IOT Vulnerability Assessment and Penetration Testing
IOT, which is a buzzword in many business industries and also its becoming one of the most important trend in the history of the software industry.
IoT are physical objects that connect wirelessly to a network and has the ability to transmit data they are equipped with the sensors which are able to collect and share data with each other which are connected via internet, devices communicate with each other which are wirelessly connected to each other this makes IoT different from other electronic devices.

Light turns ON
In our case the IOT contrivance is the keenly intellectual lightning technology designed for energy efficient. This may include high efficiency fixtures and automated controls that make adjustments predicated on conditions such as occupancy or daylight availability. With the avail of the sensor it determines whether the lights should be ON or OFF.
So in this case we check the susceptibility of the contrivance because if the contrivance is vulnerably susceptible the assailant can make the contrivance work however he requires.
For example1: If the smart lighting system is implemented in xyz organization and the organization is closed on Sundays the attacker can hack the smart lightning device and make it turn ON even on Sundays so that organization face electric loss.
Example 2: Suppose in an organization people are working and simultaneously cause a perpetual blackout of millions of consumer light bulbs which are disturbing and annoying scenario for the employees which is caused by the attackers hacking of the device.
What are the vulnerabilities found?
• Almost every IoT have a web server built in it which host a web app for managing the device. Like many web server/app, there may be flaws in the code that allow the device to be attacked. As these are connected devices weaknesses can be exploited remotely. Which is the Insecure web interface.
• While there are often weaknesses in the implementation of authentication/authorization certain features that are provided must be utilized.
• The IoT contrivances which are utilized have inadequate security features because the contrivance is not secured and the features doesn’t avail in this case so the contrivances should attest the PIN NUMBER OR utilizer name or password for the security and we should be able to cull the encryption method
• IoT device sends private information over insecure protocol by which unknown can spy through, the information can be confidential ,private which can be exposed to attacker hence there is lack of transport encryption.
• If information on the device is not encrypted at rest, and people have access to the device, your personal information is at risk. Which is privacy concerns, for example if there is any secret task given to two individuals in the college and the task what other friend is doing got discovered by the her friend this is because tablet was configured to share information with her and there is no privacy in your own personal life.
• Devices which are connected to the cloud have cloud interface management which represents another potential security weakness.
• Now a days many IoT devices is linked with the mobile interface as every one uses their mobile which becomes more frequent and hence building secure software is very difficult for the restricting remote attacker to access.
Tools used are ~
By using tool like NMAP, NESSUS AND METASPLOIT further assessment and testing could be done which prevents and detects the vulnerability and assessment of the device
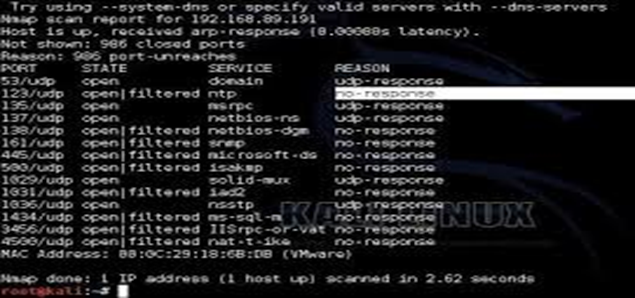
1] NMAP ~ Nmap (Network Mapper) is a security scanner, used to discover hosts and services on a computer network, thus building a “map” of the network. To accomplish its goal, Nmap sends specially crafted packets to the target host(s) and then analyzes the responses.
The software provides a number of features for probing computer networks, including host discovery and service and operating-system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection and other features. Nmap can adapt to network conditions including latency and congestion during a scan. The Nmap user community continues to develop and refine the tool.
By using tool like NMAP further assessment and testing could be done and while testing the device we could elucidate, which ports are open, what is the vulnerability and what are the risks that can be avoided. This can be done by knowing the IP address of the respective device which need to be test
Features include: Host Discovery
– Port scanning
– Version detection
– OS detection
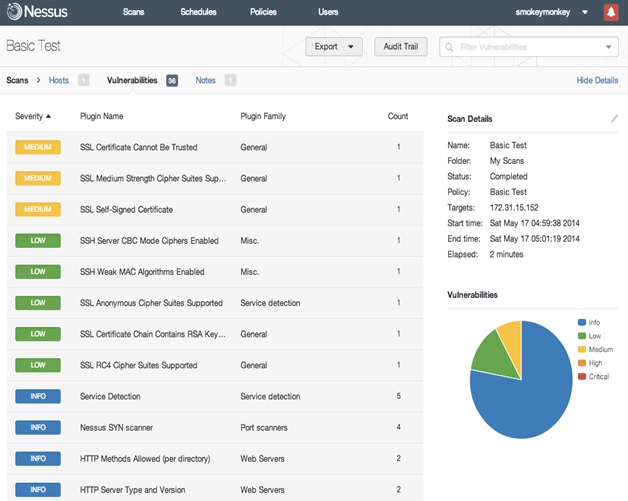
2] NESSUS ~ By using Nessus tool which is a remote security scanning tool scans a computer and raises an alert if it discovers any vulnerability that malicious hacker could uses to gain access to any computer you have connected to a network and it lists the criticality of the vulnerabilities which can be prioritized.
3] METASPLOIT ~ Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research.
Once sniffing and scanning is done it is time to go to OS and application level. It is a open source framework that performs rigorous scans against a set of IP address, it can also be useful for anti-forensics. Expert programmers can write a piece of codes exploiting a particular vulnerability and test it with metasploit to see if it gets detected. It can also be useful to test patch.
The two important terms in metasploit are ~
Exploit– To take advantage of a vulnerability, you often need an exploit, a small and highly specialized computer program whose only reason of being is to take advantage of a specific vulnerability and to provide access to a computer system. Exploits often deliver a payload to the target system to grant the attacker access to the system.
Payload– A payload is the piece of software that lets you control a computer system after it’s been exploited. The payload is typically attached to and delivered by the exploit. Just imagine an exploit that carries the payload in its backpack when it breaks into the system and then leaves the backpack there. Yes, it’s a corny description, but you get the picture.
How can IoT be prevented From Hacking
• The iot devices need to be taken care like mobile phones, tablets, home computer, laptops etc strong password should be set so that brute force attack can be prevented, reading the given instructions carefully for the security purpose.
• Understand your device its storage methods and how does it collect and manage data.
• Always buy the product which is secured, review the product before buying it for its security concerns. Device which runs on old protocols like SIP (Session Initiation Protocol) serve as sitting targets for easy intrusion and hacking.
• Devices which are fully automated have the higher risk of it getting attacked.
• Change the settings for security from default to customize your own personal settings keep a strong password and check for the new existing security feature.
• Some systems with known vulnerability which are easily penetrable, should be patched before a zero day exploitation occurs or else it would for worry.
• Always keep different passwords for different devices
• Make sure your Internet connection is secure.
• Make sure data which is being transferred while communication is encrypted.
• Update all firmware on iot devices through various applications like Microsoft SCCM etc to safely distribute enterprise approved software and patches It would also help to provide a unique identity key to each device that talks to your Iot hub to ensure authentication. You may choose to contact your manufacturer for providing a security certificate for your device.
OWASP Internet of Things (Iot) Top 10 List
• I1 – Insecure Web Interface
• I2 – Insufficient Authentication/Authorization
• I3 – Insecure Network Services
• I4 – Lack of Transport Encryption
• I5 – Privacy Concerns
• I6 – Insecure Cloud Interface
• I7 – Insecure Mobile Interface
• I8 – Insufficient Security Configurability
• I9 – Insecure Software/Firmware
• I10 – Poor Physical Security
What are the ways to conduct Pen test in your organization?
• The scope needs to be described
• Internal vs. external factor need to be considered
• Safe testing
• The testing done is done by who should be culled by in-house or it should be outsourced
• Culling a pen tester.
Hence for a secure connection the following measures should be taken in to consideration
Aversion:
To obviate this certain measures need to be followed ~
• Permission to probe the network should be granted to only sanctioned person.
• Company’s terms and conditions of privacy and security should be followed
• Employees at work place should not leave anything open for someone so that someone unauthorized can access through it and exploit later on.
• Software developers and hardware manufactures should ken of any security susceptibilities you locate in their software or hardware, if not already kenned by the company.
Check out IoT Security Testing Services
More Relevant Links Below
Web Application Penetration Testing Services
Cloud Application Security Services
Mobile App Penetration Testing Services
REST API Penetration Testing Services
Network Security Auditing Services