In 2013, an incident occurred in New York involving the intrusion of Iranian hackers into a small dam known as Bowman Dam. While the nature…
SCADA Security
SCADA Security Hacking Story: Target Stores
SCADA system attacks typically occur through an organization’s business network, impacting the remote control systems. However, in 2013, hackers took a different approach by targeting…
SCADA Security Hacking Story: Stuxnet
In 2010, Stuxnet emerged as one of the most intricate malware ever discovered. It infiltrated control system networks, leading to speculations that it severely impacted…
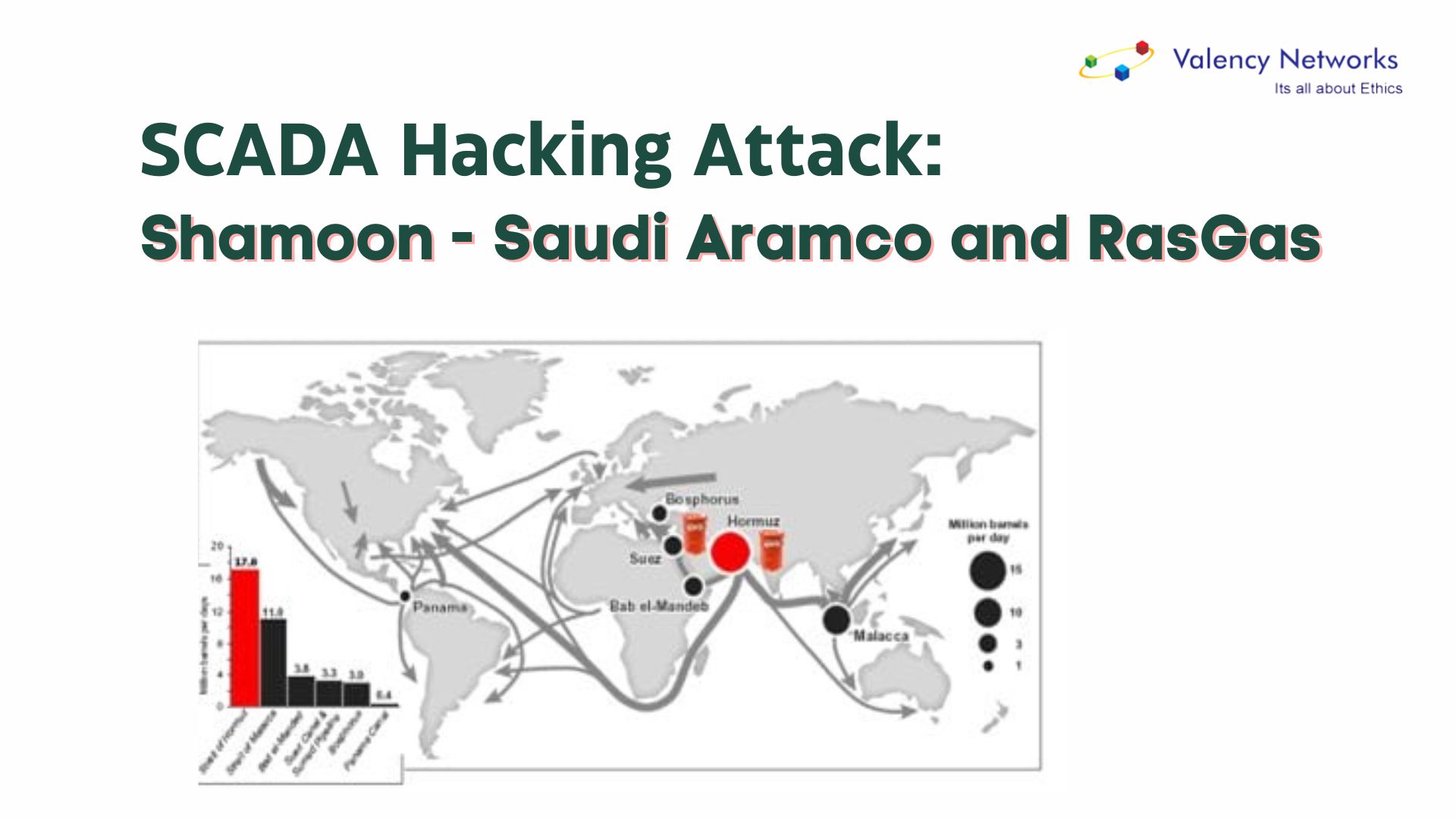
SCADA Security Hacking Story: Shamoon – Saudi Aramco and RasGas
In 2012, Saudi Aramco, the prominent global energy company, encountered a severe and unprecedented cyber incident that sent shockwaves through the industry. The company fell…
SCADA Security Hacking Story: Duqu, Flame, and Gauss
In 2011, Hungarian cyber security researchers made a significant discovery of three information-stealing malware: Duqu, Flame, and Gauss. This malware was found to be related…
Fundamentals Of SCADA Security – 4
Security threats to SCADA and RTU The SCADA systems which tie up together the decentralized facilities like; oil and gas pipelines, waste water collection, power…
Fundamentals Of SCADA Security – 3
Introduction to RTU The remote terminal unit abbreviated as RTU is an electronic device that is controlled through the use of a microprocessor. It helps…
Fundamentals Of SCADA Security – 2
Introduction to PLC Programmable logic controllers abbreviated as PLC are said to be industrial computers that help monitor inputs, make relevant decisions on the basis…
Fundamentals Of SCADA Security – 1
Introduction to SCADA Supervisory Control and Data Acquisition abbreviated as SCADA is regarded as a complete system constituting of hardware and software components that helps…