Title: Top 10 Web Log Analyzers Scope of article Today’s web hosting data centers are deployed with multiple web servers, running heterogeneous operating systems architecture….
Open Source Security
Top 10 Security Vulnerability Scanners
Title: Top 10 Security Vulnerability Scanners Scope of article Gone are the days when a network administrator would sit in his cozy datacenter room, sip…
Top 5 Security Assessment Tools
Title: Top 5 Security Assessment Tools While performing a vulnerability scanning against a network, it needs to be done from within the network as well…
Top 3 Network Monitoring Tools
Title: Top 3 Networks Monitoring Tools Scope of article In a well managed IT infrastructure, network monitoring acts as eyes and ears to spot problems…
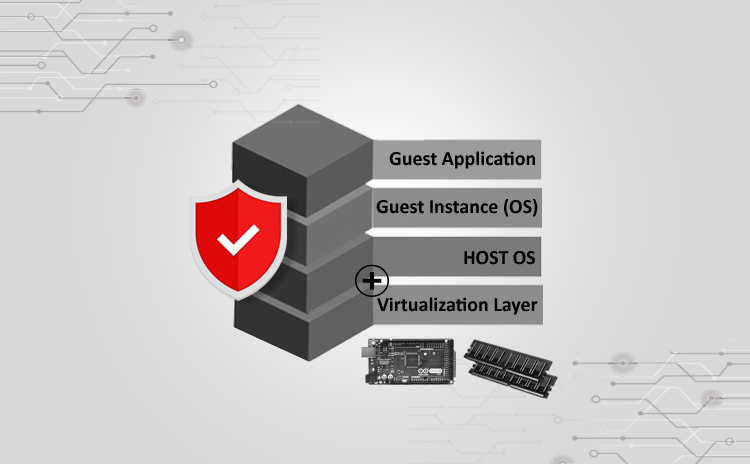
Securing Xen Virtualization
Title: Securing Xen Virtualization Scope of article The concept of virtualization was created in IT industry to achieve easy management and maintenance of the server…
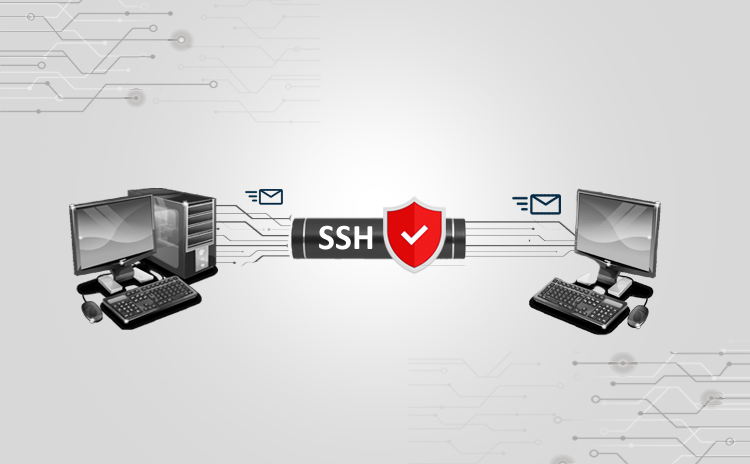
Securing SSH Service
Title: Securing SSH Service Scope of article SSH service is very widely used in the open source infrastructure setups. Due to its small footprint on…
Securing MySQL Server
Title: Cyber Attacks Explained: Securing MySQL Server Scope of article MySQL server is widely used in the open source world. Let it be a small…
Open Source Security Tools – TrueCrypt
Title: Open Source Security Tools: TrueCrypt Scope of article In the last article we talked about Tripwire, which ensure the integrity of file system. In…
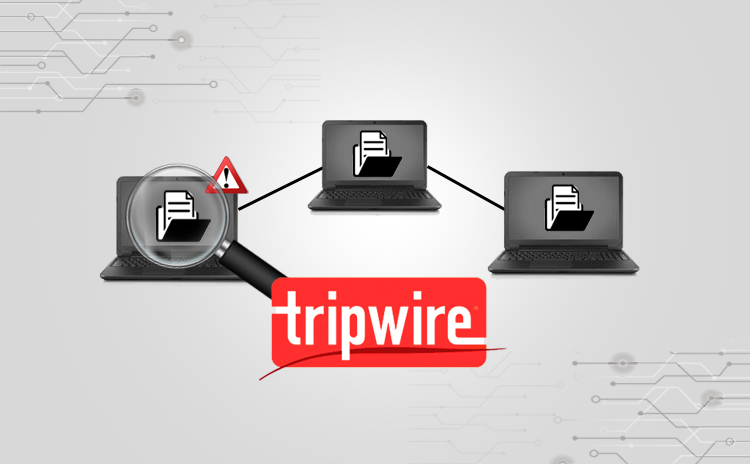
Open Source Security Tools – Tripwire
Title: Open Source Security Tools: Tripwire Scope of article With the increasing demand of cyber security in open source world, it has become important to…
FOSS Built-In Security
Title: Built-in FOSS Security Scope of article When it comes to securing network infrastructure, it is a common trend to invest into commercial grade appliances….