- DORA Compliance – A Complete Guide by Valency Networks - 31/01/2025
- Is ICMP Timestamp Request Vulnerability worth considering - 31/12/2024
- Understanding Threat Intelligence in ISO 27001-2022 - 21/11/2024
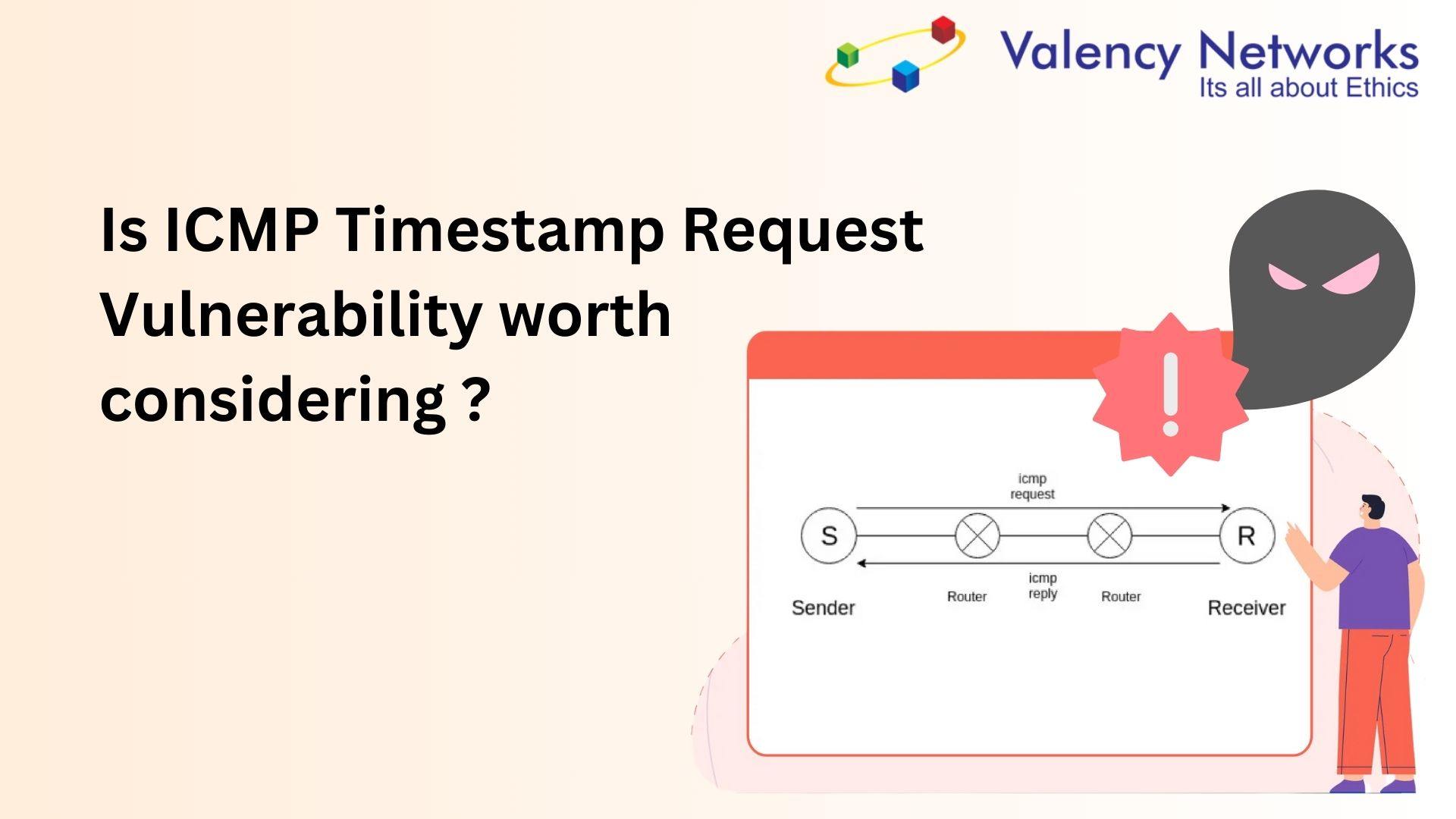
Is ICMP Timestamp Request Vulnerability worth considering?
The ICMP timestamp request vulnerability highlighted in the Nessus scan (or similar other tools) is typically a low-severity issue, and whether it is “worth” addressing depends on the context of your environment and threat model.
Understanding the Vulnerability
-
What is it?
When an attacker sends an ICMP timestamp request (Type 13), the targeted machine replies with its current time in milliseconds since midnight UTC. This can reveal the system’s approximate time settings. -
Why it matters?
The time value may help an attacker in:-
Time-Based Attacks:
Aligning the system’s clock with their attack environment to exploit time-sensitive authentication mechanisms (e.g., Kerberos tickets, one-time passwords, or time-based security tokens). -
Network Reconnaissance:
It can help attackers map the network by identifying devices responding to ICMP requests, especially if combined with other reconnaissance techniques.
-
Time-Based Attacks:
-
Windows-Specific Behaviour:
Windows Vista/7/2008/2008 R2 deliberately provide incorrect timestamps, but they remain within 1000 seconds of actual system time. This mitigates direct attacks like synchronization but still reveals approximate system time.
Is it Worth Fixing?
-
Risk in a Typical Internal Network:
-
Low Risk:
In internal or isolated networks, this vulnerability is generally not exploitable in a meaningful way unless the attacker already has access to the network and is conducting advanced reconnaissance. -
Recommendation:
While it is low-priority, disabling ICMP timestamp responses can still be considered part of a good defense-in-depth strategy, as it reduces unnecessary information exposure.
-
Low Risk:
-
Risk in an Externally Exposed Environment:
-
Higher Risk:
On systems exposed to the internet (e.g., public-facing servers or devices), ICMP responses, including timestamp responses, provide valuable information to attackers for reconnaissance. This should be addressed, especially in high-security environments. -
Recommendation:
For public-facing devices, blocking ICMP timestamp responses is a quick and simple step to reduce attack surface.
-
Higher Risk:
-
Does it Assist in Defeating Time-Based Authentication?
- While the timestamp itself reveals approximate time settings, exploiting this to defeat time-based authentication (e.g., OTPs) is typically complex and unlikely unless combined with other significant vulnerabilities.
- Most time-based protocols include buffers or tolerances (e.g., 30-60 seconds), making small discrepancies hard to exploit.
How to Fix It?
-
Disable ICMP Timestamp Requests:
- On Windows, ICMP timestamp responses can be disabled by adjusting the firewall or using Group Policy:
netsh advfirewall firewall add rule name=”Disable ICMP Timestamp” protocol=icmpv4:13 dir=in action=block
-
- On Linux, modify sysctl.conf:
net.ipv4.icmp_timestamps = 0
sysctl -p
-
Limit ICMP Traffic:
Use firewalls to block or restrict ICMP traffic where it’s not needed (e.g., in public-facing environments). -
Monitor and Review:
Regularly review your network’s attack surface to identify unnecessary exposures.
Any Known Malwares That Exploit This?
-
No Known Direct Exploits in Malware:
- There are no widely documented malware strains or exploit kits that specifically target ICMP timestamp responses to compromise systems or directly exploit this information for intrusion.
- Most malware focuses on vulnerabilities that grant more direct access or allow execution, like unpatched software, weak authentication, or open services.
-
Indirect Use in Reconnaissance:
-
While not the focal point of an attack, ICMP timestamp responses can play a role in network reconnaissance. Some advanced tools (used by attackers or malware) might collect timestamp information to:
- Identify active hosts on a network.
- Differentiate between live and dormant systems.
- Map network infrastructure.
-
While not the focal point of an attack, ICMP timestamp responses can play a role in network reconnaissance. Some advanced tools (used by attackers or malware) might collect timestamp information to:
Examples of tools using ICMP-based reconnaissance include Nmap and other network scanners, but this is primarily for discovery, not exploitation.
Practical Scenarios Of Exploitation
-
Time-Based Attacks:
-
An attacker could theoretically combine timestamp information with other vulnerabilities (e.g., in Kerberos or time-dependent protocols) to exploit discrepancies. However, this is rare and requires:
- Precise knowledge of the system’s internal workings.
- A lack of other compensating controls (like authentication tolerances).
- Likelihood: Very low, especially for modern systems with correct configurations.
-
An attacker could theoretically combine timestamp information with other vulnerabilities (e.g., in Kerberos or time-dependent protocols) to exploit discrepancies. However, this is rare and requires:
-
Internal Threats:
-
A human hacker inside the network is unlikely to exploit timestamp responses directly because:
- Gaining access to timestamp data offers minimal benefit compared to other methods (e.g., ARP spoofing, lateral movement tools like Mimikatz, or brute-forcing credentials).
- Internal attackers often prioritize more accessible attack vectors, like poorly secured administrative interfaces or shared credentials.
-
A human hacker inside the network is unlikely to exploit timestamp responses directly because:
Why Do Security Scans Flag This?
Security tools like Nessus flag ICMP timestamp responses as a potential vulnerability due to the principle of reducing attack surface:
- Even if the risk is theoretical or minimal, unnecessary exposure of system information increases the attack surface.
- Blocking or disabling timestamp responses eliminates a small reconnaissance vector, making it marginally harder for attackers to gather information about the environment.
Does the Lack of Malware Make It Less Severe?
Yes, the absence of documented malware or significant attack methods exploiting ICMP timestamp requests reduces the severity of this issue. However:
- It’s still best practice to disable this feature because it’s easy to do and doesn’t impact system functionality.
- In high-security environments (e.g., banking, defense), even theoretical risks are addressed as part of rigorous hardening.
Conclusion
- Severity: Low in most environments, especially for internal systems with no public exposure.
- Malware Focus: None currently exploits this directly, but it could aid reconnaissance efforts.
- Recommendation: Disabling ICMP timestamp responses is a minor task that aligns with good security hygiene, but it’s not a pressing issue unless your systems are publicly accessible or you handle highly sensitive data.
Fixing ICMP timestamp responses is a low-priority task for internal networks but becomes more important for systems exposed to external threats. In most cases, disabling timestamp responses is quick, easy, and part of reducing unnecessary information leaks. However, in low-risk internal setups, it might not be worth significant effort unless as part of broader hardening initiatives.