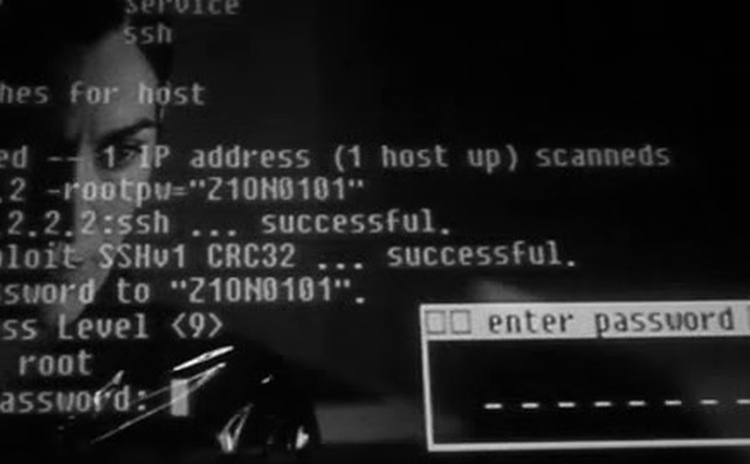
“Top Threats to Cloud Computing”, provides needed background to help organizations in making refined risk management decisions regarding their cloud adoption strategies. #Threat1- Misuse of…
Day: February 7, 2020
Mobile Apps: Owner’s Pride, Hacker’s Gain
Did you know that a mobile application, on an average has 9 vulnerabilities? Multiply that by the average number of installed applications (26.2) and you…
Vulnerability Assessment – Automated v/s Manual Testing
We all know that there are 3 distinct pillars of software testing – functional testing, security testing and performance testing. There are multiple tools out…
Why Hackers Like The Healthcare Industries
To the question in title, if I was a hacker I would ask myself “why not”?. Its simple really. Hackers always go for the data…
Why Manufacturing Industry is Prone to Ransomware Attacks
2017 was clearly an year of ransomwares. We saw Locky, Petya, GoldenEye, Wannacry and their variants. The cases were pretty straight forward – Machines get…
Learnings From The Cyber Attacks on Banking Industry
Year 2018 was full of cyber-attacks and the most serious news was about well-orchestrated cyber-attacks on banking industry. No matter how much awareness is generated,…
How To Select Your ISO 27001 Implementation Partner
While choosing ISO27001 consultant or implementation partner, usually companies do not know the basis on which they should select the right vendor. Due to lack…
Considering ISO27001 for IoT Security Readiness
Manufacturing companies are heading towards IoT (Internet of Things) in a fast pace. While most of the companies are focused on automating their production processes,…