Title: Built-in FOSS Security Scope of article When it comes to securing network infrastructure, it is a common trend to invest into commercial grade appliances….
Author: Prashant
Ensuring Security On Open Source Virtual Platform
Title: Ensuring Security on Open Source Virtual Platform We must thank IT virtualization as it led us to cloud technology. Today’s IT infrastructures are already…
Cyber Attacks Explained – Wireless Attacks
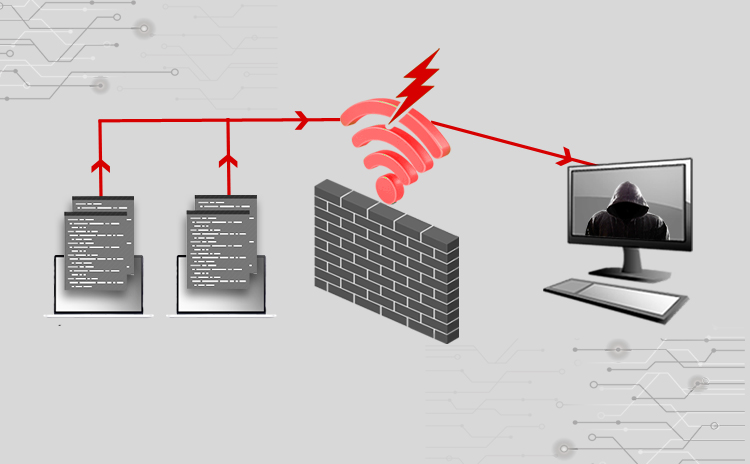
Title: Cyber Attacks Explained: Wireless Attacks Scope of article Wireless networks are everywhere, from home to corporate data centers. They make our lives easy by…
Cyber Attacks Explained – Web Exploitation
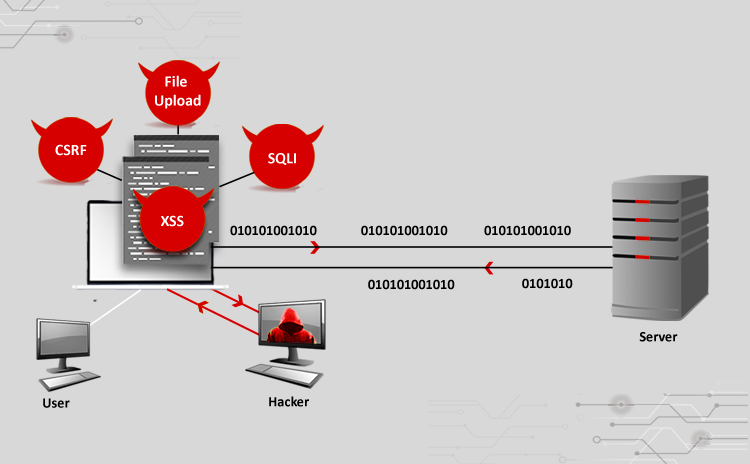
Title: Cyber Attacks Explained: Web Exploitation Scope of article Websites are no longer a means to have internet presence today, but are also used for…
Cyber Attacks Explained – Packet Spoofing
Title: Cyber Attacks Explained: Packet Spoofing Scope of article Last month we started this series of articles to cover important cyber attacks which impact critical…
Cyber Attacks Explained – Packet Crafting
Title: Cyber Attacks Explained: Packet Crafting Scope of article In the previous articles of this series we covered common attacks found in most of the…
Cyber Attacks Explained – Network Sniffing
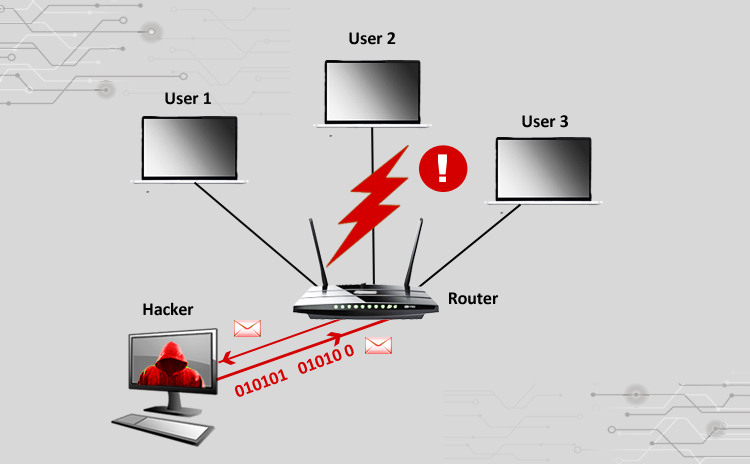
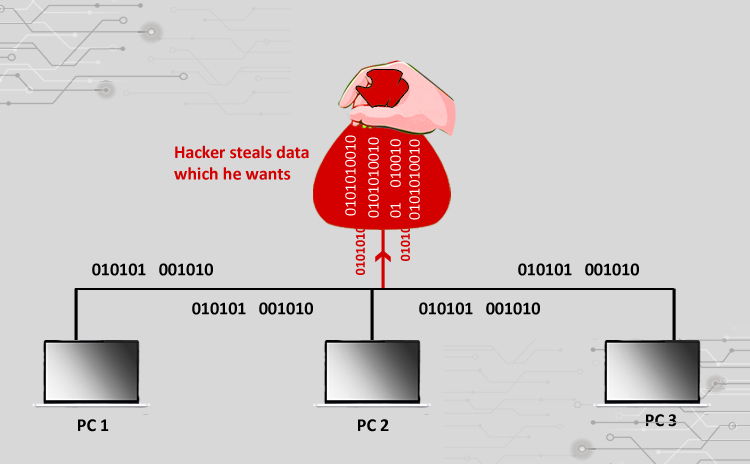
Title: Cyber Attacks Explained: Network Sniffing Scope of article Since we started this series of articles on various cyber attacks, so far we have learnt…
Cyber Attacks Explained – Man In The Middle Attack
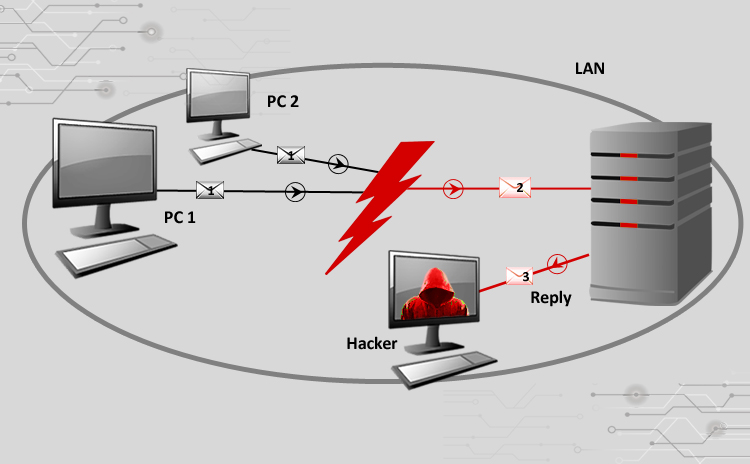
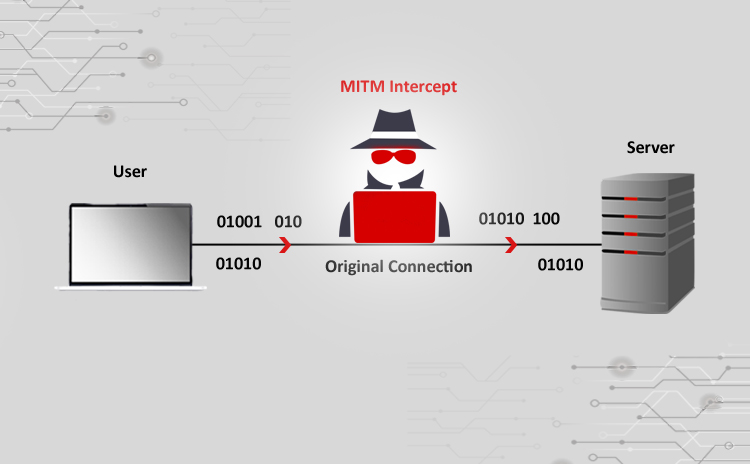
Title: Cyber Attacks Explained: Man In The Middle Scope of article While we are receiving encouraging feedbacks for this series of articles, we thought of…
Cyber Attacks Explained – DoS and DDos
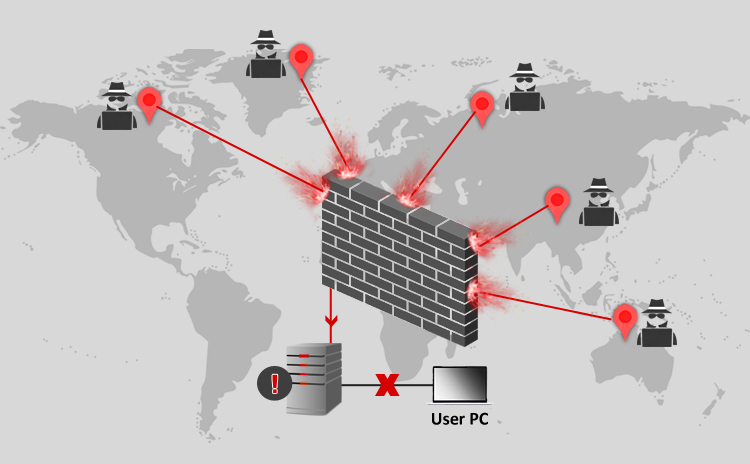
Title: Cyber Attacks Explained: DoS and DDos Scope of article With this article we are starting a new series to cover important cyber attacks which…
Cyber Attacks Explained – DNS Invasion
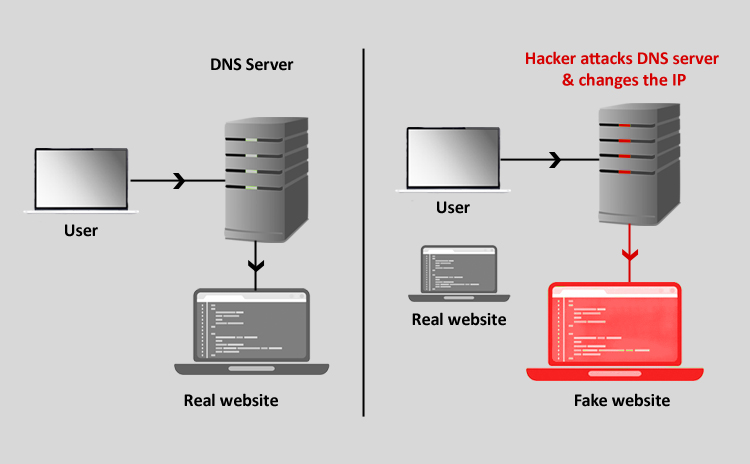
Title: Cyber Attacks Explained: DNS Invasion Scope of article We always read in the news about some website defaced and its pages changed to reflect…