary
Database hacking is highly favored by hackers due to its benefits. It is achieve by exploiting inherent vulnerabilities. Properly configuring firewalls, database policies, and following best practices for the roles and rules by the network administrators is important to protect their corporate data from prying eyes. It is important to note that, the legacy method of protecting database servers at operating system level is not sufficient in the modern days and it needs careful design and deployment of intrusion detection and removal components.
More Relevant Links Below
Web Application Penetration Testing Services
Cloud Application Security Services
Mobile App Penetration Testing Services
REST API Penetration Testing Services
Network Security Auditing Services

