In 2018, one of India’s largest banks, the State Bank of India (SBI), faced a significant phishing attack targeting its customers nationwide. The attack aimed…
Year: 2023
Phishing Story: JP Morgan
In 2019, a large multinational corporation known for its financial services, JPMorgan Chase, experienced a significant phishing attack that targeted its customers—the attack aimed to…
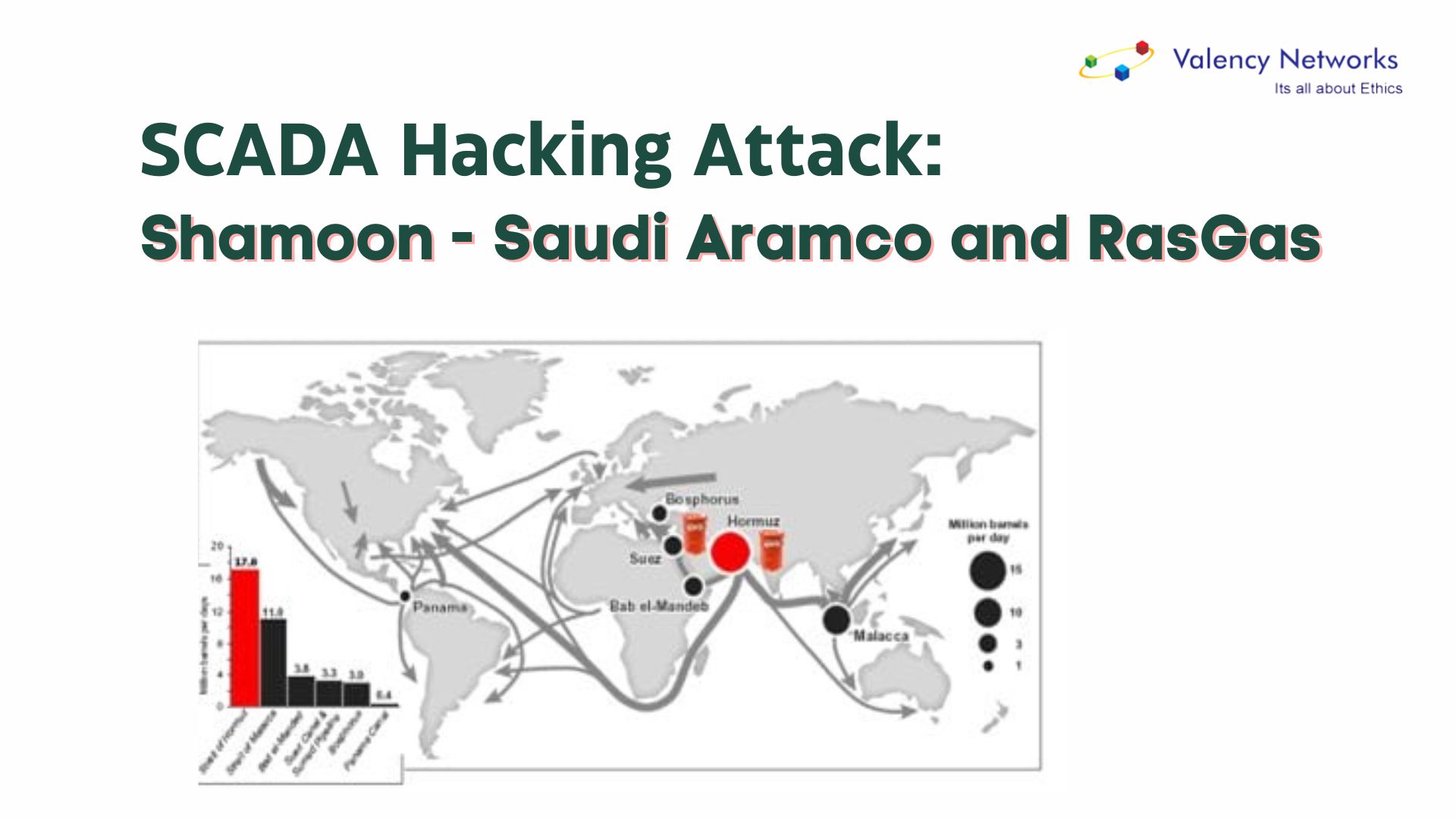
SCADA Security Hacking Story: Shamoon – Saudi Aramco and RasGas
In 2012, Saudi Aramco, the prominent global energy company, encountered a severe and unprecedented cyber incident that sent shockwaves through the industry. The company fell…
SCADA Security Hacking Story: Duqu, Flame, and Gauss
In 2011, Hungarian cyber security researchers made a significant discovery of three information-stealing malware: Duqu, Flame, and Gauss. This malware was found to be related…
Phishing Story: ICICI
In 2017, a central Indian bank, ICICI Bank, faced a significant phishing attack that targeted its customers. The attack aimed to deceive customers into revealing…
Phishing Story: Google
In 2016, one of the world’s largest and most prominent technology companies, Google, fell victim to a sophisticated phishing attack. The attack targeted many users,…
Phishing Story: Flipkart
In 2020, a leading Indian e-commerce company, Flipkart, experienced a significant phishing attack that targeted its customers. The attack aimed to deceive users into revealing…
Process & Benefits of Compliance Audits
Compliance audits are systematic reviews conducted by organizations to assess whether their operations, processes, and activities adhere to applicable laws, regulations, policies, and industry standards….
Difference between VAPT and Red Teaming
In the realm of cybersecurity, there are numerous methodologies employed to assess and enhance the resilience of an organization’s digital infrastructure. Two commonly discussed practices…
Comparison of ISO27001 and Cyber Essentials
ISO 27001 and Cyber Essentials are popular frameworks for managing and improving organisation information security. While they share some similarities, they differ in scope, requirements,…