- Wireless Security Devices Compliance - 03/01/2020
- Securing Email Servers Compliance - 03/01/2020
- Ethical Hacking Information Gathering - 03/01/2020
RCIE Course Modules:
3.10 Securing Email Servers Compliance
What is email server security compliance?
Securing your corporate email server is one of the most important aspects of ensuring compliance. With the rise in cyber-threats and the focus on phishing and malware, there is stronger need for deeper compliance in the email domain.
With advanced tools like encryption and authentication, there are many methods of ensuring that the corporate email remains secure. Additionally, there are measured tactics that allow for strategic sending of files over email and others over intranet.
There are challenges when it comes to ensuring proper compliance to email server policies. However, with the help of proper education, training and technological advancements employees can feel more empowered to perform their tasks.
The importance of encryption in email
Encryption is one of the premier ways to ensure that the corporate email box remains secure. This is done through a predefined protocol and an encryption key that can be used to decrypt the message. Even if hackers gain access to the message, it may not be readily available to read.
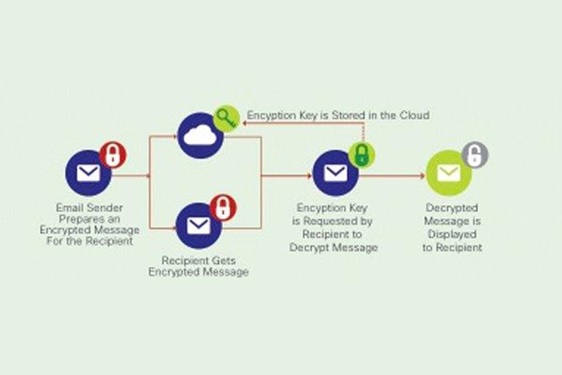
With the introduction of the cloud, the encryption key can be stored within the domain. This means that the hacker may have to gain access to the key from the cloud, as well as acquire the message being sent. This reduces the chance of brute force hacking.
However, as with any technology measure compliance is key. This means that employees need to be careful about how they access their email and what emails they share. Hackers can use social engineering, phishing and malware to gain non-technological access.
They can also hack into the mainframe by posing as the IT admin and writing a spoofing email. There are multiple ways to gain access via email, which is why it’s important to have proper compliance when dealing with the domain. Email is one of the most frequently used features within the business and sensitive information gets shared regularly.
Hackers can spot a weak email server from a mile away and attack at will. They can sense when the technological capabilities are just not there. They can use advanced packet sniffing tools to read the emails or be a passive observer from a Day 0 attack. There are various methods to hack into a company’s email and many of them require a complete technological overhaul.
Let’s look at how a common encryption method would work on email –
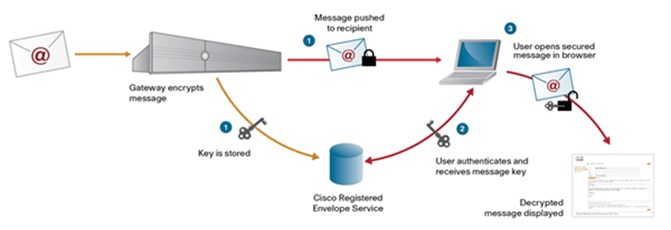
As we can see from the diagram above, the message is pushed to the recipient using a secure gateway. The transmission is only validated if the key is secure and the message key is safely transmitted. This is when the user opens the secure email on their browser and mobile to view the decrypted message.
If companies don’t have an encryption mechanism built into their systems, then there could be issues arising from the lack of security. This is because hackers can use generic methods to decrypt the message and not need the key in the first place.
For an encryption protocol to be successful, it must also be scalable. This means that all levels of the company should have similar encryption methods, which is applicable for email servers as well. All messages must also have a standard protocol when sharing as well.
While the appropriate compliance policy should be applicable to all transmissions, employees often violate the rules unknowingly. They send personal emails over their corporate servers or upload personal files. While companies can enforce BYOD policies and personal use, there is always the chance of a risk.
Remaining ahead technologically (malware, ransomware, etc)
It is estimated that in 2017, the cost of cybercrimes jumped 23% to about $11.7 Million on average. Cyber attacks rose during the same timeline, with 2019 being the year for greater cyber-compliance. More technology firms are launching better tools to enable greater compliance.
In fact, the cost of a malware attack can reach around $2.4 million, and it may take about 50 days (on average) to resolve the issue. This means that email hacking or phishing can be the leading cause of cyber attacks in the first place.
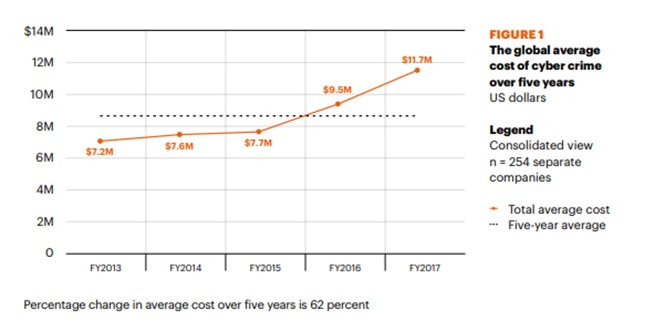
As the cost of cybercrimes rises, CCOs must invest in better technology. This means better encryption, greater compliance and better server security at the base central. The cost of compliance increases as well, but the overall ROI for investing in compliance is also greater.
Information sensitive industries like healthcare and fintech need cyber-compliance to be in its best shape possible. This is because there is greater strength in having more options when it comes to cyber attack redressal.
Whether that be email or DDoS attacks, CCOs should have all the tools ready in their arsenal. According to Cisco’s Annual Cybersecurity Report, 8 % of malicious email attachments were docm files which leads to direct access to documents.
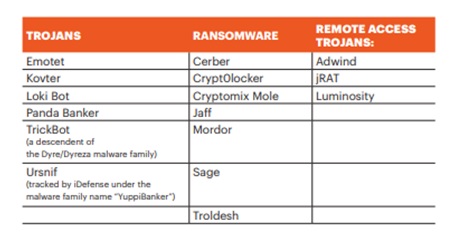
Some of the more common phishing and ransomware offenders have scaled up significantly. CCOs must be aware of common attackers such as Emotet and jRAT. These are technologically superior forms of malware and must be protected against using a high-quality anti-malware software.
When it comes to compliance, CCOs need all tools necessary. This is why 2019’s CCOs will have greater access to more tools that have wider scope. They will be able to provide enhanced security at all layers within the organization.
Employee education and protocols around email
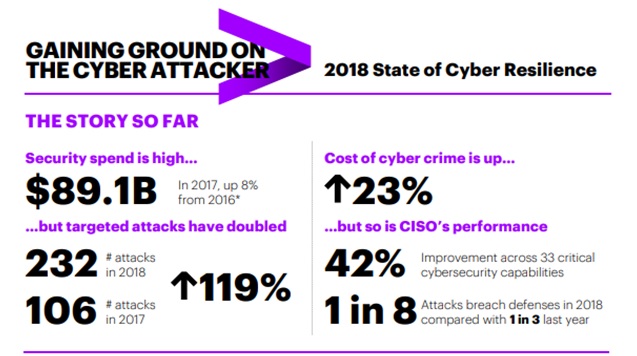
Per the 2018 State of Cyber Resilience report released by Accenture Global, targeted attacks have doubled since last year. However, the performance of a compliance officer and IT cybersecurity expert has risen as well. While the market shifts towards a more technological focus, there is greater innovation still necessary.
As employees become more mobile, the risk of email hacking rises. Employees are opening their inbox using corrupted Wi-Fi networks and insecure pathways. They’re also opening their private files from their personal devices and exploring their inbox using an insecure network.
This is precisely where compliance steps in and drafts the right guidelines for greater effectiveness.
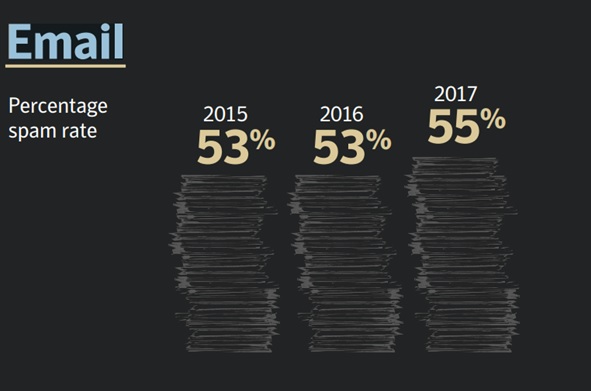
Data from Symantec Research suggests that spam has risen significantly, and hackers are using subject lines like “Invoice” and “Payment” to entice employees to open. Some of them appear to have been sent from the company domain with slight variations.
E.g. if the company is named abc.com, then the domain maybe abc1.com or abc.nl. This is done to trick new employees or unsuspecting incumbents to click the link to open the mail. They don’t even have to download a file to have the virus installed on their computer.
The type of email attacks has changed significantly as well. They’ve become more sophisticated and are using cryptocurrencies as ransom for data. These hackers are relying on bulk emails and blocking to ensure that there is no trace back to them.
They’re injecting malware into the email as a form of a URL. When the employee clicks on that URL, they will have automatically installed a malware patch on their device. This could be masked as well, with the employee not knowing that the URL had a problem.
Educating employees about email protocol
This speaks to a larger problem in the email compliance domain, which is education. Every employee knows not to open dangerous attachments as they could contain a virus. However, employees don’t know that a URL can be just as dangerous.
This is where education comes in, with proper training and policy formation.
CCOs need to keep employees updated with the latest trends in cyber compliance and attacks. This includes new form of email phishing, malware and ransomware. CCOs also need to ensure that they’re creating an innovation-focused environment within the compliance domain.
When CCOs are updated about the latest changes in the compliance domain, they can make better email security decisions and keep employees safe. Additionally, CCOs can also create more compliance related policies that are around new forms of email use.
E.g. with the introduction of the cloud, new email formats are being released. These emails open only on certain apps or require access to certain features. Additionally, certain websites may need your email account to allow user-name access. These uses of email identification can leave the company vulnerable to hackers.
Hackers can also use a simple landing pack spoof where the website could look like an enterprise social media platform and require that employees log-in using their IDs. Since the browser may autocomplete the information, the employee may click on OK and allow access. Hackers can then gain valuable information (already decrypted) right from their dashboards.

The true challenge arises when the hacker has already gained access. It can take anywhere from minutes to months as the compliance department is able to understand the hack. Some hacks can go unnoticed for a long period of time, as demonstrated by Verizon Security’s 2018 Report. Upwards of 2/3rds of attacks were undiscovered for months.
This isn’t a common picture as more attacks occur stealthily. Hackers are opting for quieter methods of gaining access. They’re relying on compromising the system through infiltrating the email servers. They’re also sharing malware at an astounding rate. More than 90% of all malware arrives via email now that we are in a truly mobile world.
Research also suggested that a majority of the cybercrime conducted on companies was done with the motivation of ransomware. Additionally, it’s widely known that email compromising is the most common form of ransomware vulnerabilities.
This increases the need to have stronger email servers and better compliance overall. If the employee doesn’t open that email or the server can correctly frame an email as spam, then they can be more secure.
Assessing a compromised email account
The true challenge arises when a compromised email account starts sending phishing emails. This is because other employees will open the link trusting the source of the email. Since the sender is a verified employee, others may open the email as well.
This increases the spread of the malware or ransomware, which finally gives access to hackers across the board.
The compromised account can also gain access to the company’s cloud. Depending on the authentication protocols instated in the company, a third-party vulnerability can also allow for hackers to gain access. Additionally, employees that are roaming within the corporate offices can transmit the malware by logging into their local LAN.
A wireless connection can become quickly compromised when an employee uses a non-secure email portal. While some employees may share important files from their personal accounts, many of them stick to the authorized email server. This is because the cost of anti-compliance is heavy, both in terms of monetary and reputation.
Employees must have a direct approach when it comes to compliance and remain within the boundaries outlined. When it comes to personal use, employees must have the right tools to determine which files can be shared and which can’t.
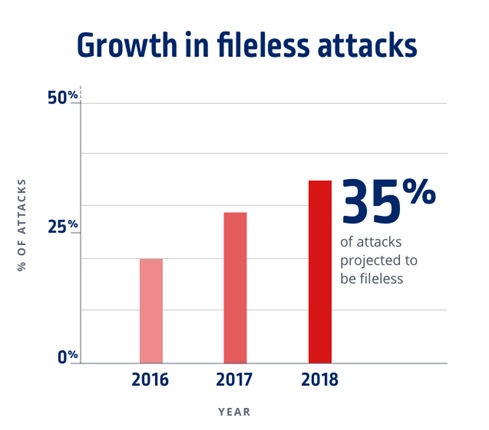
This means that apart from authorization, email use also needs an overhaul in terms of utility.
File-less attacks are on the rise, and CCOs need to have a clearer policy and education program when it comes to email. This is because file-less attacks are more likely to work when it comes to sending malware at scale. Employees may open the email as it doesn’t appear to have any attachments.
This is why CCOs need to have an official program when it comes to compromised emails. The compromised email accounts must be contained, and the source of the hack must be identified. It’s one of the best ways to ensure that there is no spreading of the virus outside of the quarantined area.
Additionally, there are technological tools that allow for reviewing the utility of the email as well. CCOs can access the dashboard to review logs and information about who was using the email ID. This can help in creating a stronger plan of action when it comes to certain employees or domains.
CCOs also have policy formulations that can allow for greater control over technological capabilities. This means that CCOs can create new policies that restrict the sharing or receiving certain types of files. For a certain domain, a certain type of file can be restricted. This allows for greater control over email and more insight when it comes to protection.
“The advent of secure email platforms such as Mimecast, Symantech, etc., can reduce the number of phishing and spam email in general. The cost and time to implement can be a constraint for small to mid-size companies, not to mention the administration costs moving forward.
The pure numbers of malicious emails make prevention very difficult considering one in one-hundred emails are in some form of a malicious hack attempt. Data Security has to be right 100 percent of the time to be successful in protecting your data, but a hacker has to be successful only one time to steal your data.” – Daryl Crockett, CEO of ValidDatum. (Cybersecurity Exp)
As with any format of cybersecurity and compliance, education is key to increasing adherence. However, when an email account has been compromised, the right protocols can help in controlling the situation. The employee must know the steps required to ensure that proper validation and IT verification is done.
This is important so that every employee is empowered enough to make their own decision in the space. They can take quicker action and inform the CCO department sooner rather than later.
Penetration testing on email servers
Corporate email use is evolving around the world, with more employees preferring to use their personal account. Research from investigation firm Stroz Friedberg Inc. found that a majority of employees still use their personal accounts to share company information.
Whether it be for convenience or for a lack of understanding, employees need to use secure corporate accounts. Employees also need to understand the dangers of using a personal account when they should have used a corporate account.
There are problems with the way that employees are using their corporate accounts and are sharing files outside of the secure network. This is why running a penetration test is key to reviewing the status of your educational programs.
Having these tests run every quarter or so will help in building a more secure email environment and allow for greater compliance across the board.

From personal computers to using IoT, each device has its own protocol. It’s important to have a testing environment setup to ensure that there are no lapses between devices. For email communication, it’s critical to have the right approach to penetration testing.
Technological Testing
From a technology perspective, there are various factors that contribute to a positive penetration testing scenario. There are various tools and guidelines that can be used to perform the testing protocols.
From a strategy stand-point, it’s important to plan ahead. This means that CCOs can create test accounts or allow for email penetration during off-hours. This also enables CCOs to test the strength of the email server when there is no load or network connecting directly into it.
It also provides a more single-factor way of approaching the strength of the encryption as well. Since there is only one testing transmission, the results can be granulated better.
Resource Testing
Resource testing involves sending test emails and scans to your employee base. This also includes sharing dummy emails within control groups that have just been through the orientation or educational seminar.
This helps in reviewing employee performance and understanding how effective your programs have been when conducting them. Additionally, resource testing will help strengthen weak-points within the workforce.
Since phishing scams are based off numbers and social engineering, CCOs need to issue these tests repeatedly. This will help provide better results and focus on the specific types of attacks that produce the results.
Testing for resources can be done statically and dynamically.
From a static resource testing perspective, employees can be singled out and tested on a regular basis to review the performance over a time period. These employees can be informed prior to launch that there are going to be randomized testing.
Since the results are static, CCOs can better understand the impact of their programs. Additionally, as there are lesser number of variables, the results are more standardized.
For dynamic testing, there are phishing mails sent out regularly to all employees in a dynamic manner. As the employees get tested and reviewed, CCOs will get dynamic results over a longer period of time. CCOs can perform the test if they understand the results better.
They can also test for various factors like open rate, risk factor, click through and information shared. Additionally, CCOs can design these tests dynamically and send multiple phishing mails to one or two departments as well.
This helps in strengthening the overall employee base and their compliance to protocols listed out.
“We are attacked every day, just like every other corporation—about 16 attacks a day, in fact. There are a couple of things we do to quickly contain and minimize the impact of attacks and protect data. I was pleased with the way we executed our response plan, but more important than the response was our level of preparation. We have tight integration between IT and security operations so we can move quickly. This was not a breach—it was a service interruption. As a pre-emptive measure, we shut down services or links to protect the confidentiality and integrity of the information.”
– Jim Nelms, CISO at LabCorp
Business Email Compromise (Email Security Review Audit)
It’s important that CCOs perform regular audits to review their email security. This can be done with external vendors or via in-house capabilities. Additionally, there are greater benefits to conducting all tests within a listed-out framework.
The audit can review Email and DNS configuration impacting the confidentiality and integrity of communication.
Here are some of the factors that must be checked during an Email Audit –
Sender Policy Framework (SPF) –
SPF is essentially an anti-spam approach in which the domain of the sender can be authenticated for the sender. This helps in weeding out spammers and infiltrators that may want to gain access via phishing mails. It also helps protect against spoofing activities.
Domain Key Identified Mail (DKIM)
Senders can create a DKIM by signing the email digitally. This ensures that the right person is sending the email ahead and it is not a scam or spam email. It also helps that the signature is located in the header of the message so that the MTA can generate it using an algorithm. The unique hash value will determine the signature of the sender.
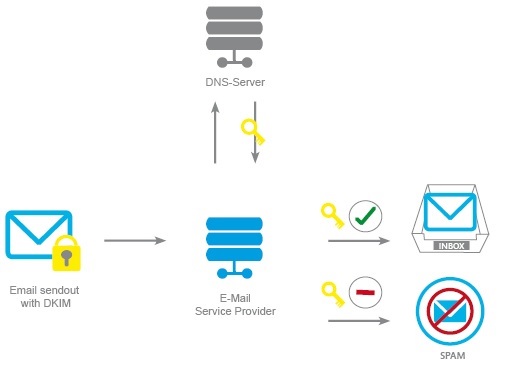
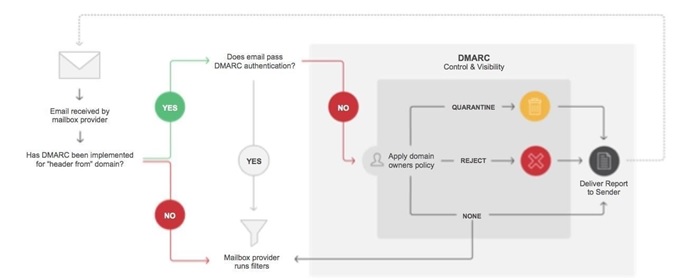
Domain-based Message Authentication, Reporting & Conformance (DMARC)
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication mechanism. DMARC ensures that the email is legitimately authenticated using previously defined standards. Otherwise the fraudulent email is sent back and blocked permanently. Using this protocol, DMARC is able to leverage domain alignment and reporting across the organization.
Additionally, DMARC checks for SPF authentication and alignment or DKIM across the transmission. This helps in rejecting mails that don’t comply with standards laid out. A reference of DMARC is shared below.
SMTP SSL or TLS support (SMTP/S)
Encryption testing is another important aspect of email auditing. It’s important for the CCO to test out the protocols being used, and the encryption standards being deployed.
Additionally, it’s key to find weaknesses hidden within the encryption model being used. That’s why CCOs need to constantly test out these protocols to find the best option available to leverage. There are greater advantages to using the best in standard encryption, especially when it comes to sensitive data.
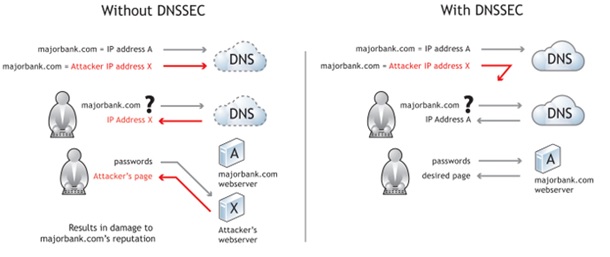
DNS SEC
DNS SEC can be used to protect against attackers that can hack into email servers. This is done by digitally signing the data so that the validity can be maintained across the board.
It needs to be deployed at each step of the authentication process to enable full scale and better control. CCOs need to review their DNS SEC protocol to ensure that there is proper authentication of the emails being shared. The data may be encrypted using another protocol, but the validity of the address should be present as well.
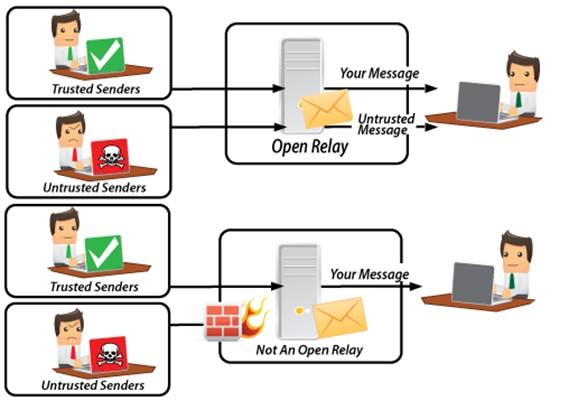
SMTP Open Relay
The Open Relay controls how the email is being sent to the employee at the other end. It creates a protocol to allow for third-party relay of messages. The open relay creates a pathway for third-parties to share emails back and forth.
It’s important to have a strong policy when it comes to the Open Relay so that compliance measures can be upheld. CCOs need to test out their Open Relay so that they can be secure against unforeseen attacks.
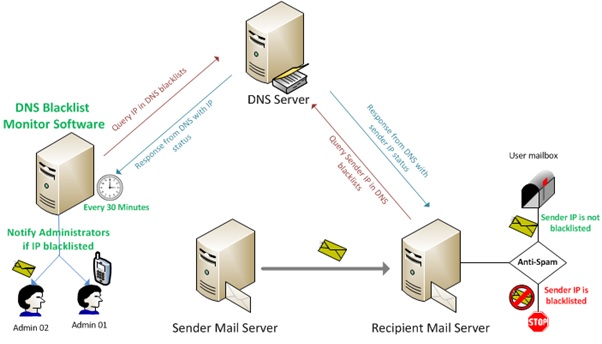
Anti-Spam blacklists
Blacklisting is a common compliance measure done to prevent known offenders from entering the system. This is also accomplished by having a robust technological architecture and strong compliance policies protecting the company.
CCOs can explore a variety of anti-spam black-listing measures and ensure that their servers are protected. Popular blacklisting solutions have pre-loaded common domains, but CCOs need to review all the domains manually and run tests on them as well.
Having a strong blacklisting policy protects the company from common threats that may emerge from time to time.
Domain Name Protection
It’s important to have the right domain name protection measures in place. CCOs can run testing mechanisms to review their domain names and create fake spoofing accounts to test the validity.
Additionally, DNP measures can be taken place as a deterrent to hackers as well. They include locking the domain, creating firewalls around the domain and having multiple variants pre-registered. This dissuades hackers from using DNP based attacks.
Securing Email Servers Compliance
From a compliance stand-point, CCOs need to formulate the right policies that are scaled up. From sharing particular files to obtaining the correct permissions, there are multiple ways through which servers can remain protected.
Authentication is also critical to ensure, as there are multiple authentication measures that can be put in place. From biometric to two-step there are multiple ways through which email servers can be secured.
Compliance should also be enforced through education as well. By educating employees the right way, CCOs can create an environment of compliance. They can also create better pathways for CCOs to use when they need to explore secure options.
Logging and Dashboard management are critical tools as well.
Every CCO has access to the log and dashboard of the emails in the company. They can review the information being shared across the emails and formulate their own strategy to accomplish compliance.
By frequently reviewing the logs and the dashboard, CCOs can ensure that compliance is seen throughout the organization. They can strengthen certain areas, correct certain action and review the impact of new technologies that enter the system.
Companies can become that much more compliant when CCOs can review meta-data stored on the emails being shared. A certain file type can be flagged, or a transmission protocol can be reviewed manually.
The value of a hacked email account is far greater than companies might presume, which is why CCOs must ensure that there are no lapses in protection. Cybersecurity measures can be standardized to a certain extent, before compliance takes place.
CCOs install the needful in place and then policies need to be well executed. Research from IBM X-Force and IRIS suggests that email accounts can be used for post-intrusion manipulation as well.
This means that a hacker may have obtained entry from another channel but used a compromised email account to change the logs.
This complex form of hacking can make it that much more difficult to capture, and CCOs may lose track of the flow of information. A hacker can also do a dummy attack to let an obvious phishing scam get caught. They can use the distraction to plan their actual next move.
Deleting logs, keeping copies or ensuring that tracks are covered, are all methods that hackers can use when gaining access to an account. Email accounts are some of the most important assets within an organization, depending on the authorization provided.
Employees must understand the importance of protection and maintain a strong environment of compliance all around.
Employee management and assessment
Research suggests that over 60% of email attacks happen at lower management and base employee levels. This means that most of the attacks happen at the entry level of the organization. Protecting this end of the employee base is critical.
Upper management and CXO level employees received a significantly lower number of phishing emails (around 25% and 5% respectively).
This means that the phishing attacks are happening at the ground level where execution is key. CCOs need to constantly monitor the lower-base of the hierarchy for compliance issues.
Third-party vendors can also pose security threats when they share emails from compromised accounts. That’s why having a coherent anti-virus and anti-malware software installed is critical. This is the best way to protect the email server and disallow scale-driven attacks to take place.
Since sourcing the inception of the attack is critical, CCOs can also enable all employees to become vigilant. They can flag suspicious accounts and domains for you so that they can become the first line of reporting and innovation.
CCOs need to work with employees and engage them in the compliance process. Otherwise, compliance may become a single-lined process where threats are only monitored at the top. Compliance officers need to be knowledgeable about the information being shared via email and let them know about offences.
The number of attacks has increased by 85% in the previous year, with increased focus on small to mid-size enterprises. Since scale-driven email hacking attempts don’t require resource-driven initiatives, much of the basic attacks can be counteracted.
CCOs need to have the right technology measures in place to ensure that no attack can weaken the defences of the email server. Employees are in the line of attack if they remain non-compliant for longer periods of time.
Additionally, CCOs need to have an employee-first mindset when it comes to compliance. This is so that they can have a more integrated approach to compliance and make sure that compliance becomes an area of strength.
The compliance domain is rapidly evolving and needs the complete participation of employees across all domains. CCOs need to work in tandem with the employees present in the organization.
Having an incident response strategy
When it comes to email hacking and compromises, CCOs need to have an incident management plan. The compliance domain needs to ensure that all hacks are contained within a certain parameter and that employees are safe from the attacks.
Additionally, when it comes to sensitive data an incident management plan provides deeper insight into the breach. Whether that’s monetary or business data theft, there are multiple ways to approach the analysis report.
“We deal with it very strictly with a absolute zero-tolerance policy. So whenever we are attacked in one way or another, we will actually go after the people to the full extent that’s possible under the law. And you have to do that, right? Because if you ignore attackers, you let them hit you without going back after them, then that kind of creates ecosystem where you will draw more attackers.
So we have to be very firm in dealing with these sorts of attacks. It’s part of the business. We expect it to happen. The experience and expertise that we have gained from dealing with these type of attacks for the past three years has made us significantly stronger and much better positioned to take on these sort of threats than a typical company our size would be able to do.” – Andy Yen, Proton Mail CEO
Threat Detection
CCOs need to have a strong detection mechanism present. The detection mechanism should be tested repeatedly to ensure that there are no weak points within the system. This can be done through penetration testing and brute forcing your way into the server.
Threat detection also occurs when CCOs have a strong firewall protecting their email servers. This can flag attacks from happening and present insights driven by AI and machine learning. These insights can shed light on which attacker was using what route to gain access.
This is exceptionally helpful as more CCOs need to have an active approach to fighting hackers. Detection of threats can also open up new opportunities to companies who want to expand in the most compliant manner possible.
Incident Response
The response to the attack should be outlined as well. This could include various strategies and techniques to ensure that there are no future breaches and that the situation is contained. Either the issue is escalated or handled locally depending on the extent of the breach.
Incident response also includes informing the authorities and gaining more perspective on the matter. As sensitive data may have leaked to these hackers, it’s important for the right stakeholders to know as well. Hackers may gain access but having the right response methodology works best.
Risk Mitigation
Mitigation is the most critical step in the process. It encompasses various degrees of action plans and strategies that CCOs must engage in. It also covers the gamut of tools that CCOs have to prevent future attacks from taking place.
Mitigation also includes scaling up future capabilities from a technology perspective. This may include threats that emerge organically within the industry as well. Where encryption may fail, CCOs can design their own format of protection.
If there are challenges with authentication, then CCOs can design their own authentication protocols. There are multiple steps that can be taken to ensure that there are no future attacks on the email server. Since the email can provide access to hackers to sensitive information, it’s important to have a well-protected email server.
“Currently there are weaknesses in both server-side and client-side encryption. If you’re worried about the trustworthiness of the server, be advised that anyone who controls the server also controls the server-supplied JavaScript that executes in the browser.
If someone who operates a web-based email service is hit with a court order, they could be coerced into injecting a “special” version of the JavaScript that could exfiltrate the encryption keys from a user’s browser. These could then be used to decrypt intercepted traffic.” – Phil Zimmermann, creator of PGP encryption
Reporting incident
Companies also need to report the incident internally so that all stakeholders are in sync with the latest developments. If it’s a local attack, then the local regional offices can be made aware.
If the attack is more national or based off a certain server, then the company can be made aware.
The reporting of the incident also needs to be done to the upper management layers who can take an informed call as to the next steps outlined by the CCO.
The CCO, in turn, needs to ensure that the reporting mechanism covers the next steps in the strategy and recover the lost data.
Recovery of information
This is one of the greatest challenges in the compliance domain, as ransomware can get complicated. Since hackers are difficult to contact or connect with, there needs to be a steady approach to recovery of data. The server needs to be sealed off with a backup of the data ready to launch.
Additionally, when it comes to lost information, there needs to be a strategic approach to gain information back. CCOs need to design a comprehensive plan of action that enables them to retrieve the lost information.
Even if the information is obtained in smaller bits, it’s valuable to the organization. That’s why CCOs need to have a direct line of planning and execution with the IT domain to recover lost data. For data that is lost to the ether, there are few methods of recovery outside of the matrix.
Hackers can hide their traces and ensure that no IT domain can capture them. That’s one of the greatest reasons why compliance is an important domain and employees need to be in sync with corporate protocols.
3.10.1 SMTP STARTTLS
What is SMTP STARTTLS?
Email encryption is a complex subject which requires a deep dive into individual terminology.
SMTP is an application layer protocol that is designed for better email encryption. The client that wants to send an email opens up a TCP connection to the SMTP server. The transmission then takes place, leading to a successful email exchange.
The SMTP receives the connection request and initiates the connection on the port. When the connection is established the email can be shared ahead.
STARTTLS is a protocol to make an insecure connection more secure using SSL/TLS. Essentially it is a protocol command that tells the email server than a client wants to turn an insecure connection into a secure one.
By using TLS in the STARTTLS, it can enable safer email transmissions using higher quality protocols. Employees can share emails in a safer manner and not leave their emails susceptible to hacking.
A reference of SMTP is displayed above, and CCOs need to review each step of their own email protocol to ensure compliance. Security is critical to uphold and CCOs need to have the right tools in place to ensure proper measures.
Why is encryption important to email security?
Encryption allows for scaled compliance and protection against hackers. As compliance officers can only do so much, encryption adds that secondary layer of protection within the system. It ensures that there are no lapses in security and that every employee is safe from an attack.
Email security also includes the type of protocol being used, which is why SMARTTLS was introduced as a new standard. It did away with much of the problems with legacy systems and introduced a new format of encryption.
Additionally, it allowed the standard SMTP servers to communicate over existing ports by displaying whether the server supported TLS encryption. The added encryption allowed for general connections to become that much more secure.
Without additional load, the existing servers have become more secure using encryption over SMTP.
The importance of SMTP STARTTLS
The STARTTLS command is defined in the following documents –
For IMAP and POP3 is defined in RFC 2595,
For SMTP in RFC 3207,
For XMPP in RFC 6120
For NNTP in RFC 4642.
For IRC, IRCv3 Working Group has defined the extension with FTP using the command “AUTH TLS” defined in RFC 4217 to make connections encrypted.
Essentially, there are two models for email transmission across two points.
End-to-End transmission.
End-to-End solutions encrypt the email but ensure that only the intended recipient can decrypt the message. This means that solutions like PGP and S/MIME can allow only the recipient to read the decrypted message.
Hop-to-Hop transmission.
STARTTLS provides a Hop-to-Hop encryption model which doesn’t require configuration on the end-user’s part. An email server with STARTTLS can protect emails from passive network sniffers and packet eavesdroppers.
Hop-to-Hop also ensures that there is no metadata leakage, including subject line information or other meta data. This means that packet sniffers won’t be able to understand the data being shared as well.
So long as STARTTLS is being implemented by both the email server and the sender’s service, the email will be completely encryption. That’s why organizations are urging third-party vendors to use email encryption to provide overall compliance.
What’s most important is to ensure that there are no downgrade attacks happening on the STARTTLS protocol. There is a preloaded list of MTA-STS security policies that can help prevent any such attacks from occurring. Since the mail server is critical to protect, any attempts should be caught in time.
Enhancing the STARTTLS is key to cyber compliance. As the protocol uses SSL and TSL standards, each transmission can become automatically more secure.
CCOs can make STARTTLS more scalable and secure using critical strategies in the domain. They can start by ensuring that the STARTTLS adoption is clear and coherent.
By having valid certificates on mail servers, STARTTLS can become a more ready-to-use platform. Additionally, running a more secure server should be higher on the list of security priorities.
STARTTLS is a secure transmission protocol but there are many holes when it comes to secure connections. Since both mail servers ask each other about their status, the initial connection itself is insecure.
It doesn’t matter than the final transmission is done in a secure manner, the connection request is still insecure. This could lead to spoofing and server hack attacks by nefarious entities.
It’s important to have the right firewalls and protocols in place to ensure that there are no potential hacks that can occur using this route. Since the overall connection was insecure, hackers would penetrate the network by spying on that initial connection request. There could be a large number of attacks that can take place, including some that can occur on scale.
CCOs need to be updated about the latest trends in the domain of email encryption. This is important to stay ahead of hackers that may want to access your email servers.
Additionally, the man-in-the middle attack could be used to make the network insecure. This is why a new protocol was launched keep the insecurities in mind. This was called SMTP STS (Strict Transport Security).
STS is an advanced form of email security standard, which is designed to enhance communication strength. It’s a more secure protocol in general and is used widely in corporate email communications.
STS also takes care of another flaw in the communication, which is the fact that encryption policies can’t be communicated. This meant that two different servers could interact without distinct encryption frameworks.
SMTP Strict Transport Security (SMTP STS) works alongside SMTP standard to block hackers that use encryption downgrade and MIM attacks. The model also protects against active hackers that want to intercept connections.
Since there is a certification authority enforcing the encryption, there is a more valid connection being made. This means that the transfer of messages is made that much more secure using the methodology. It will also ensure that the recipient supports SMTP STS and has an updated encryption certificate.
3.10.2 S/MIME
What is S/MIME?
Secure MIME is a widely recognized standard for digitally signing a MIME based email and the public key encryption. It was developed to become a scalable solution to secure email communication worldwide.
S/MIME has been designed to protect against packed sniffing, MIM attacks and hackers that may try to leverage an access point. Certificate owners are also able to identify themselves to the recipients and verify their address using the signature.
This enables more secure communication to occur, using encryption keys that are well protected. S/MIME can only encrypt emails if the recipient is also in possession of a certificate. If the certificate needs to be reinstalled, then the encryption must be shared with the contact each time.
CCOs must also update the certificate regularly to ensure proper compliance within the framework.
A reference of the S/MIME protocol is shared above. CCOs need to ensure that their email servers are well protected using the S/MIME protocol. Otherwise, their servers can be left open to vulnerabilities.
S/MIME performs the following critical functions.
Authentication
The protocol allows for greater authentication overall, providing more information during the initial connection. This enables greater validation and a more secure way of communicating. Both parties can fully verify who the other person is before transmitting the right information.
Message integrity
The message quality is not lost during the transmission, as the integrity is maintained through the communication. Once the connection has been established using Class1 or Class 2 S/MIME, there is message integrity maintained. Companies can also make sure that their messages are fully protected by running the appropriate tests.
Non-repudiation of origin (using digital signatures)
The message signature is of critical importance as that is the main method through which the verification is done. Since the digital signature is maintained throughout the transfer, the data isn’t rejected.
The transfer is done using minimal amount of information and the source doesn’t have to reveal too much. The connection is also secure.
Privacy
Since privacy is maintained through the transmission, there is greater emphasis being put on this protocol. There are many protocols for information transfer, but privacy is protected by S/MIME.
CCOs need to understand the value of privacy between email servers and preserve the strength of the transfer. Privacy is important to maintain, especially in more sensitive industries like healthcare and finance.
Customer data also needs to be protected anytime a single unit is sharing sensitive information across a transfer protocol.
Data security (using encryption)
Encryption is of the essence, as there are an increasing number of attacks taking place. Encryption is ensured using three critical protocols under the S/MIME transfer. They are –
Transport Layer Security (TLS)
TLS encrypts the entire tunnel or route between the email servers. This helps in protecting against eavesdropping or snooping. This encrypts the transfer of email information and disallows hackers to gain access. It’s an important component of the encryption model.
Secure Sockets Layer (SSL)
SSL is a widely known encryption model that makes the connection between the client and the server encrypted. It protects the information being shared and bars hackers from entering the packet.
BitLocker
BitLocker encrypts the actual data on the hard-drive in a datacentre. This is a physical and technological method of protecting the end server.
3.10.3 PGP
What is PGP?
PGP stands for Pretty Good Privacy and has been a standard for decades now. It has been a widely used encryption model that uses both private and public key encryption.
Therefore, it offers a high degree of security and protects confidential messages. PGP is constantly being worked upon to make conversations more secure. Vulnerabilities can be fixed instantly with developer communities working on the core technology.
Essentially, PGP allows users to create a public and private key pair. This allows you to turn plain communication into ciphertext. The public key is then used to encrypt the message and once the public key is retrieved, it can be decrypted with the private key.
This makes the communication that much secure as there is encryption at both ends. The public key can encrypt the message being transferred and the private key can turn ciphertext into normal text.
It’s important to understand that the private key may be secure, but the actual email isn’t. Attackers can spoof the email and made it look like the source was different. Authentication isn’t verified using PGP as it’s a main method for encryption and decryption.
The public key should also be secure and not be a commonly used one online. CCOs need to use the proper strategies to ensure that effective encryption can take place over time. As Bob receives an encrypted email from Alice, the email should have originated with proper signatures and encryption. Only then can the entire email sending process be fully compliant and secure.
PGP is a complex process made easier when CCOs have the right tools in their arsenal. As compliance is a key issue at hand, PGP should be used at the right email transfers. Added to PGP, there should be regular updating of the protocol within the organization.
PGP should also be used in conjunction with other protocols that protect the email server and the transmission. Authentication should also be enhanced especially in the case of sensitive information transfer.
“We’ve been trying to do things that are lightweight, and don’t involve such a heavy commitment from the IT department. It’s not an infrastructure thing, it’s an agile personal initiative. If you look at all the things that have been developed – firewalls, intrusion detection systems, all these things put in place to protect computers? They haven’t really hit a home run: they keep getting breached.” – Phil Zimmerman Father of PGP
PGP allows for users to sign their messages with digital signatures, adding that layer of authentication. This proves that the message was sent by them and the encryption is standardized. Accessing the private key, in this case, would be increasingly difficult.
However, EFAIL was able to access vulnerabilities within PGP as well. Researchers were about to find a security hole in email systems with which content can be decrypted if it has content like HTML or JS. If the email also loads external content, then the message can be decrypted as well in some cases.
As a result of the vulnerability exposed the content of the email can be transmitted across servers. The encryption keys are not disclosed but the hackers can still gain access to the information.
As a means of mitigation, CCOs must ensure that all emails don’t autoload external content. Additionally, emails should disable active content like HTML and JS. This makes it easier to keep the encryption alive as PGP works on improving the standards issued.
As a compliance office, it’s important to stay ahead of the industry and ensure that all emails are being encrypted the right way. Involving employees in the matrix is critical as well.
References, papers & e-books
https://www.cisco.com/c/en/us/products/security/email-encryption/index.html
http://www.ironportstore.com/Email-Encryption.asp
https://www.accenture.com/t20171006T095146Z__w__/us-en/_acnmedia/PDF-62/Accenture-2017CostCybercrime-US-FINAL.pdf#zoom=50
https://www.accenture.com/t20171019T100048Z__w__/us-en/_acnmedia/PDF-63/Accenture-Cyber-Threatscape-Report.pdf#zoom=50
https://www.accenture.com/t20180719T034642Z__w__/us-en/_acnmedia/PDF-82/Accenture-Security-2018-State-of-Cyber-Resilience-Infographic.pdf#zoom=50
http://images.mktgassets.symantec.com/Web/Symantec/%7B3a70beb8-c55d-4516-98ed-1d0818a42661%7D_ISTR23_Main-FINAL-APR10.pdf?aid=elq_
https://enterprise.verizon.com/resources/reports/DBIR_2018_Report_execsummary.pdf
https://enterprise.verizon.com/resources/reports/2017_dbir.pdf
https://blog.barkly.com/small-business-cybersecurity-statistics-2018
http://www.digitaljournal.com/tech-and-science/technology/q-a-why-are-we-still-at-risk-from-email-hacking/article/538770
https://www.incapsula.com/web-application-security/phishing-attack-scam.html
https://practical365.com/exchange-server/a-sender-policy-framework-spf-primer-for-exchange-administrators/
http://www.kenscio.com/blog/2012/02/29/what-is-a-domainkeys-identified-mail-dkim-signature-why-it-is-required-for-your-mailing-server-infrastructure/
https://blog.returnpath.com/how-to-explain-dmarc-in-plain-english/
https://www.icann.org/resources/pages/dnssec-2012-02-25-en
https://www.unlocktheinbox.com/resources/openrelay/
https://support.exabytes.com.my/en/support/solutions/articles/14000067547-all-about-blacklisting
https://www.cio.com/article/3305063/leadership-management/cio-interview-with-jim-nelms-ciso-at-labcorp.html
https://krebsonsecurity.com/2013/06/the-value-of-a-hacked-email-account/
http://www.strozfriedberg.com/wp-content/uploads/2014/01/Stroz-Friedberg_On-the-Pulse_Information-Security-in-American-Business.pdf
https://www.inverse.com/article/49041-protonmail-ceo-andy-yen-interview
https://www.bestvpn.com/privacy-news/interview-legend-phil-zimmermann-creator-pgp/
https://www.geeksforgeeks.org/simple-mail-transfer-protocol-smtp/
https://thehackernews.com/2016/03/smtp-sts-email-security.html
https://www.thesecuritybuddy.com/email-security/what-is-smtp-strict-transport-security/
https://www.internetx.com/en/news-detailview/smime-your-e-mail-security/
https://theprivacyguide.org/tutorials/pgp.html
Encrypted Email – The History and Technology of Message Privacy by Authors: Orman, Hilarie
PGP: Pretty Good Privacy By Simson Garfinkel
The Practical Guide to HIPAA Privacy and Security Compliance By Rebecca Herold, Kevin Beaver
PCI Compliance: Understand and Implement Effective PCI Data Security By Branden R. Williams, Anton Chuvakin

