- DORA Compliance – A Complete Guide by Valency Networks - 31/01/2025
- Is ICMP Timestamp Request Vulnerability worth considering - 31/12/2024
- Understanding Threat Intelligence in ISO 27001-2022 - 21/11/2024
Title: Cyber Attacks Explained: Cryptographic Attacks
Scope of article
Cryptographic solutions are used to encrypt data transmission over wireless or wired protocols. Unfortunately these techniques are proved to be vulnerable to the cyber attacks, and data can be stolen or disrupted. In this article we will learn about this problem and also understand various means to strengthen the encryption techniques to protect the network infrastructure. We will also learn how to use various methods to achieve the same, using FOSS based solutions.
How cryptography works?
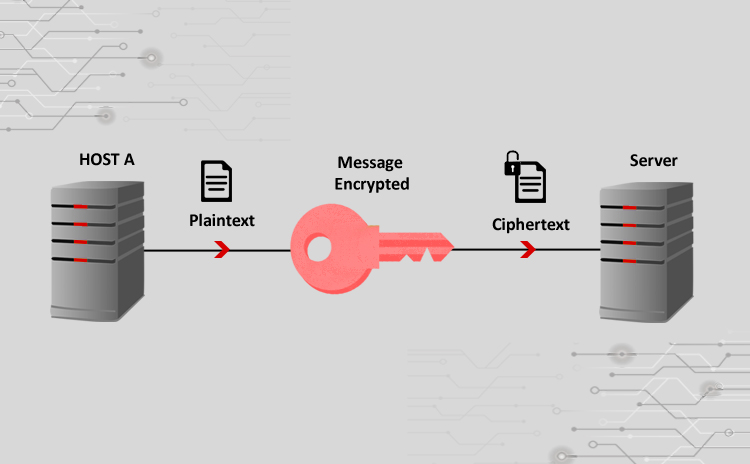
As we all know, the heart of cryptographic network communication is the public key cryptography (PKI), which is used to encrypt the TCPIP communication between two network end points. PKI uses various encryption algorithms to ensure data security. The whole idea behind encryption is to make it so difficult that it becomes a time consuming task to try out all the possible keys. For example, if a message is encrypted using an 8bit key, it means that 256 different combinations of the key need to be tried, to decrypt the data. Any computer can perform this task in less than a second. However if the key length is extended to 32, it would need 65536 combinations to be tried, needing few seconds. Extending this trick further, a 256 bit key would result into a large number of combinations, thus needing literally many years even for a powerful computer to crack it. While the key length is an important factor, the mathematical algorithm used for processing encryption and decryption is also equally important. The algorithm is supposed to quickly perform the action, while maintaining necessary data and key security. There are many algorithms such as SHA1, 3DES etc, each algorithm has its benefits over the other. There are two types of keys, symmetric and asymmetric. In case of symmetric key type, only one key is used for encryption and decryption, while in case of asymmetric keys there is a set of two different keys, which are complimentary to each other. Please refer to Fig 1 which shows the basic cryptography functionality, which is designed with the objectives of data confidentiality, integrity and authentication, in mind.
It is important to understand what cryptography means in the internet world. Internet is blessed with SSL (Secure Socket Layer) and TLS (Transport Layer Security) protocols. They perform the job of encrypting and decrypting data over the wire, so as to enable users put their personal information, credit card numbers on the website, to do online purchase. SSL and TLS are based on asymmetric key exchange of the PKI technology. In order for a person to use internet for online transactions, the browser is not supposed to trust the website and web server by default. There are two demands here, first being that the data must be encrypted for security reasons, and the second being that the website is hosted by a legitimate party. The latter is important because website may be hosted by an attacker to steal the personal information. To ensure the legitimacy, the web server is hosted with an SSL certificate, which enables the traffic on HTTPS protocol using TCP port 443 for communication. This SSL certificate is provided or signed by a trusted certification authority such as Verisign or Thawte, who ensures that the consumer of SSL certificate is a genuine party, will adhere to security standards and hence is eligible to obtain a certificate and install it on their servers. The SSL certificate is tied to the web domain name such as abcd.com.
To understand security concerns in the cryptography world, we need to first study how certificates work. Digital certificates using asymmetric PKI are composed of two keys, a public key and a private key. The private key is installed on the web server where the website URL is supposed to be secured using SSL. The public key is shipped along with the browsers, and this applies to all browsers which support SSL protocol. In order to support multiple certificate authority vendors, browsers are equipped with their public keys, as well as various ciphers too, which are nothing but the encryption and decryption algorithms. Each public key has its own expiration date and needs to be updated once it is close to expiration. When we install a digital certificate on a web server for a website URL, we are essentially installing the private key which is specifically created by the trusted certification providing authority.
Now let’s see how this mechanism works technically at a high level in case of a browser. As shown in Fig 2, when a person tries to access an SSL website, the browser first challenges server by sending its own cipher strength, in the response the server does the same and also sends its own copy of SSL certificate installed on it for the hosted website url. At this point, the browser checks validity and authenticity of the certificate by using the set of public keys on it. Upon finding it to be acceptable, browser sends back a digitally signed response to server to initiate the further secure communication. If the server certificate cannot be verified for authenticity, the browser alerts the user about this situation. It’s important to note that while SSL helps achieve security, there is a payback in terms of communication performance. Since the TCPIP communication by default, does not provide any security as such, adding encryption layer on top of existing protocol frame can result into a bigger TCP packet sizes.
Cryptographic attacks
It is a common observation that the network administrators invest time and money to design security around the applications, servers and other infrastructure components, but tend to take cryptographic security less seriously. Before we talk about various attacks, let’s understand first that cryptography is all about key, the data, and the encryption-decryption of the data using key. Few cryptographic attacks try to decipher the key, while the others try to steal data on the wire by performing some advanced decryption. Let’s take a look at few common attacks on cryptography.
SSL MITM attack – In this type, the attacker intrudes into the network and establishes a successful man-in-the-middle connection. Attacker silently watches the HTTPS traffic on the wire, and waits for the targeted website to respond to some browser’s HTTPS request. As we learnt earlier, the server is supposed to send its digital certificate to browser as a part of SSL handshake process. Attacker grabs this certificate, and notes down various details such as domain name, expiration date, cipher strength etc. Attacker then creates his own certificate, also called as a self-signed certificate, containing the same information as that of the captured certificate. From this point onwards, attacker becomes a real man-in-the-middle whereby each browser request is intercepted and responded with the fake certificate. As a normal response to such situation, the web browser pops-up a warning to user, which in most cases is ignored by the person browsing website, and thus the attacker is successful. Further on the server side, attacker establishes a separate HTTPS connection to complete the request and the result of response is fed back into the browser on the connection already established. This gives attacker a complete control on the SSL traffic and help steal the personal information. Since this attack involves a real intrusion into the network, it is less likely to happen, but can result into a serious data loss. Also since the attacker is not breaking request and response chain, it becomes tough to detect the data stealing operation.
SSL MITB attack – Similar to the attack mentioned above, in this type attacker injects a JavaScript code snippet into the browser to create a man-in-the-browser situation. This snippet monitors all SSL activities and records the session. While this is happening, the attacker also records encrypted version of the same session and programmatically tries to find out cipher strength and the key, besides stealing data. This attack is becoming more popular lately, due to multiple open source browsers and various security vulnerability problems with each of those.
Key Hijacking – This is another intrusive type of attack whereby the attacker gains access into the web server which hosts the website. This can be achieved by using multiple intrusion techniques already discussed in previous articles of this series. Once the server is compromised, attacker uses elevated privilege attack to gain access to the certificate store, from where the private key can be obtained. Attacker then uses packet sniffing to download an entire HTTPS session and stores it for offline decryption. The decryption process needs private key which is already stolen, and the public key which is available in the browsers trusted authority key store. The data set deciphered so, might reveal vital personal information such as userid, address, credit card number etc, assuming that the targeted website sells goods online using e-commerce technology.
Birthday SSL Attack – This attack relies on a mathematical theory called as birthday problem paradox, which says that statistically, in a set of randomly selected people some pairs of people will have same birthday. This theory tends to more accurate as the number of people chosen is large. In cryptography, the data integrity is established using a hash or checksum, which is calculated at both ends of the transmission to ensure that the data is not tampered with. Birthday attack targets on the hash, and needs multiple attackers coming together who individually capture chunks of data and share it among themselves. Each chunk is then analyzed programmatically to create additional set of data, in such a way that the hash of it matches that of the data chunk. In other words, for a given chunk of data and hash combination, the mathematical algorithm creates a clone data set. Further process of the original data chunk and the resultant data set, helps derive the encryption key. This attack is a very time consuming and technically complex type, but can be possible using multiple powerful computing machines and software programs.
Chosen Dataset attacks – As we learnt earlier, attackers always aim for data as well as the key in order to completely compromise a cryptographic system. A chosen dataset method consists of two different types. In first type, called chosen plaintext, attacker is assumed to have access to the original data and the encrypted version of it. Attacker then applies multiple encryption keys to the original data, each time the output is compared with the already encrypted version. If the result is positive, it means the key is derived. In the second type, called chosen ciphertext, attacker has the cipher text and also the decrypted version of it. Again, attacker tries multiple keys until the output matches that of the decrypted version obtained already. These attacks are bit less time consuming, however need attacker to gain enormous amount of data and computational power to seek the desired results.
SSL Brute force attack – This is a different type of attack wherein, attacker sends very small data sets to be encrypted by SSL protocol. Attacker captures the resultant outcome and stores it against the transmitted dataset. Upon performing such operation on lots of data chunks, a key can be eventually derived. This process is very slow and can take days to decipher the key, and such attacks could be found to be originating from within the firm’s network. To speed up the process this method is usually combined with the group key decipher attack.
Group Key Deciphering – As learnt earlier, key based encryption is dependent on the length of key, where a bigger key result into lot of time required deciphering it. In group key deciphering attack, multiple attackers come together, each one with their powerful machine. Unlike the brute force way where lot of data is captured, in group method only a given set of data is captured and used. This data is subjected to all the possible permutations of keys, to try decrypting the data. Since usually a 256bit encryption can take multiple years to decipher, using multiple powerful computing machines can bring the time down. Attackers also use statistical grouping of keys to be tried from different machines, to bring that time down further. In past, few such experiments showed that cracking a 128bit key required only few days. With improving CPU speeds and throughputs, it is feared that cracking a 1024bit key can unfortunately be a reality soon.
Compromised key attack – Cryptography is all about trust, whereby a trusted certificate provider authority signs a certificate. The provider itself is supposed to be extremely secure; however it has unfortunately happened in the past that their own private key is either exposed or stolen by attacker. Attacker then uses this private key to sign certificate created for a domain name, which is their own site. Any browser being lured to this website will not suspect such a website; this is because the certificate will pass the authenticity test. This happens because the public key of such certificates will already be present in the browser certificate store. This can, and in the past has, resulted into loss of personal information.
SSL DoS – Attackers main aim is usually to steal the data. Since it is a troublesome and highly technical process in cryptography, few attackers tend to use legacy methods such as a denial of service attack. SSL negotiation adds it payload on the TCP protocol, thus slowing down the communication to achieve security. To achieve SSL denial of service attack, the attacker establishes SSL communication through a browser and then sends multiple bogus packets with varying length on that channel. Each packet is decrypted and processed on the server side, thus eventually exhausting CPU power, resulting into service outage. In another form which takes place at layer-3, the TCP port 443 is bombarded with bogus fragmented packets, creating similar effect.
Protecting FOSS systems
In the FOSS world, cryptography is mainly used on the web servers by implementing the SSL protocol. Besides, open source developers can digitally sign the code before sending to a trusted party, to prevent wire-tapping. On a web server, the very first step is to use a digital certificate from a trusted authority. It should also exhibit latest and stronger cipher algorithm, and the key length should at least be 256bit. Second step, is to protect the certificate store, which is that crucial area on the web server, where the website’s private key is stored. Only administrators and the network managers should have access to it. To protect FOSS network from brute force attacks, other network security protections should be in place, which are already discussed in previous articles of this series. While most of the critical infrastructures implement a firewall, a UTM device and powerful antivirus or anti-Trojan software, it becomes imperative to have an intrusion detection system (IDS) in place. IDS systems are capable of intercepting denial of service and brute force attacks and also help stop other critical anomalies. In case of Linux workstations, cryptography can be used to encrypt a file or entire disk too.
About the author
The author has over 18 years of experience in the field of IT hardware, networking, web technologies and IT security. Prashant is MCSE, MCDBA certified and also F5 load balancer expert. In the IT security world he is an ethical hacker and net-forensic specialist.
Prashant runs his own firm named Valency Networks in India (www.valencynetworks.com) providing consultancy in IT security design, security audit, infrastructure technology and business process management. He can be reached at prashant@valencynetworks.com.
More Relevant Links Below
Web Application Penetration Testing Services
Cloud Application Security Services
Mobile App Penetration Testing Services
REST API Penetration Testing Services
Network Security Auditing Services