Title: Cyber Attacks Explained: Device Evasions Scope of article This is the last installment of the year long series of cyber attacks articles. As we…
Cyber Attacks Explained
Cyber Attacks Explained – Database Hacking
Cyber Attacks Explained: Database Hacking Scope of article In this article we are going to delve into database security attacks. Database is the heart of…
Cyber Attacks Explained – Cryptographic Attacks
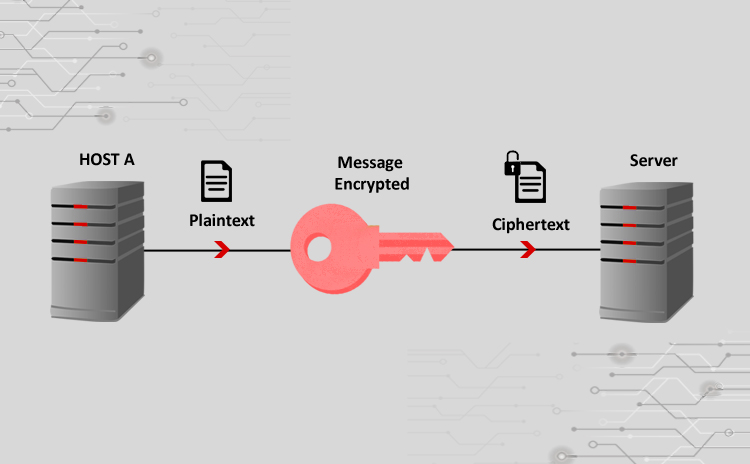
Title: Cyber Attacks Explained: Cryptographic Attacks Scope of article Cryptographic solutions are used to encrypt data transmission over wireless or wired protocols. Unfortunately these techniques…
Cyber Attacks Explained – Botnets
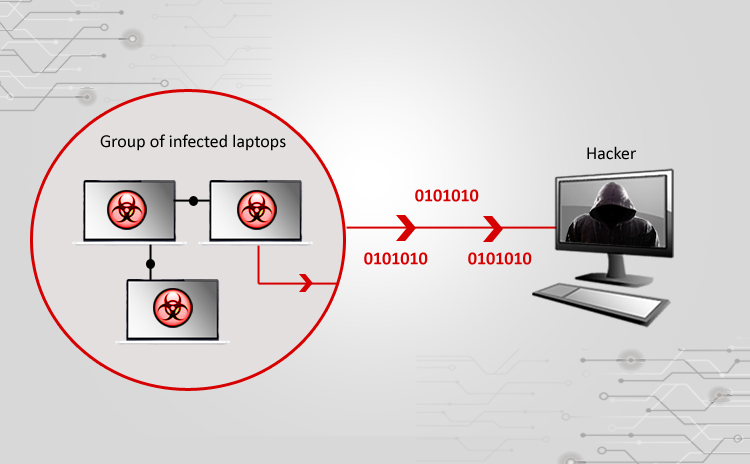
Title: Cyber Attacks Explained: Botnet Army Scope of article This month we are going to learn about yet another dangerous type of attack which is…
Cyber Attacks Explained – Authentication Attacks
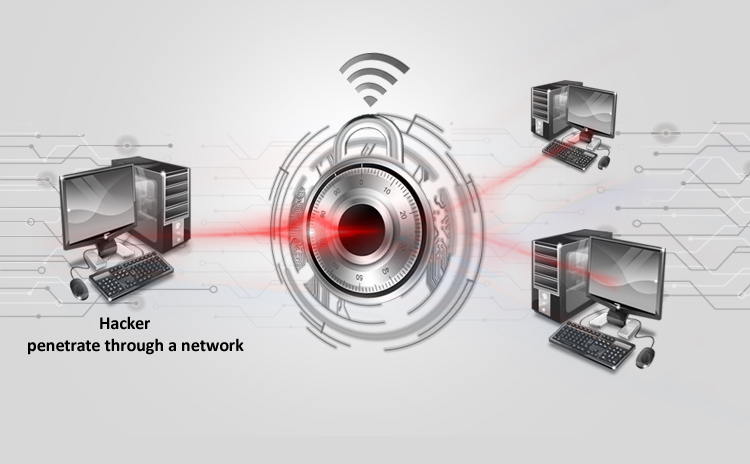
Title: Cyber Attacks Explained: Authentication Attacks Scope of article In the previous article, we dealt with man in the middle attack whereby a hacker can…