Title: Cyber Attacks Explained: Securing MySQL Server Scope of article MySQL server is widely used in the open source world. Let it be a small…
Day: January 6, 2020
PHP Security Best Practices-2
PHP security PHP is a powerful and flexible tool. This power and flexibility comes from PHP being a very thin framework sitting on top of…
PHP Security Best Practices – 1
Title: PHP Security Scope of article In the open source world, PHP programming is always given first choice due to its availability and flexibility. It…
Open Source Security Tools – TrueCrypt
Title: Open Source Security Tools: TrueCrypt Scope of article In the last article we talked about Tripwire, which ensure the integrity of file system. In…
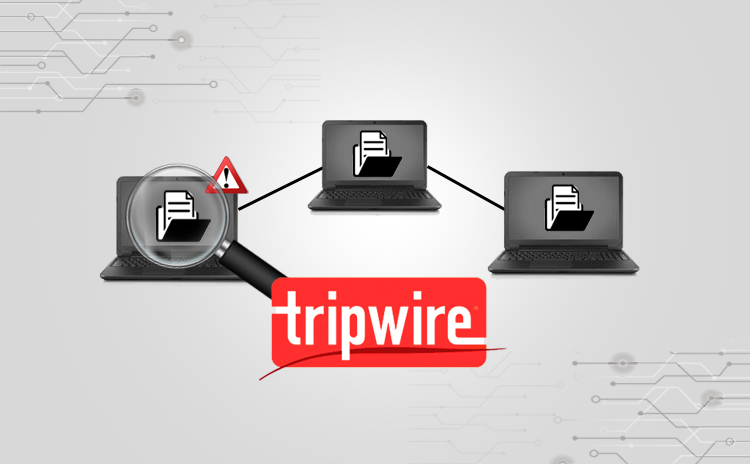
Open Source Security Tools – Tripwire
Title: Open Source Security Tools: Tripwire Scope of article With the increasing demand of cyber security in open source world, it has become important to…
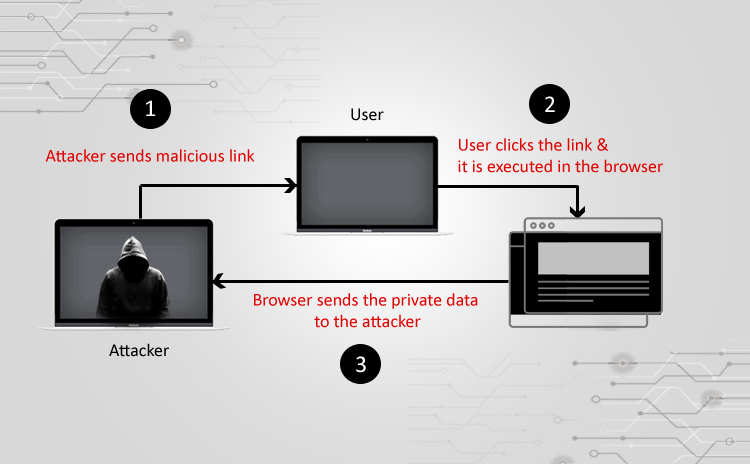
How to handle Non Persistent XSS injection
How to handle Non Persistent XSS injection Cross-site scripting (XSS) attacks are a type of injection, in which malicious scripts are injected in the client…
FOSS Built-In Security
Title: Built-in FOSS Security Scope of article When it comes to securing network infrastructure, it is a common trend to invest into commercial grade appliances….
Ensuring Security On Open Source Virtual Platform
Title: Ensuring Security on Open Source Virtual Platform We must thank IT virtualization as it led us to cloud technology. Today’s IT infrastructures are already…
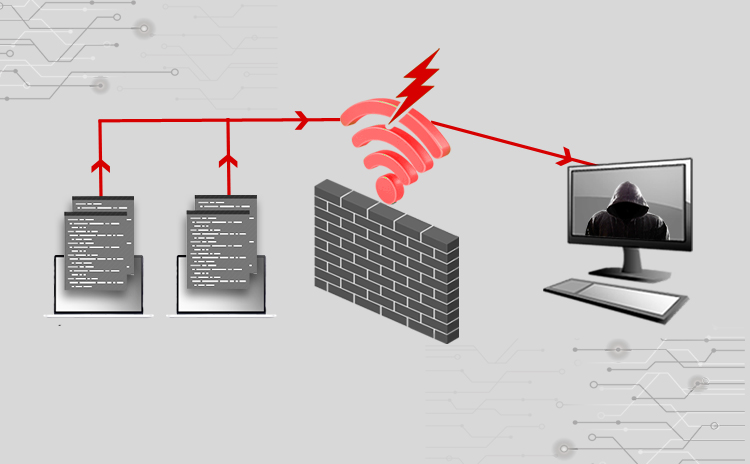
Cyber Attacks Explained – Wireless Attacks
Title: Cyber Attacks Explained: Wireless Attacks Scope of article Wireless networks are everywhere, from home to corporate data centers. They make our lives easy by…
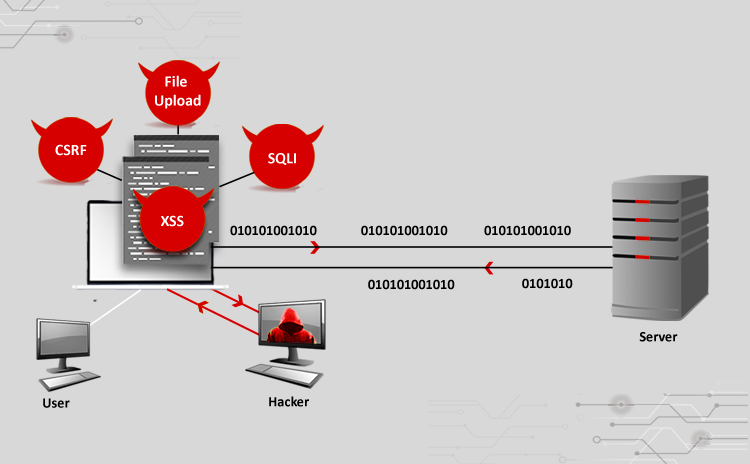
Cyber Attacks Explained – Web Exploitation
Title: Cyber Attacks Explained: Web Exploitation Scope of article Websites are no longer a means to have internet presence today, but are also used for…