- Penetesting Industry 4.0 IoT Prototype – 5 - 18/04/2020
- Penetesting Industry 4.0 IoT Prototype – 4 - 18/04/2020
- Penetesting Industry 4.0 IoT Prototype – 3 - 18/04/2020
Penetesting Industry 4.0 IoT Prototype
Why we did this?
Valency Networks is established into VAPT market but walking path of making IoT based industries secure. There is a great deal of confusions around IoT and Industry 4.0, in terms of how those interact, what are their security challenges, what methods need to be followed etc. People are rather confused on this, and the only way to prove them the compelling reasons to consider security in IoT, is to show them a proof of concept. This article and embedded videos show exactly that.
As we all know Industry 4.0 stands for the fourth Industrial revolution that encompasses modern technologies such as Industrial Automation, Cyber-Physical Systems (CPS), Internet of Things (IoT), Industrial Internet of Things (IIoT), Cloud Computing, Artificial Intelligence, etc. to enhance the quality and quantity of production. In simpler terms, Industry 4.0 is an amalgamation of many advance technologies which industry uses along with IoT to facilitate remote control and monitoring to enable optimized & quick operations supported by business analytics.
Cyber Security Threats for Industry 4.0
Integrated & complex environment of Industry 4.0 is perfect opportunity for hackers to attack at different layers and cause heavy damage to plant and people. Hence the cybersecurity threats of Industry 4.0 must consider IT Security (Information Technology Security), OT Security (Operational Technology Security), and IoT Security (Internet of Things Security).
Industry 4.0 uses smart devices such as smart sensors and motors that are directly connected to the digital manufacturing network. Hence even a small vulnerability can provide an opportunity for hacker to move laterally across the manufacturing network and access the other interconnected devices or systems such as the IoT Platforms, Web Applications or Cloud Applications of the industry which can lead to loss or theft of confidential data and IP (Intellectual Property) assets while also causing malfunctioning of the ongoing processes in the industry.
Similarly, if attackers gain access to any of the IoT platforms or Web applications designed for controlling the operations of the industry they could further penetrate into the system network and steal sensitive data or also cause the system to crash or damage it permanently. Malwares like ‘Bickerbot’ are known to have the ability to exploit the hard-coded password in IoT devices which can cause PDOS (Permanent Denial of Service) attack, thus compromising the critical devices in the system. Hence, understanding how a potential cyber-attack is executed is vital in order to fix the critical security flaws in the industrial system.
Replicating the scenario of Industry 4.0
In order to demonstrate some typical cyber security threats and Vulnerabilities, we replicated the scenario of Industry 4.0. by creating a prototype of an industry 4.0 using Raspberry Pi being used as a controller. The webpage as shown below was created for remote control and monitoring functions. This prototype had IR Sensor, DC Motors and LEDs that represent the devices used for the functioning of a conveyer-based assembly line.
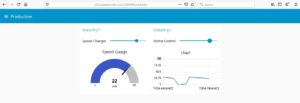
Fig 1: Control and Monitor Web App for an Industry to be used on the same network
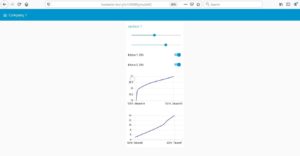
Fig 2: Control and Monitor Web App accessible from mobile phone from a remote network