In 2017, a central Indian bank, ICICI Bank, faced a significant phishing attack that targeted its customers. The attack aimed to deceive customers into revealing…
Phishing Story: Google
In 2016, one of the world’s largest and most prominent technology companies, Google, fell victim to a sophisticated phishing attack. The attack targeted many users,…
Phishing Story: Flipkart
In 2020, a leading Indian e-commerce company, Flipkart, experienced a significant phishing attack that targeted its customers. The attack aimed to deceive users into revealing…
Process & Benefits of Compliance Audits
Compliance audits are systematic reviews conducted by organizations to assess whether their operations, processes, and activities adhere to applicable laws, regulations, policies, and industry standards….
Difference between VAPT and Red Teaming
In the realm of cybersecurity, there are numerous methodologies employed to assess and enhance the resilience of an organization’s digital infrastructure. Two commonly discussed practices…
Comparison of ISO27001 and Cyber Essentials
ISO 27001 and Cyber Essentials are popular frameworks for managing and improving organisation information security. While they share some similarities, they differ in scope, requirements,…
Benefits of Canada PIPEDA compliance
PIPEDA is the Personal Information Protection and Electronic Documents Act, Canada’s federal privacy law for private sector organisations. Compliance with PIPEDA brings several benefits to…
The Psychology behind disliking SOC2 Compliance
The American Institute of CPAs (AICPA) established SOC 2, Service Organisation Control 2, a widely accepted auditing standard. It focuses on the controls and processes…
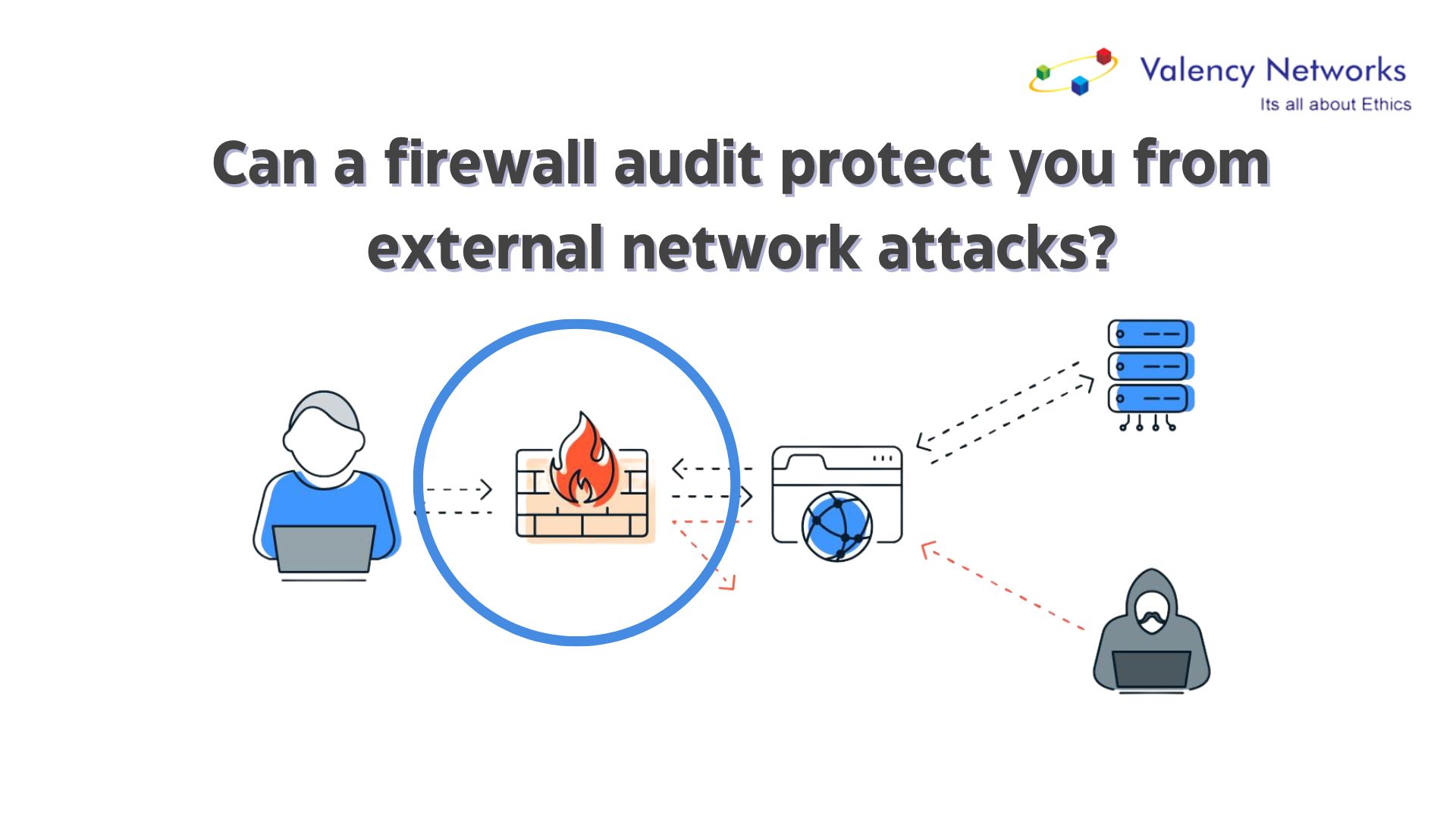
Can a firewall audit protect you from external network attacks?
Firewall audits play a crucial role in protecting networks from external network attacks by assessing the effectiveness and configuration of firewalls. While a firewall acts…
Why is Firewall Audit Important?
A firewall audit systematically evaluates its configuration and effectiveness to ensure it is properly configured, secure, and aligned with the organization’s security policies and objectives….