SOC 2 refers to a set of audit reports that demonstrate the level of conformity of information security controls’ design and operation against a set…
What is the difference between ISO 27001 and 27002
he primary difference between ISO 27001 and ISO 27002 is that ISO 27002 is intended to be used as a guide for selecting security controls…
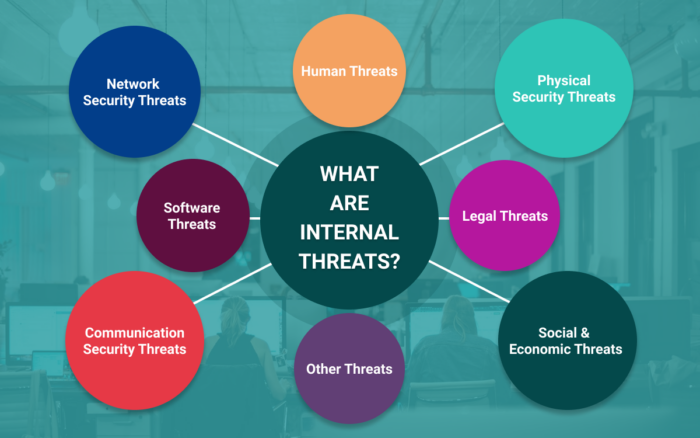
Why is it important for companies to plan for internal threats?
Internal threats refers to risks to data that stem from inside the organization due to poorly managed security of network, resources, assets and much more….
How pentesting differs in various operating systems?
Different operating systems are based upon different ideologies. Linux based operating systems like Kali, Parrot OS, Backbox Linux are specifically made with certain inbuilt tools,…
What are the 4 types of IT security?
Every organization has some data to protect. The data, if stolen can cause huge damage to an organization both reputational and financial. Hence, it becomes…
What are major cyber security risks?
Cyber security risk is a risk that could potentially harm the confidentiality, integrity and availability of the data through an attack either on asset, network…
Why ISO27001 Internal Audit Should Not Be CheckList Based?
All ISO27001 certified companies (not just compliant but certified) certainly have a stronger foot while competing for contracts and customers in the market. But being…
Real Life OT Security Incidents
Case 1: Colonial pipeline ransomware attack Location: Houston, Texas The Colonial Pipeline ransomware attack was one of the most significant attacks in 2021. The attack…
Introduction to OT Security
Operational Technology uses hardware and software to monitor and control physical processes, devices, and infrastructure. They use specialized protocols and software to interface with legacy…
Difference between OT and IoT
The term “operational technology” (OT) refers to a particular class of hardware and software whose function is to keep track of and manage the operation…