- XML-RPC Vulnerability – Risk and Mitigations - 11/10/2024
- Choosing testing environment for VAPT - 24/06/2024
- What is the ideal web session timeout? - 15/05/2023
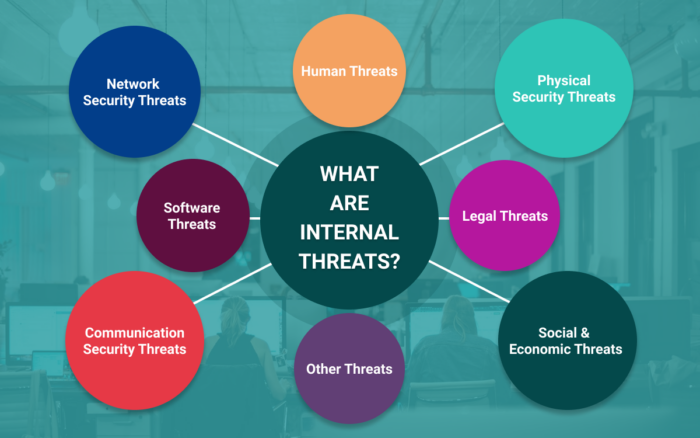
Internal threats refers to risks to data that stem from inside the organization due to poorly managed security of network, resources, assets and much more. According to Gartner, majority of attacks happen from within the organization.
Listing down a few of the factors that contribute to majority of the attacks.
Awareness: It all starts from how aware and informed employees are with respect to information security. Employees should be considered as important assets rather than weak links since they access, process and touch the data. They should be made conscious of the risks and threats that are lingering around and should be trained on how to handle data responsibly.
Access control: It is important to audit and analyse the level of access given to employees and management. Employees should be given access on least privilege basis. All accesses should be verified and terminated when an employee leaves the organization or when they are no longer necessary to an employee.
VAPT: A timely vulnerability analysis of all the network devices and infrastructure can play an important role when tightening the security. It is important to analyse what traffic is coming in and going out of the organization and blocking the malicious traffic immediately. An unpatched system and an unwanted open port is enough for an attacker to get inside the network and do the damage