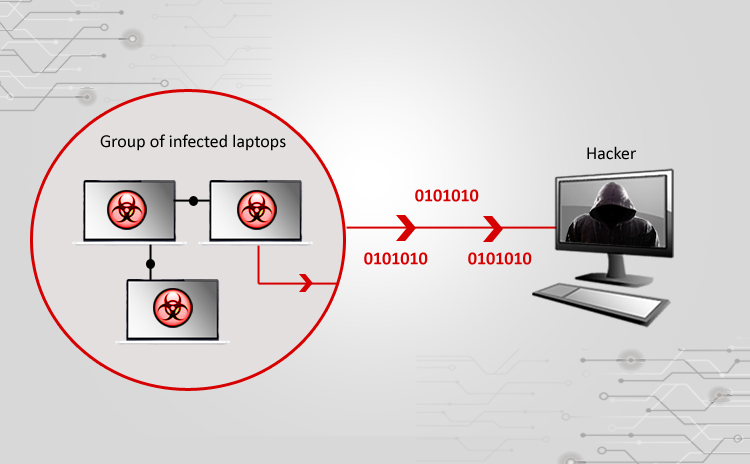
Title: Cyber Attacks Explained: Botnet Army Scope of article This month we are going to learn about yet another dangerous type of attack which is…
Month: January 2020
Cyber Attacks Explained – Authentication Attacks
Title: Cyber Attacks Explained: Authentication Attacks Scope of article In the previous article, we dealt with man in the middle attack whereby a hacker can…
Comparison of ISO27001 and SOC2 Compliances
ISO 27001 and SOC 2 COMPARISON Background There is an increased need for service organizations to provide assurance, trust and transparency over their controls to…
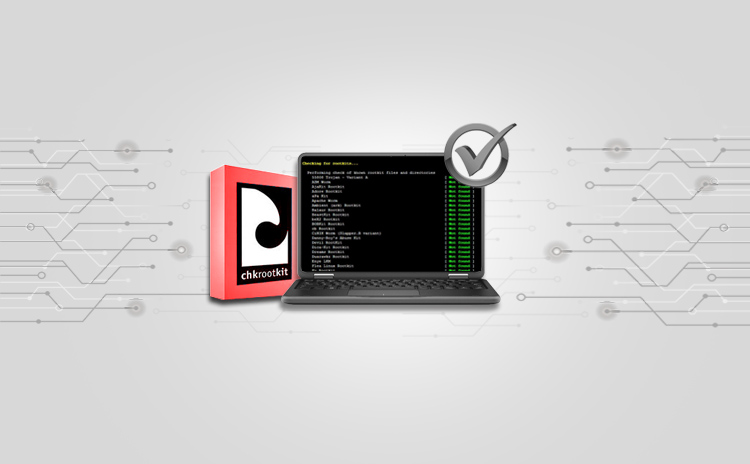
CHKRootKit – Eliminate The Enemy Within
Title: CHKRootKit : Eliminate The enemy within Scope of article Last month we learnt about the technical components that form the rootkits. We also discussed…
Benefits of OpenSSH
Title: Benefits of OpenSSH Scope of article SSH service is very widely used in the open source infrastructure setups. Due to its small footprint on…
Basics of Vulnerability Assessment and Penetration Testing
Basics of Vulnerability Assessment and Penetration testing As the number of web and mobile applications is increasing the cyber attacks are increasing everyday too. World…
Angular JS Security Fundamentals
AngularJS Vulnerability Assessment on Web ⦁ Introduction: In this era of digitization, technology has been changing at a rapid pace and businesses are always looking…
Android Security Risks
Scope of article Open source world loves Android operating system. It is surely a gift from google, that provides cutting edge and versatile mobile development…
PCIDSS Compliance For Mobile Application
PCIDSS COMPLIANCE FOR MOBILE APPLICATION WHAT IS PCIDSS PCI DSS (Payment Card Industry Data Security Standards) standard developed in order to ensure the security of…
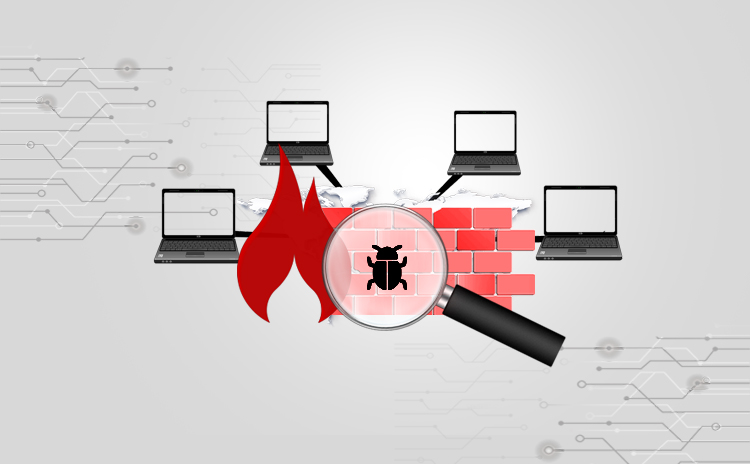
How To Pentest Firewall
How to pen test a firewall externally Firewall is a device or software which is responsible for filtering traffic of network. It can be implemented…