PIPEDA is the Personal Information Protection and Electronic Documents Act, Canada’s federal privacy law for private sector organisations. Compliance with PIPEDA brings several benefits to…
Year: 2023
The Psychology behind disliking SOC2 Compliance
The American Institute of CPAs (AICPA) established SOC 2, Service Organisation Control 2, a widely accepted auditing standard. It focuses on the controls and processes…
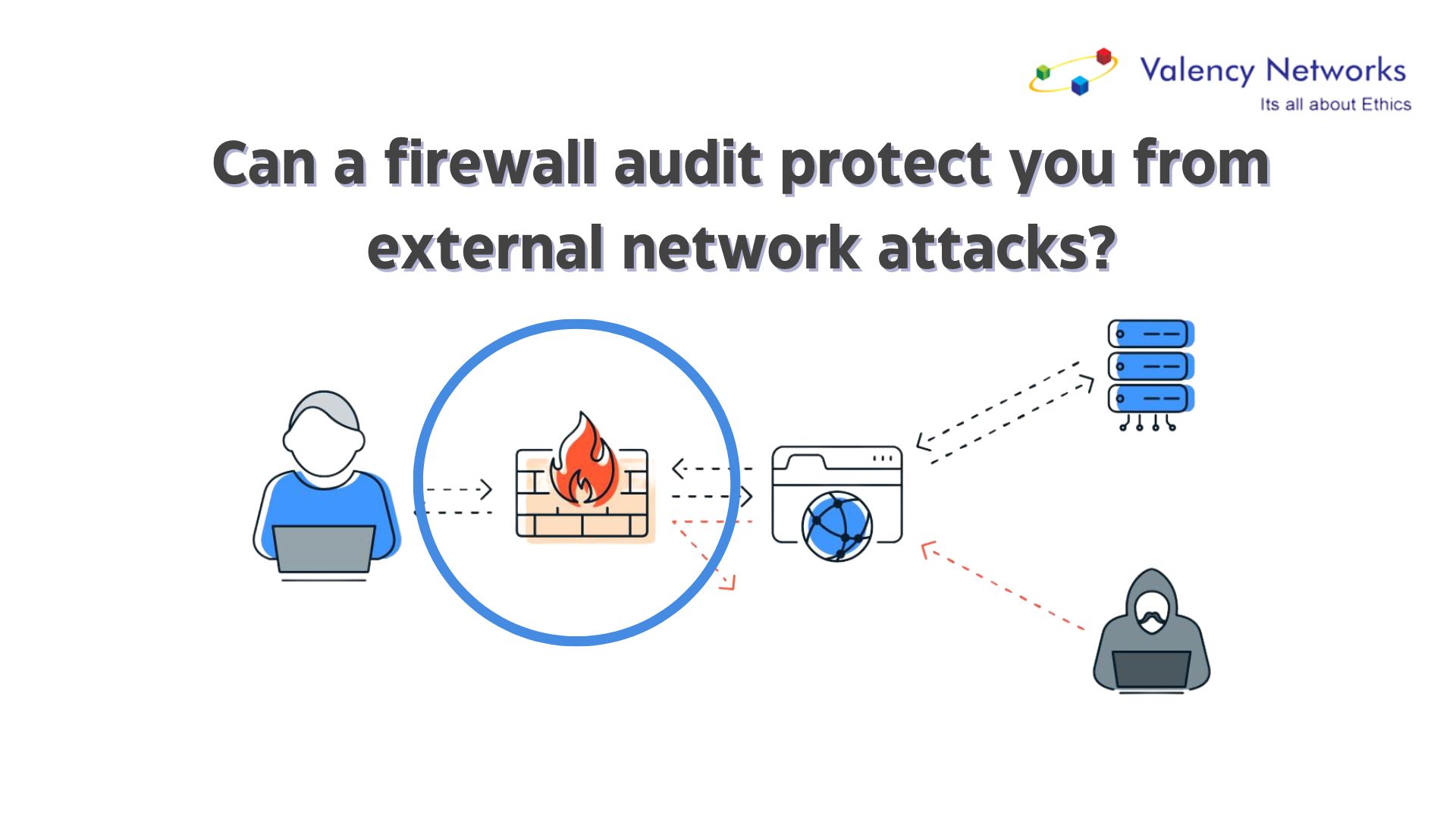
Can a firewall audit protect you from external network attacks?
Firewall audits play a crucial role in protecting networks from external network attacks by assessing the effectiveness and configuration of firewalls. While a firewall acts…
Why is Firewall Audit Important?
A firewall audit systematically evaluates its configuration and effectiveness to ensure it is properly configured, secure, and aligned with the organization’s security policies and objectives….
Why Patch Management is important?
Patch management is a critical process that involves identifying, deploying, and managing updates or patches for software applications, operating systems, firmware, and other components of…
How to set ISO27001 objectives?
How to set ISO27001 objectives? ISO 27001 is an international information security management system (ISMS) standard. It systematically manages sensitive company information, ensuring its confidentiality,…
Benefits of Cyber Essentials
Cyber Essentials is a cybersecurity certification program developed by the UK government to help organizations protect themselves against common cyber threats. The program aims to…
Comparison of ISO27001 and TISAX
ISO 27001 is an international information security management system (ISMS) standard. It systematically manages sensitive company information, ensuring its confidentiality, integrity, and availability. ISO 27001…
Comparison of ISO27001:2013 and ISO27001:2022
In the realm of information security, ISO 27001 stands as a powerful standard. It provides organizations with a robust framework to protect their valuable data…
Comparison of HIPAA and GDPR Compliance
HIPAA (Health Insurance Portability and Accountability Act) and GDPR (General Data Protection Regulation) are essential data privacy and security regulations. While HIPAA primarily focuses on…