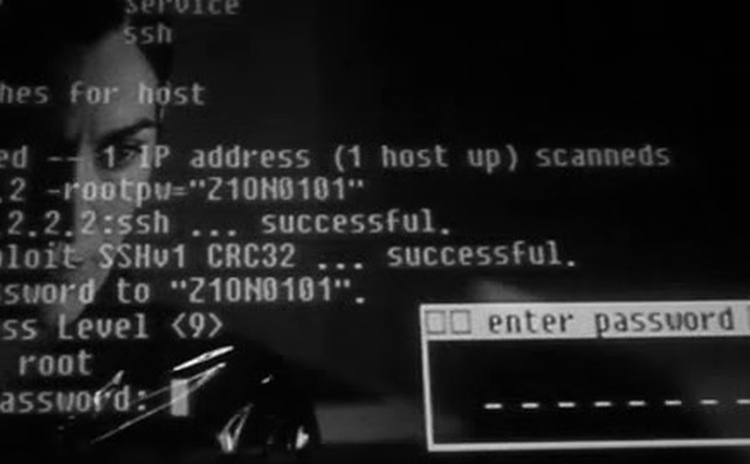
I guess most of us know why a vulnerability assessment and penetration testing needs to be performed for web apps or mobile apps. Lately I…
VAPT
Vulnerability Assessment – Automated v/s Manual Testing
We all know that there are 3 distinct pillars of software testing – functional testing, security testing and performance testing. There are multiple tools out…
Learnings From The Cyber Attacks on Banking Industry
Year 2018 was full of cyber-attacks and the most serious news was about well-orchestrated cyber-attacks on banking industry. No matter how much awareness is generated,…
SQL Injection Attack Via ORM Sink
Test cases for SQL Injection via ORM Sink What is an SQL injection? SQL injection (SQLi) is a major or one of the top OWASP…
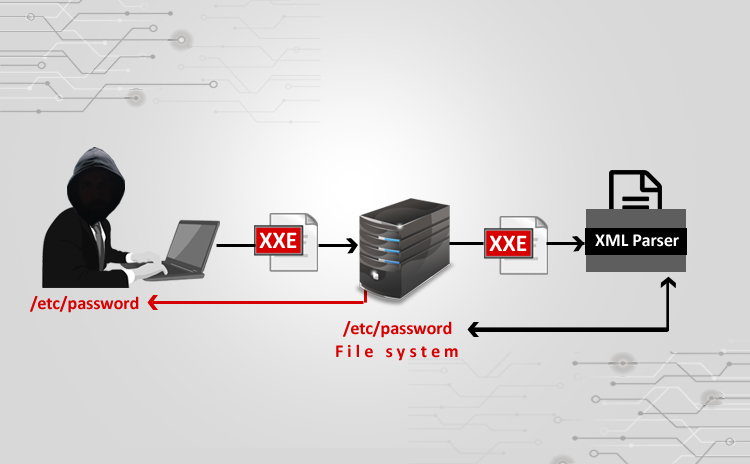
XXE Attack using Burpsuite
Steps: ⦁ I used a vulnerable website (⦁ http://testhtml5.vulnweb.com/#/popular) a)Pre-settings to be done b)Go to the vulnerable website: c) Do Forget password: ⦁ I have…
Basics of Vulnerability Assessment and Penetration Testing
Basics of Vulnerability Assessment and Penetration testing As the number of web and mobile applications is increasing the cyber attacks are increasing everyday too. World…
Android Security Risks
Scope of article Open source world loves Android operating system. It is surely a gift from google, that provides cutting edge and versatile mobile development…
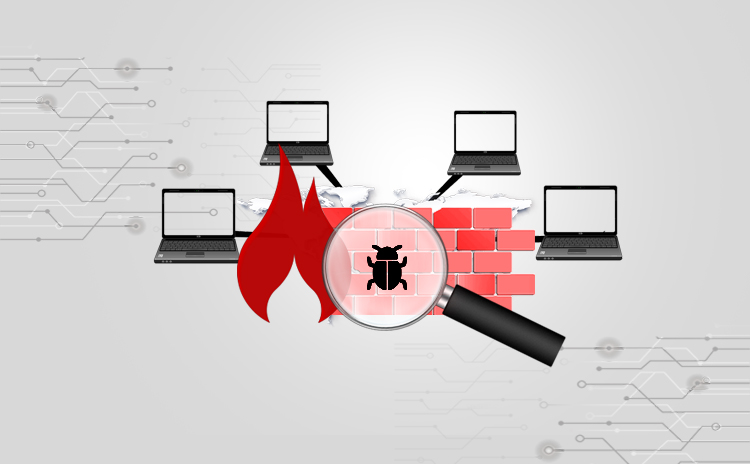
How To Pentest Firewall
How to pen test a firewall externally Firewall is a device or software which is responsible for filtering traffic of network. It can be implemented…
Fundamentals Of HTTP Headers And Web Application Security
Fundamentals of HTTP Headers and Web Application Security The notorious targets for all sorts of cyber attacks can be zeroed down to the web applications….
E-commerce Website Pentesting Final
How to pentest e-commerce website Setting up an E-commerce system is a complex process. It is necessary to be protected and customer privacy at the…