RCIE Course Modules:
3.8 Firewall Policies Compliance
Firewall Policies compliance
Having a strong firewall policy allows companies to stay compliant to best practices. From a CCO standpoint, there are many tools and policies that can be implemented company-wide. CCOs can also create firewall policies when dealing with other networks as well, to create a stronger security foundation. Firewalls allow certain information and data packets to flow through a network and can allow for increased monitoring as well.
That’s why CCOs need to understand the importance of having a strong firewall installed early on. Otherwise, there may be 0-day hackers, malware spammers or agents who may have penetrated the network before you start implementing firewalls. Additionally, there is a stronger need for updating all firewalls within the organization. The need arises from legacy systems that aren’t able to stand against hacking testing.
CCOs can review the firewall policies of the organization and press for better alignment between distributed channels. A firewall can become one of the greatest sources of strength for the organization.
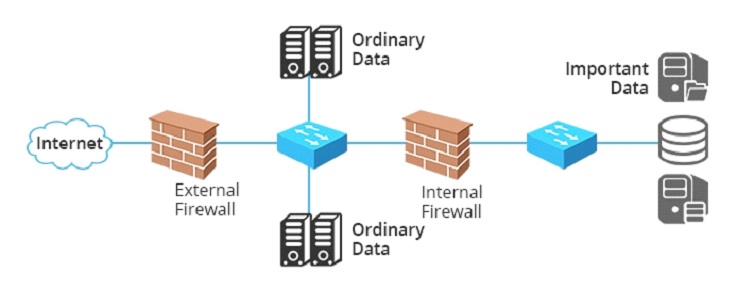
As we can see above, the firewall acts as a gateway for traffic to flow from one node to another. Whether that be ordinary data or important data, there can be firewalls strategically setup to avoid detection and penetration.
This helps in creating a security layer that is primary in nature, and that can also keep a check on malicious attempts. This makes the entire network that much more secure and ready for scaled expansion.
CCOs must ask themselves whether having a firewall will affect the business goals of the corporation. If the answer is in the positive, then that’s a solid move that CCOs should incorporate in the beginning itself.
However, if the firewall is slowing the data transfer or creating barriers, then CCOs may want to look at existing firewall policies.
Firewalls generally have a multifaceted role to play and CCOs must understand where they need to be installed. Many industry bodies have mandates on specific firewall usage and where firewalls must be installed.
For CCOs to remain compliant, this is a necessary step to ensure that customer data is kept safe and is not compromised in any way. Hackers are always trying to enter your database or “listen” for leaky networks so as to gain an access parameter. It’s up to the savvy CCO to ensure that there are no breaks within the network to gain from.
Having a robust firewall architecture is critical to having 100% network security. Whether you’re working in a small to mid-size enterprise or have a larger network size in a major corporation, network firewalls are critical to install.
Attacks on enterprise firewalls
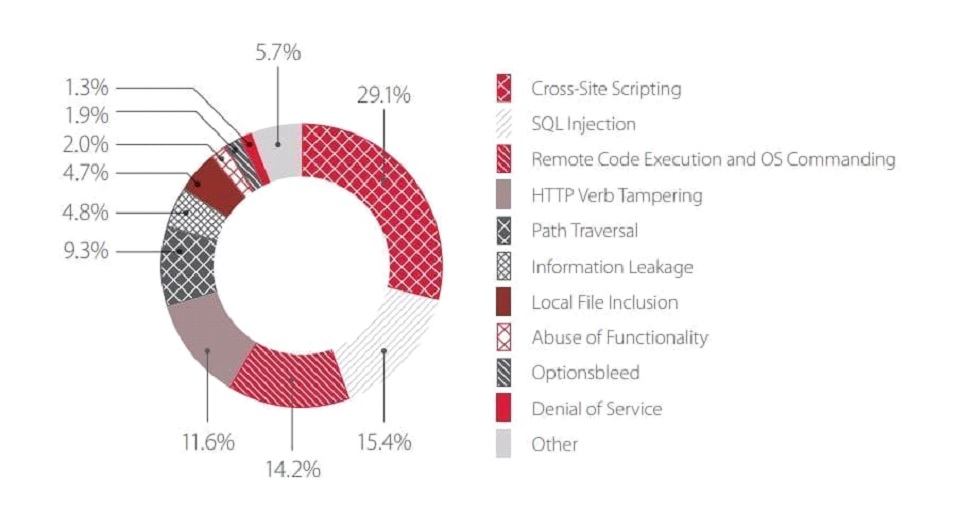
Data from PT security shows that a maximum number of cyber attacks on enterprises took place via cross-site scripting and SQL injection. These attacks are commonly connected with poor firewall policies, as hackers find a way inside these systems easily.
Hackers can also install malicious software inside any single computer that can provide access to the entire network as a whole. That’s why having a computer-level firewall is important as well.
This firewall prevents the device from getting connected if it has been compromised or not been updated with the latest patch. There are various factors that go into making a network more secure and having a robust firewall architecture is key.
Additionally, attacks such as DNS spoofing and DDoS can be protected against, when companies have a stronger firewall policy. These companies can keep their systems more secure by having a stronger firewall established prior to launching. Companies also protect themselves against unknown assailants owing to their strength in firewall.
One of the greatest areas of importance when it comes to firewalls is that all traffic must come through a firewall directly. The firewall ensures that no unauthorized access or traffic is allowed through the gates. Otherwise, a hacker could be using a compromised device to log into the network.
Multiple functions performed by firewalls
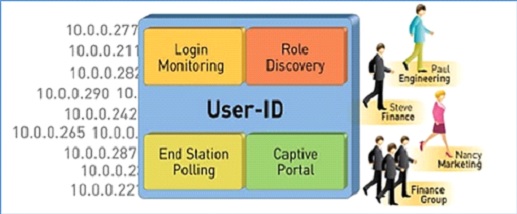
That’s why firewalls perform multiple functions within the organization. CCOs need to have monitoring and reading rights over the traffic that flows through the company.
That’s where a firewall emerges as a clear winner for all parties involved. From Login-monitoring functions, CCOs can understand what attempt has been made from where. They can analyse the flow of traffic better and review how many users have accessed the network.
When it comes to role discovery, the firewall can help in providing granular data on which user or AoE is trying to gain access. This helps in re-checking and reviewing against a secure database – access records, log-in credentials, etc.
Captive portals allow the CCO to disable or renew internet access or speed to a certain individual or group. This allows CCOs to take quick action in case there is a breach in the network.
There are multiple types of firewalls that CCOs can work with, and they each have their own unique purpose in the organization. They can set IP level rules or even specific instructions for web apps within the organization. This enables CCOs to have greater scale and increased control over the flow of information.
Additionally, CCOs have the capability to create stronger rules when it comes to determining the right action taken. Network security is critical when it comes to understanding different vendors, third-party suppliers and customers. There is a wide array of information being asked for, which needs barriers to entry depending on the type of access.
Shifting perspective on firewall technology
CCOs need to change the mindset behind firewalls in the organization. They can’t be seen as traditional guards defending potential attacks. They need to become increasingly sophisticated in their approach and scope. Firewalls can start to look out for active threats and be a source of great network strength.
Companies are also investing in 5G firewall security for devices that are leveraging higher spectrum bandwidths. There are also cases where IoT devices need bandwidth level protection and better firewalls to prevent data theft. Companies need to think about firewalls from the perspective of their network as a whole and not any one single end-point.
“Our service cloud providers are facing a major mobile infrastructure transition from 4G to 5G. We’re announcing a new super scale next-generation firewall that has been developed specifically for service providers with their high-throughput needs, taking into account the price considerations upcoming 5G and IoT transition.” – Nikesh Arora CEO Palo Alto Networks
Firewalls are being implemented in the case of driverless vehicles, autonomous AI and other applications. Since every technology requires a certain level of bandwidth and scale, there is a wider scope for firewalls to be implemented in a robust manner.
Companies can’t think about firewalls as a piece of “software” anymore. Firewalls need to become a part of the core IT vision. Stronger firewalls mean that all data within the company is made completely secure.
Firewalls now will be seen as handling multiple layers of requests and understanding the deeper context behind a data packet transfer. Since hackers can easily spoof accounts, change their identity and so on, firewall experts are making AI enabled firewalls that can make smarter decisions.
Firewalls also need to be seen as a layer of trust providers within a network. Otherwise, employees may not be comfortable with using a certain technology or an app. It may also complicate the process of on-boarding vendors or working with non-compliant clients.
Firewalls should be seen as the primary providers of security and allow companies to grow within that framework. The framework could be robust, like in the case of a fully customized network architecture. Alternatively, a simple firewall could also work in the case of smaller organisations.
Cloud technologies and integrating firewalls
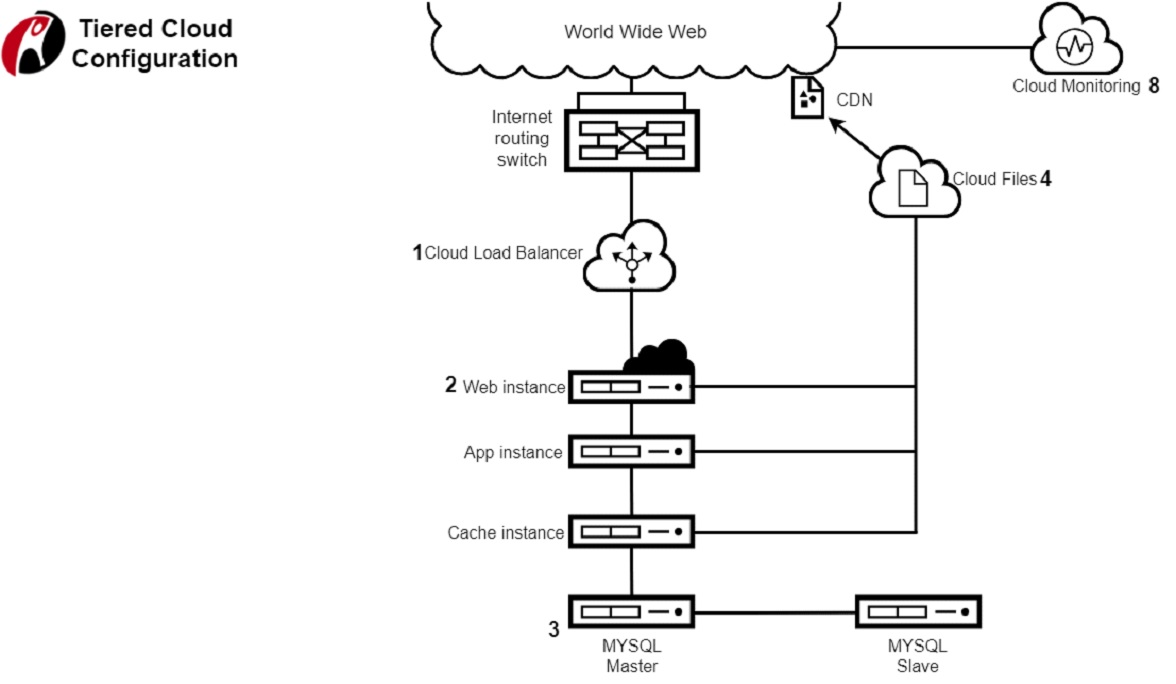
When it comes to the cloud and how firewalls impact that technology, then a special architecture must be setup by the CCO. From a compliance stand-point certain precautions must be set in place, along with guidelines on using firewalls as well. The typical tiered cloud architecture is displayed above, with multiple layers and stacks being used.
The interconnectivity of the cloud architecture used is critical to analyse. CCOs must map out the infrastructure that the organization is leveraging in order to create a more robust cloud security framework. CCOs can install firewalls at any stage of the interconnected network so as to provide greater security intra and inter networks.
E.g. CCOs may want to install a unique firewall between an app instance and the cloud files being leveraged. This is to protect certain types of data or to initiate better security for certain file transfers. If there is a connection between two web apps, then a firewall can be installed to monitor the connection as well.
Innovation in firewall technology & Blockchain
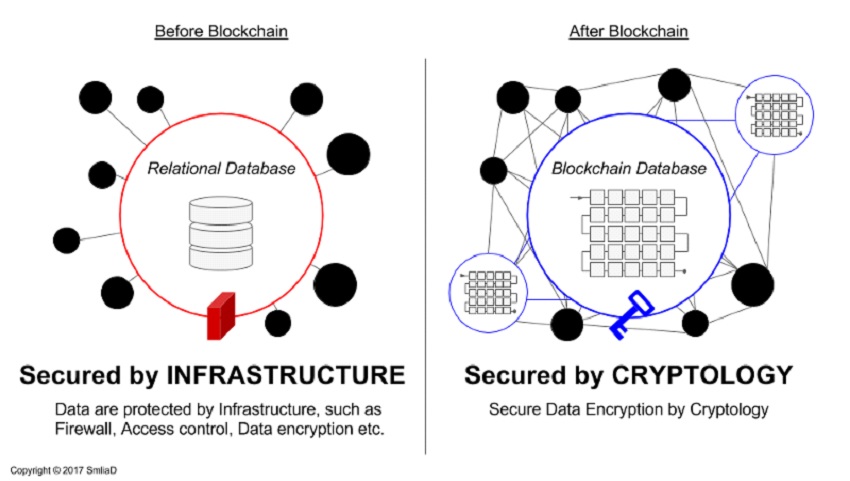
Networks can be made more secure when Blockchain is integrated as a firewall. The technology allows for greater security within the network and the database is made more secure as well. It is encrypted at all stages and the distributed nature of the information makes it more difficult to hack into.
CCOs must be made aware of the innovation in firewall technologies, from advanced hardware to architectural shifts. Since there is a greater shift towards IoT and AI enabled devices, firewalls must be put in place to prevent hackers from obtaining key information.
“That tiny locked-down piece is massively secured in the demilitarized zone and then it alone has a tiny umbilical cord that allows the data to flow back in and out of the firm. That separation of the nodes into those two pieces is the Blockchain Corda Firewall and we think it will be transformational.” – Richard Gendal Brown R3 CTO
Additionally, there is an increased need to create barriers to entry at the device level as well. This occurs when a device is trying to access information in a web application format or through the database directly. In this case as well, firewalls must be setup with rules that pertain directly to that scenario. This is a better way to ensure that all processes are made that much more compliant.
Firewall and IoT technology
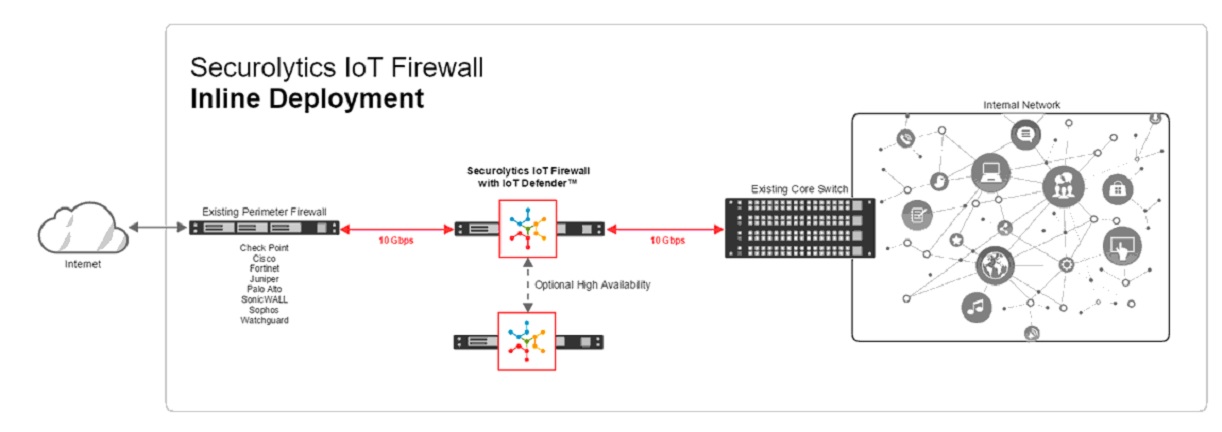
The internet of things has made it possible to have multiple points of access through these devices. Whether they may be distributed components under a single processing framework or wearables that are connected, firewalls must be installed to prevent hacking. Since IoT devices are constantly sending and receiving information it’s important to have stronger technology to ensure that malicious software can’t be added.
One of the greatest areas of contention when it comes to IoT is the proliferation of tracking software. Hackers can install data-packet tracking software to track what information is being sent. This gives them an open-portal through which they can attack a secure server. Hackers can also create backdoor channels that can be used to leak data easily.
There aren’t clear standards yet on the utility of IoT and its security. However, CCOs need to create their own unique models of IoT security. These include firewalls at the device level and the network level, so as to protect the entire framework from hacking or penetration.
Updating the standalone firewall is critical as well. It’s important to have complete control over who is accessing your database and which parties can enter the core network.
A sample IoT firewall is referenced above, which is an intermediary firewall specially designed for the IoT infrastructure. The firewall acts as the middle man that tracks various interactions between data servers, networks and devices.
Network-based Firewall vs Application-based Firewall
CCOs need to opt for both network-based firewalls and application-based firewalls for better protection. Web apps are being targeted daily, as hackers try to gather information from these applications. That’s where a coherent firewall strategy needs to come in to the picture. CCOs need to design better information architectures to be able to provide increased security.
“A WAF blocks attacks targeted on websites, web-based applications, as well as the web server infrastructure. Network firewalls blindly allow web traffic through to servers and intrusion prevention solutions only protect against a subset of web-based threats, so WAFs have become essential for defense in depth security. A compromise of web applications allows attackers to steal information from the connected databases or infect other users of the site with web-based malware.” – Neeraj Khandelwal, Sr. Product Manager at Barracuda Networks
At the application level SDP (Software Defined Perimeter) has made strides in tackling challenges in the firewall reach. Patch management, end-point/device enforcement and multi-factor authentication can be made stronger using advanced firewall technologies.
The challenges to implementing a company-wide web-app protocol is configuration for each application. Firewalls must be designed independently of the source of the app. That makes the task that much more complex and resource-intensive. However, when CCOs review each app and create a firewall architecture around it, it makes the entire company that much more compliant overall.
When CCOs have a coherent WAF and NF strategy, then they need only focus on maintenance and upkeep. Areas such as security patching, networking, and threat assessments is critical to understand in-depth. CCOs need to run constant testing parameters to enable the company to have a better outcome security-wise.
Since WAFs can offer immediate remediation and active blocking, they are the preferred tool by CCOs to prevent against hackers. These tools can also be used at scale and adopted by a number of organizational areas of excellence. Third-party modules, attachments and plugins can also be monitored better, giving rise to a more consistent approach to network security.
For a more coherent network to be deployed, both NAF and WAF are important to structure.
PCI Compliance and Firewall technology
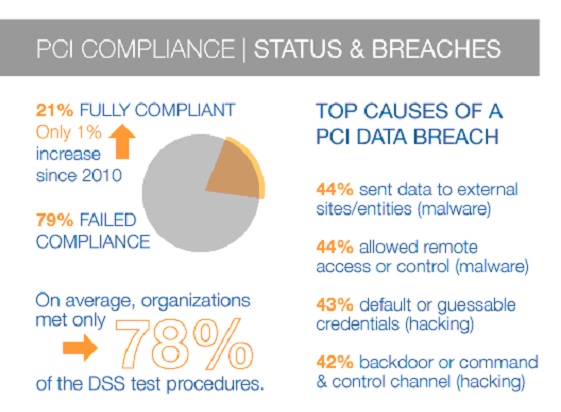
There are various industry bodies that have their own compliance related regulations to follow. When it comes to firewall security, it’s important to have proper protection when remaining PCI compliant. Scale does not matter when it comes to PCI compliance and handling customer data. Companies must have –
1. A robust firewall policy and framework present within the organization.
2. Testing mechanisms to review the strength of the network and firewall.
3. A fully customized tracking and monitoring dashboard for traffic flow.
Companies need to focus on enhancing the overall strength of the firewall if they are to remain compliant to PCI standards. Additionally, to scale along with rising demand, it’s critical to have a coherent firewall policy around your company. With 90% of retailers failing against common PCI regulations, it’s up to the savvy CCO to strengthen its networks.
“As part of the process, organizations need to build firewall and router rules that restrict inbound and outbound traffic. These restrictions need to specify all ‘untrusted’ networks and hosts, especially wireless ones. As part of this restriction, no public access can occur between the internet and system components in the Cardholder Data Environment (CDE).” – Research Analyst at Security Scorecard
PCI compliance also revolves around effective controls over firewall security. When CCOs understand what aspects are being monitored effectively, they can develop robust checks and balances.
CCOs can also develop the right strategy to tackle PCI DSS first-hand. Since this gives them leverage to develop new technologies, it enables the ecosystem of tech security to open further.
PCI DSS also mandates stricter firewalls for global transactions as well. Since the compliance norms dictate global interactions as well, companies will have to create better firewalls that focus on international traffic.
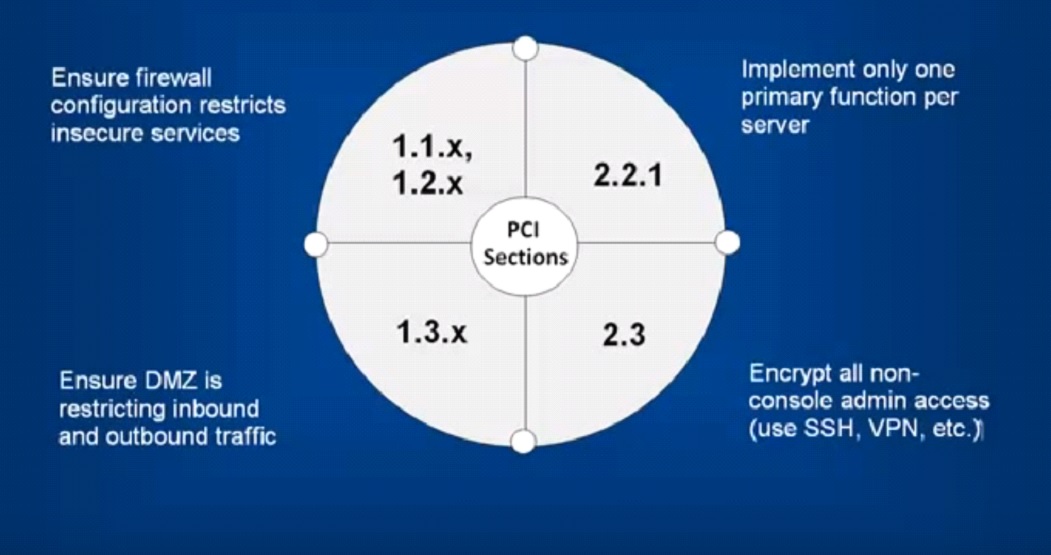
The firewall needs to remain compliant to existing PCI regulations as well as act as an enabled in other primary regulations as well. Requirements 1 and 2 of the PCI DSS protocol specifically address firewalls, making it important to remain compliant.
When companies need to ensure DMZ is restricting inbound and outbound traffic, firewalls can help curb leaked information flow.
Additionally, in the case of server roles, firewalls can help in controlling any unauthorized access or multiple traffic flow into server databases. There is a wide scope within the PCI framework that firewalls can help in ensuring compliance.
Insecure services using non-compliant pathways can also be instantly rejected bases on their status. This enables CCOs to have better control using their firewall. They can review the intrusion detected at a later date but have their firewalls be the primary source of capture and protection.
Firewalls also help CCOs enforce internal compliances to PCI regulations. The technology can help the company remain compliant against any rule breaks. Since behaviourally, the challenges may keep mounting up, from a technology perspective there is clear and present control.
Investing in better firewalls is a coherent strategy once scale is in picture. CCOs must ask themselves – will better firewalls create business advantages? If the answer is yes, then that’s a pathway that they’ll have to approach.
The final element of the piece is employee understanding. Whether employees understand the advantages of using a firewall should be the critical criteria. Employees need to understand the nuances behind PCI compliance and remain within guidelines that have been approved.
Employees also have to be aware of terms like tokenization and compliance-norms that are related to their industry. This helps in adopting PCI related firewalls better and enables companies to scale with the help of their employees. When every employee is on-board there is a sense of uniformity in compliance.
CCOs need to conduct regular training sessions with their employees to keep them updated on new firewall policies and changes in the way that they’re approaching compliance.
CCOs also need to constantly update the firewall technology itself and teach employees how to update end-points manually if there is a need to do so. Hackers can gain easy access into firewall protected databases if there is a compromised end-point.
Smart Enterprise Border Protection
When it comes to firewalls, the company should view the architecture as an enterprise asset that needs protection. Through this thought-process, it can create multiple layers of additional firewalls within critical assets. This shifts the perspective of the firewall to a more border-protection oriented process.
Even for compliance purposes it’s a more robust strategy. While technology changes and more advanced forms of firewalls are presented, the overall philosophy remains unchanged. CCOs that focus on firewalls from an intelligent enterprise perspective become future-ready.
Using AI, machine learning and firewall testing processes, CCOs are able to make their infrastructure that much more secure. They’re also able to provide better mechanism for remediation, in case there is a hacking attempt discovered. There is an increased sense of trust when we look at our current protocols from an intelligent enterprise perspective.
Border protection also implies how we review cases from a holistic perspective. Earlier firewalls were just seen as a passive technology that didn’t allow intruders in. Now, CCOs are seeing firewalls as an active technology that finds gaps in the perimeter where hackers could attack.
“An AI-based firewall solves problems such as time-consuming threat detection and coarse granularity of traditional threat-detection technologies. The introduction of AI technology and virtualization architecture enables next-generation firewalls (NGFWs) to “intelligentize” enterprise border protection. The AI-based firewall makes [solution] realize dynamic collaboration between software-defined security products through open architecture and implement intelligent collaboration between on-cloud and off-cloud services through centralized intelligence and edge intelligence, to greatly enhance enterprise network immunity.” – Denzel Song, General Manager of Huawei Network Security Domain
Companies that focus on smarter firewall protection also have better firewall policies surrounding the core technology. As the mission and vision of the company shifts, so too must the firewall policies. Firewall policies are being seen as structural pillars on which the company can rests its security framework. From technology standards to single-case protocols, firewall policies are changing rapidly.
Configuring smarter firewall policies
Firewall policies need to be configured in a way to enable smarter growth and better control over the network infrastructure. Modifying existing configurations is the start of the process, along with accessing rules and lines of traffic flow. Inspections can be performed on the firewalls that are already structured within the company.
CCOs must map out the router configuration and network being used as a whole. This provides compliance officers a better vantage point for when they need to make strategic changes. Using multiple interfaces on an existing configuration is an additional step that can also be performed.
Setting out the right rules and restrictions is key when it comes to configuring smarter policies. It’s important to understand what area or management level is able to access what data.
This is even more so pertinent when it comes to new clients that need access to critical information. In this case, it becomes increasingly important to have strong firewall policies that restrict unwarranted access.
Configuring traffic flow
One of the most important elements of a robust firewall policy is to configure the right traffic flow. This enables greater control over compliance related matters, especially when it comes to certain data centres and out-going transfers. Routers that are placed within the network can also be configured well in advance.
This traffic flow can show CCOs originating and returning traffic, allowing them complete transparency when it comes to networks. This enables CCOs to take deeper action when it comes to analysis and remediation. There can be errors or disconnected routers that could lead to a potential data hack through that layer.
This helps CCOs design better firewall compliances as well. Firewalls can be setup once the entire architecture has been mapped from a traffic flow perspective.
Access rules & controls
CCOs can setup unique rules and controls for certain zones within the network. This can allow CCOs to have more perspective over the traffic that is flowing through the network. By adding rules on access, entry and user-credentials, a firewall can be setup in terms of providing or restricting flow.
Data packets can have added rules within the general framework and certain data centres can be restricted to all. This general view can help CCOs design better policies round access control as well. CCOs can enable access to certain developers or IT admins only in certain situations at certain levels. Although this introduces a level of complexity into the system, it also creates better efficiency and security.
CCOs can also assign controls over specific domains. E.g. a file from finance travels to marketing, and a firewall picks it up as a violation. This can be designed to protect either department from sharing information that isn’t relevant. Additionally, CCOs can design firewalls to prevent unauthorised downloading of any single file or folder’s content.
This level of control only an intelligent border control system can provide.
WAN, LAN, WiFi control
It’s important to design better firewall policies from the perspective of the network being used as well. As the network scope wides, so too must the policies being leverage. For organizations with WAN and LAN interconnectivity, there is an additional layer of policies that must be formulated as well.
As data is transferred from one network to another, there is information that is being transported. This information can be hacked into by third-party players that are listening for exchanges. Therefore, firewall policies must be put in place in the case of data transfer and connected distributed devices.
For remote transfers of information and web-traffic flow, there need to be unique firewall policies designed as well. These policies allow companies to share information within a specific framework so that they’re compliant with all polices established.
Additionally, as networks move from LAN to WAN, there is a need for scaled firewall protection which is something that falls under the CCO purview. Compliance officers must study the network comprehensively to find areas of policies that need to be formulated. These policies can fall under general or specific instances of data and traffic flow.
Firewall workflow and reducing complexity
One of the greatest challenges being faced in the cybersecurity domain is the complexity in firewall structuring. Since each department has a unique rule and each transfer has a unique flow, there can be times where complexities arise. CCOs have to deal with multiple layers and stacks of compliances that are added to data transfers as well.
That’s why CCOs need to create a robust firewall workflow and decrease human-intervention where necessary. This increases the efficiency of process automation and creates a robust library of rules that can be followed anywhere. End-point devices get a simple message telling them about the restrictions if they’ve made an error in transferring a certain file.
Allowing firewall workflows to become less complex allows companies to become truly lean. They can take action that much faster, along with suggesting remediation at a faster pace. CCOs can also obtain critical information about who tried to log-into the system and at what zone. This gives CCOs more leverage in taking the right decision at the spot.
If there has been a breach, then the transparency built into the firewall workflow allows for quicker decision making. Information about the breach can be obtained much faster, allowing CCOs to escalate the situation accordingly. Whether a certain firewall was breached, or it was a general attack, the workflow will allow you to take the right call.
When there is increased complexity within the system, there is a chance of there being details that are lost within layers. This occurs when a specific instance or workflow has multiple owners or access log-ins that require their own rules to be setup.
This also occurs when different people try to access the same data at the same time. There may be errors in sharing information across the servers, and the router may be of an incompatible model. There are always chances of there being problems that arise from increased complexity. Ensuring that the workflow is as synchronized as possible is key.
Updating the workflow is essential as well. Firewalls need to be updated regularly to keep up with shifting trends. As CCOs start to analyse their current systems, they can prepare new models that work better over time. Workflows can be designed to be coherent and self-updating, along with technology needing to be replaced.
In order to maintain firewall policies compliance, it’s important to have a streamlined workflow. Reducing complexities in layers and rules is important as well.
Types of enterprise firewalls in organizations
There are 5 major types of firewalls that exist in the marketplace, each having their own unique purpose. Their application is also unique to the design and can be fitted in a specific or general instance.
There are also hybrid and new-gen models of firewalls that are required at multiple levels within the firewall architecture. The network of the firewall also needs to be optimized prior to installing any specific type of firewall. Packet filtering may be the most common form of firewall, dealing with information entering the system in the form of packets.
Additionally, there is a chance of hacking at either layer of firewall optimization if the firewall is outdated or the pathways are incorrect. The core technology may also be corrupted by alternative means, in which case CCOs need to strengthen their compliance policies.
Each type of firewall has its own advantages and disadvantages, which is why CCOs need to establish their own type of firewall network. If there are certain criteria that are fulfilled by a specific firewall, then another one needs to be installed to ensure that another one is satisfied.
This is how the sophisticated CCO would design their network infrastructure and firewall framework. There need to be multiple points noted out that can be infiltration zones. These zones would have to be protected with a firewall that is present to protect that area. Whether that be a data cluster or the cloud application being run around the server, there need to be robust firewall models around the systems.
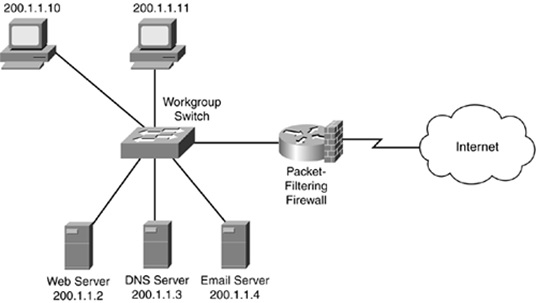
Packet Filtering Firewall.
Packet filtering firewalls are deployed on the router itself on the network layer of the model. It’s an important type of firewall that all internet connections must have ready and built-in. A reference of a basic packet filtering firewall architecture is shared above.
The rules defined by Access Control Lists control the flow of traffic incoming. The ACL checks all the packets against the IP rules allowed, as well as screens the packets against pre-existing conditions set.
There is a regular log maintained under the PFF model and hackers can’t read the packets unless they’re authorized under the routers’ internal ACL. That’s why packet filtering is considered an important first-step towards building a more robust firewall system.
Packet filtering doesn’t check the payload that is being transferred. It doesn’t verify the individual connection as well. It simply references the incoming traffic against a set of rules around the connection. It then allows the connection to pass through if the rules are met with. CCOs can set a PFF to be the front-line of defence in the case of an enterprise firewall setup.
Circuit Level Gateway Firewalls.
CLG firewalls go deeper into the session itself to understand whether the connection is secure or not. The source is also checked whether it is legitimate or not. The firewall monitors sessions like TCP three-way handshakes to measure whether a connection is truly from the right source.
Having CLG firewalls are a smarter way to protect the organization against infiltration because it goes deeper than router-level protection. The layer of screening occurring is such that the payload on the connection is reviewed as well.
This gives CCOs more power and control over the information being shared over a network. It also helps in giving more power to the compliance team to measure which attacks have been conducting using what malware or trojan.
CLG also provides anonymity to the private network and is a cost-effective method to maintain essential security. It goes one layer deeper than the generic packet filtering model and understands the connection-type that has been established therein.
Application level Gateway Firewalls.
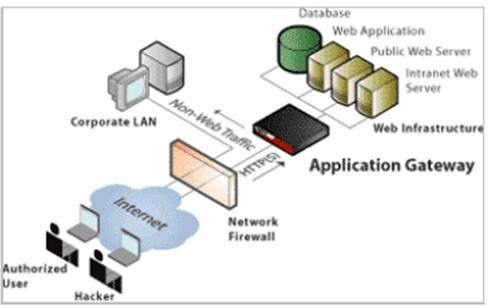
Application level gateways are designed to work on the application layer of the network model. They provide protection for a unique application layer protocol. CCOs can set the firewall to only allow HTTP protocol data to flow through the connection.
A reference of App gateway firewall is shared above. In an enterprise, it’s important to have a strong application gateway firewall installed. CCOs can gain stronger control when there is a proxy or application gateway installed within the network architecture.
It can also allow only using dynamic TCP or UDP ports to communicate with the known ports despite the firewall configuration allowing limited known ports.
It serves as an application proxy firewall providing a stronger level of network security. Both ends of the network don’t know the identity of each other, with the proxy server creating a barrier in that regard.
It’s a more secure method of transferring information and connecting from one server to another. It can help in filtering incoming node traffic to specifications that are only transferring network app data. In other words, it allows for greater filtering in the connection.
Stateful Multilayer Inspection Firewall.
The SMI Firewall is one of the strongest ways to ensure that there is no infiltration from an unauthorized source. It uses a sophisticated form of packet-filtering that goes through all 7 layers of the OSI model.
Every single packet is examined and compared against referenced friendly packets. This helps in double checking every information packet that is passed from one end to another.
While the entire packet is screened, it adds an additional layer of protection throughout the entire network. It’s also considered to be a combination of all firewalls shared above. Using ACLs, it can check for legitimate session layers and evaluate packets on the application layer.
It can also work on the transparent mode and allow direct connections between the client and server. This adds challenges when it comes to compliance, but the SMI firewall is generally seen as a compliance enforcement tool.
It creates a more secure packet sharing protocol wherein the information is sent in a more controlled manner.
CCOs can implemented algorithms and complex security features that can make the protocol more secure. These algorithms can be designed to make the actual transfer more secure as a whole.
Next-Gen Firewall.
The NGFW is a third-gen firewall technology that can be deployed as a hardware or software application. The overall technology can be implemented to detect and block sophisticated attacks. Security policies can be enforced at the application, port and protocol levels.
These firewalls combine the capabilities of traditional firewall technology with quality of service (QoS) functionality.
These firewalls are deployed as active intrusion detection technologies that are capable of defending against sophisticated attackers. They combine features such as packet filtering, network address translation and PAT. They can also perform VPN and URL blocking capabilities.
Maintaining firewall policies compliance
Objectively reviewing the need for a firewall policies compliance structure, CCOs can start to notice patterns emerging. There is a need for greater compliance and firewall protection required throughout the organisation.
However, where most compliance programs fail is the human element. Organizations run on effect compliance programs and employees need to be the first ones informed about changes and best practises.
CCOs that develop robust programs involve the employees from the first day of launch. They enable employees to make their own decisions while empowering them with the protection of a robust firewall present.
That’s why CCOs need to focus on generating clean traffic for all transactions that occur within the network. When the traffic is clean, and the data packet doesn’t have intrusion markers, companies can reach greater heights through data protection. These companies are also better enabled to reach out to new clients that may have their own robust firewalls present.
Essentially, CCOs need to design a program that enables companies to have greater access to resources. Protecting these resources should be the ultimate goal of the CCO who needs to create deeper strength within the organization.
The end goal of the firewall is to create better protection, which is why CCOs need to constantly design policy compliances that allow for greater flexibility.
Since the dynamics of the internet age are constantly changing, CCOs need to create unique solutions for each data centre or each organizational head. This allows companies to focus on growth and not worry about their data being hacked through a network intrusion.
3.8.1 Packet filtering firewalls
What is a Packet Filtering Firewall?
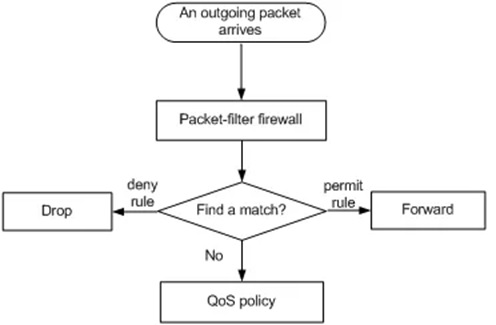
Packet filtering is also commonly referred to as static filtering as it conducts a generalized test to determine the connection. It’s a simple firewall technique that is used to control network access by monitoring the connection directly. This allows CCOs to understand the type of traffic coming in and what information is being shared.
The packets aren’t individually checked, as the firewall doesn’t have the right capabilities to perform these tests. They can block traffic incoming and outgoing by the monitoring capabilities provided to them. Additionally, they can review the IP addresses, ports and protocols through which traffic is coming into the network.
CCOs need to understand that PFFs are the first-line of control when it comes to securing their network. However, they’re not sophisticated enough to create a robust secure network around. Firewalls need to deeper than the IP level, as hackers become increasingly sophisticated around what tools they’re using.
Network layer firewalls define the packet filtering rules that allow traffic to go in and out of the system. These rules can be put in place by compliance officers that require increased control over the organisation.
The resulting filtering allows for greater transparency at the network level. The access control rules can be set by the CCO who can determine whether certain traffic sources need to be blocked out.
When considering the interactions that occur outside of the LAN, it’s important to have a robust packet filtering firewall setup. The firewall helps in ensuring that the traffic is protected against attackers at the IP level. As hackers can spoof their source of origin, they can get detected if they don’t match the incoming rules.
As the node transmits a packet that is filtered it needs to be matched to the rules set in place. Once it clears the rules, the packet is accepted otherwise denied from entering the system. This rule can be set inside the network within an organization or traffic flowing outside it.
For CCOs that want increased control over what files are being shared over the network, this is an effective tool to ensure compliance. PFF checks both the source and destination IP to review the verification of these points. Using UDP and TCP, PFF is able to double-check on every incoming transmission.
Incoming packets can also be reviewed against guidelines that can be edited at any time by the CCO. This means that originations can grow and the CCO can support their growth through managed packet filtering.
Stateful and Stateless Packet Filtering
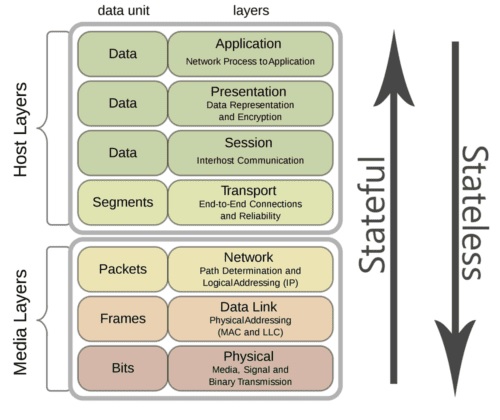
For compliance purposes it’s important to understand the key differences between stateless & stateful firewalls. Both types of firewalls perform packet filtering but use different methodology to perform the action.
Stateless firewalls allow the packets entry into the network based on the rules set in place. The router checks the static information presented by the packet and allows the passage of the information.
It doesn’t review the packet or try to gain more information about the data being shared. That’s why it’s a static method of packet filtering, and it views packets under the wider lens of web traffic. It will not review them in isolation or control the flow of packets based on contents.
This can open up possibilities of hacking, as attempts can be made to bypass the initial filter. Since stateless firewalls don’t keep a track of the status of the network, hackers could share files using a pre-existing connection. They only check the header of the packet and not the packet itself.
When it comes to stateful packet filtering, the firewall is able to keep a track of the state of the network. It’s also more context-sensitive, in that it can understand the context of the transmission.
It has memory in terms of reviewing a packet in terms of seeing it before. Once it acknowledges the context of the incoming traffic, it can trigger a response. It can either allow the packet to enter or disallow it.
This is a more secure way to determine malicious intent, as there is active memory involved when it comes to stateful. Stateful also ensures that there is a clear difference demonstrated between clean and malicious traffic.
Stateful can also watch traffic streams from end to end. It’s aware of the communication pathways and can implement security features including encryption and tunnels. It’s also provides more power to the CCO who can determine the strength of the network by implementing active stateful firewall protocols.
Stateful can also tell CCOs what stage a TCP connection is in – open, sent, sync, etc. It can tell the admin if the MTU has changed or not, and whether the packets have been sent. Stateful is one of the best tools available to enforce firewall compliance from a technological perspective.
CCOs need to have a robust strategy around stateful and stateless, implementing them where it makes most amount of sense. When there is the question of transferring sensitive files over a network, the stateful firewall can provide increased security.
It can give CCOs more information about the connection, what packets have been sent and what is the progress of the transfer.
From a compliance stand-point, employees should know what connection and what firewalls to leverage. If they’re sending certain files over a specific network, then the firewalls present should be made aware to them. This saves resources in terms of using the correct pathway each time. It also creates a more balanced approach to monitoring data transfer across pathways.
Additionally, CCOs need to understand the impact that packet filtering offers from a security stand-point. When certain pathways are used for monitoring and switching between data servers, CCOs can have more control over information flowing. They can design better systems to ensure that there is more control over the infrastructure. They can create workflows that ensure that all forms of data can flow through a previously approved pathway.
Whether there is special access required, escalates up to the CCO office who can then make the final call. This makes the entire process more systematic and oriented.
3.8.2 Circuit-level firewalls
What is a Circuit level Firewall?
Circuit level gateway firewalls essentially work at the session layer of the network. They monitor the TCP handshake between packets to ensure that a requested session is secure and from a legitimate source. It’s a good way to enforce compliance rules around secure data transfer, when the information is passed through a circuit level.
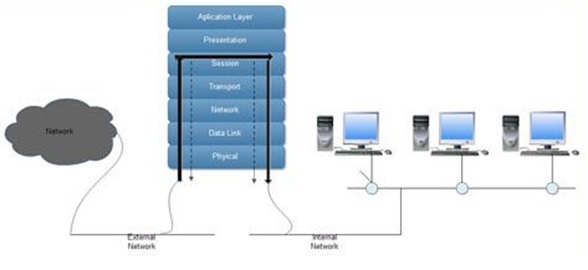
From a technical stand-point, a proxy server is a security barrier between servers. The entire gateway firewall is a virtual circuit between proxy servers and the internal client receiving the information.
It’s a more secure way of sending packets and it creates a layer of anonymity between parties. As none of the user information is passed on through the layer, it’s a more secure way to send data.
The downside of using CLG firewalls is that packet level filtering is not available. After the connection has been established, a hacker may enter the network through malware and send out malicious packets through the connection.
The capturing of the event may also take more time as there is limited technology available to review individual packets. While the three-way handshake is a legitimate method of reviewing the connection, CCOs need to add more firewalls to ensure that the entire network is made secure.
The added bonus that CLG provides is screening at the connection level. Once the rules are set in place, the CLG ensures only secure connections are allowed through the network to access information.
This enables them to become a tool for compliance from a network level. Whether employees are using the right network or right protocol happens automatically at the network level. This helps in creating a stealthy cover when businesses are transferring information.
Hackers are unable to receive information via network hacking tools, as the identity of the users is hidden.
The advantage of using CLG is in its scale. CCOs can scale up the CLG firewall architecture as and when companies increase in size. They can also be used to create secure connections between a client and a business.
It also frees up valuable resources in terms of network checking and any manual network reviewing.
The tools offered by most technology vendors allow CCOs to manage the network through a myriad of layers and lenses. They can review individual traffic flowing or access the general view of information flow.
CLG also creates a security parameter for companies to leverage, as it disallows unauthorized access. From a purely access point of view, CLG works well as a compliance tool for large-scale operations. It’s a source of great strength and security.
Circuit level Firewall & Compliance

Circuit level gateways should be used in conjunction with other firewalls within the organization. While being powerful, from a compliance perspective, they need to have additional firewalls working together as well.
When an application is launched or there is a request for information, there are various circuit level gateways that get activated. This is precisely where CCOs can introduce a firewall so that these activities can be monitored better.
From a level gateway perspective, the firewall will ensure the following –
⦁ Confirming whether the Source IP address and port is valid. Only then allowing the packets to flow through the firewall.
⦁ Ensuring that the Destination IP address and port is per the connection. Validity is checked, and verification protocols are followed through.
⦁ The actual application or protocol is verified as well, to ensure that the packets are being sent via a secure method.
⦁ Authorization (Username and Password) is verified to ensure safe log-in and complete transparency.
⦁ Handshaking protocol and sequence numbers are verified to make the connection more secure.
3.8.3 Stateful inspection firewalls
What is a Stateful Inspection Firewall?
Stateful inspection combines different aspects of dynamic packet filtering, circuit level gateway and application level firewalls. In essence, it’s a combination of the major forms of firewalls in the organization. A stateful inspection can also function as any one of the firewalls mentioned above, making it a robust solution from a compliance perspective.
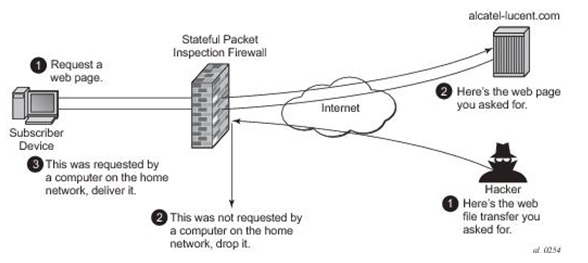
Stateful inspection can function as a circuit level gateway and estimate whether the packets in the session are right. The SI firewall can verify inbound SYN and ACK flags and sequences. The firewall also operates as a dynamic packet filter blocking out nefarious instances.
A limitation in older SI technologies is that it may not be able to inspect sequence numbers on outbound transmissions. This means that there is a minor loophole through which hackers can spoof IP address of employees and open a gateway accordingly.
While this can become a major flaw in the firewall, savvy CCOs understand the importance of having a multifaceted firewall architecture.
Stateful can also mimic an application level gateway, leading to the inspection of the packet contents themselves. This is the most important area of impact that stateful performs, wherein it can review the information being shared and allow/block based on that context. There are rules that can be set by the CCO, who can then direct traffic accordingly.
Since the cyber compliance domain dictates control over information flowing, there is a sense of authority that is provided by stateful firewalls. These firewalls can become a core part of the enforcement aspect of the infrastructure.
When the content matches the rules set in place within the administrative framework, it creates a multidimensional zone of protection. Stateful offers inspection across all 7 layers of the OSI model and CCOs are able to configure the firewall as per their organization. Specific filters can be set in place to enable greater control over the domain of network security.
Since stateful operates as a firewall it provides an integrated dynamic packet filter. Remaining compliant to multiple industry regulations and rules becomes easier, as more companies move towards the firewall-first model.
Additionally, it allows companies to review their security measures from an active-firewall perspective. CCOs that understand the importance of firewalls opt for a stateful firewall approach, especially for their valuable data assets.
The single-thread processes of stateful can have an impact on performance and speed. In smaller-scale companies, this may put barriers (although essential) which may slow operations down. However, CCOs can develop faster workflows that don’t rely on speed for effective execution.
Stateful Inspection & Compliance
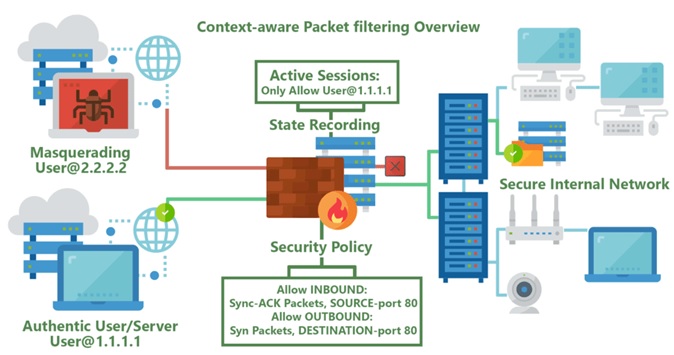
Stateful inspection offers compliance officers a more robust firewall protection. CCOs need to map out their organizational firewall strength to determine the layers that rely on increased security.
From setting security policies to enforcing compliance on internal-transfers, it’s important to have a comprehensive approach when setting compliance programs.
CCOs need to have stateful inspection be a core part of the overall firewall security picture. From creating best practises to enforcing the right rules within the framework, there are multiple challenges that CCOs need to overcome. Through the power of technology and the aid of employee training, CCOs can design a more robust program relying on better handling.
As the company grows, more clients get added to the list and more complexities arise. Stateful helps in ensuring that all companies use a uniquely designed port-way and protocol. The inspection firewall also gives more control to CCOs who can review the flow of packets across specific channels.
If there is a channel that is driving unauthorize packet transfer, then the only to catch that in time is using stateful. Therefore, it’s a great too to measure the security of other stakeholders that are working with the organization.
3.8.4 Application-level gateways
What is an Application-level gateway?
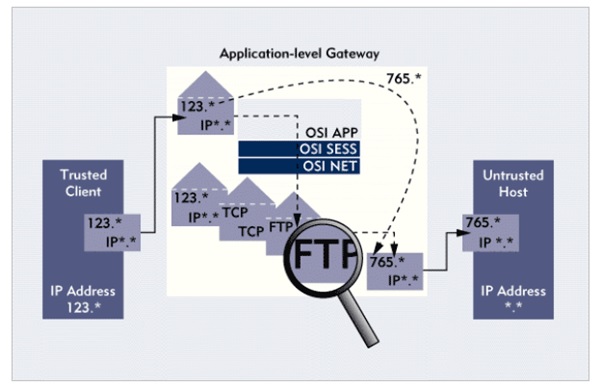
An Application level gateway will operate in the application layer of the OSI model. It actively inspects the contents of the packet and disallows bad packets flowing through the network.
The gateway acts as an intermediary between LAN/WAN and the application server. When relevant information is passed through the network, the firewall starts to deep dive into the content being shared.
This could be for both incoming and outgoing data packets and can be configured according to the best practises listed by the CCO.
The proxy server or gateway acts as the end client when interacting with the greater network. This helps in controlling the flow of information from the inside out.
The identity is well protected and the proxy acts as the main lead in the network. Information can still flow through using sophisticated hacking tools, but the proxy server can review the contents being shared.
When the gateway then sends a fresh request, it validates the transmission from its previously recorded rules. This helps in double-checking the traffic coming into the system.
The gateway essentially intercepts the packets and runs a proxy to copy forward the information. This prevents any direct connection between the two servers, making the connection that much more secure.
This works out perfectly when organizations need to formulate pathways to transfer sensitive data. A connection can be drafted based on the gateway, along with information being passed in a secure manner.
CCOs can prevent any direct connection between trusted servers and untrusted hosts, giving rise to a more secure transmission. Since hackers can infiltrate the system using sophisticated tools, application gateways serve as the perfect intermediary.
The gateway can also allow client applications to use dynamic TCP and UDP ports to communicate with the known ports. The firewall configuration can also allow a limited number of known ports so that there can be increased focus on security.
If there is no rule setup for a specific type of connection, then that connection is directly disallowed to interact with the server. This helps in understanding how the payload can get affected if there is no rule setup. It also increases security within the company as a network.
Compliance and Application-level gateways

Application level gateways function on the application layer of the OSI model. This adds increased security within the firewall framework. Additionally, this creates more control for the CCO who wants to understand how data is shared within the organization.
ALG firewalls are able to provide more information to the CCO who wants to understand how packets are being delivered. It provides increased transparency throughout the network, while giving more control over to the compliance teams.
That’s why compliance officers use ALG firewalls to create additional layers of security within the framework. From a compliance stand-point, CCOs stand to gain multi-fold from correctly implementing ALG firewalls.
3.8.5 Next-gen firewalls
What is a Next-Gen firewall?
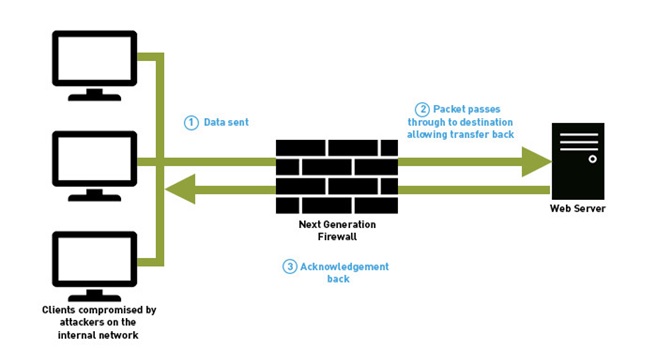
Next-generation or next-gen or NGFW firewalls are a hardware or software-based security system that combines traditional firewalls with additional features.
These features could be customized based on the organization’s requirements or filtered through each segment or area of excellence. It ultimately depends on what level of security is desired within the network, and what is the scope of work for these firewalls.
Next-gen firewalls can block out intruders and actively hunt for them around the perimeter. These Next-gen firewalls can create better compliances for CCOs to monitor, as well as provide a daily report on the instances corrected.
“Basically, next-generation firewalls do deep packet inspection. If they find something that’s bad, they reroute it, they sandbox it [and] they protect the organization against it. You can use next-gen firewalls to do things like enable internal and external traffic segmentation. So, for example, you can segment traffic on your network, so stuff that you deem inappropriate for certain parts of your organization [goes] in certain places.” – Johna Till Johnson CEO Nemertes Research.
Having an integration-focused approach is key when thinking about next-gen firewalls. That is because then CCOs can determine the right approach and standard protocol to analyse the framework.
Additionally, CCOs can design their own algorithms to protect the company from attackers that may have accessed the network. Next-Gen provides remediation plans that automatically follow best practises within the organization.
From a compliance stand-point Next-Gen offers critical tools that can be leveraged to enable better security. From tracking to active look-out, Next-Gen is the future that should be implemented across the enterprise. CCOs have more tools when they leverage the full extent of what Next-Gen can offer to the table.
As employees become more mobile and there is more processing being done in the cloud, Next-Gen firewalls offer more protection and standardization across the board. CCOs have dashboards and standard tools to enforce compliance. Employees also understand the extent of work needed to ensure compliance as well. Overall, it creates an environment of compliance that goes beyond traditional firewalls and network security.
Proliferation of Next-Gen & Compliance
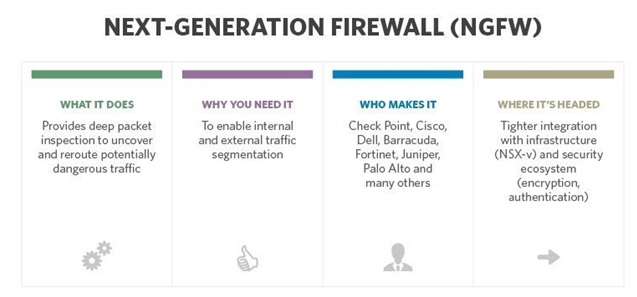
It’s important to think about the entire ecosystem of Next-Gen. From what it does to where it’s going, CCOs need to understand all the nuances of this firewall technology. Additionally, there are various tools available to CCOs who can determine the best approach for Next-Gen in their organization.
As more organizations delve in remote access, IoT, AI and machine learning, there is a sense of urgency when it comes to Next-Gen. That’s because the technology provides a complete gamut of solutions under one umbrella. From a compliance perspective, it works out perfectly for CCOs that want to remain ahead of the technology curve.
There is also an element of protection that Next-Gen provides that is unmatched in the market. From threat detection to triggering infrastructure intrusion plans, the level of automation brought on board is extensive. This enables companies to focus on growing through their lifespan.
Security becomes a true asset that is scalable across domains and can be applied to improve the industry’s ecosystem. The company becomes a real thought leader in the security space when using Next-Gen solutions. Firewalls, done traditionally, have many loopholes that hackers can exploit. When it comes to Next-Gen, there are few instances through which hackers can gain access.
Employees need to be well-versed with using Next-Gen firewalls, especially when it comes to leverage the scope of the technology. From simple file sharing to sophisticated data-networking, there is a wide scope of solutions that Next-Gen offers.
References, papers & e-books
https://community.fs.com/blog/network-switch-router-firewall-why-need-all-three.html
https://www.networkcomputing.com/networking/enterprise-firewall-checklist/702944892
https://www.ptsecurity.com/ww-en/analytics/webapp-vulnerabilities-2017-q4/
https://medium.com/@MyanaSmlia/before-blockchain-after-blockchain-in-business-d222c6e98d48
https://www.zdnet.com/article/palo-alto-networks-to-launch-next-gen-firewall-for-5g-networks/
PCI – https://www.youtube.com/watch?v=gkYLkOCB51c
https://securolytics.io/products/iot-security/iot-firewall/
https://www.coindesk.com/r3-launches-corda-enterprise-with-first-ever-blockchain-firewall
https://www.infosecurity-magazine.com/news/over-90-of-us-retailers-fail-pci/
https://www.ipv6.com/gateways/alg-application-level-gateway/
https://i1.wp.com/sanketrjain.com/wp-content/uploads/2015/01/packet_filtering_firewall_2.png
https://www.slideshare.net/PinaChhatrala1/types-of-firewall-53269158
https://infoproducts.alcatel-lucent.com/html/0_add-h-f/93-0267-HTML/7X50_Advanced_Configuration_Guide/AA-FW.html
https://www.webopedia.com/imagesvr_ce/8023/7-layers-of-osi-icon.jpg
https://www.nexor.com/firestorm-next-generation-firewall-vulnerability/
https://www.techopedia.com/definition/30649/next-generation-firewalls
https://www.paloaltonetworks.com/products/secure-the-network/next-generation-firewall
https://www.networkcomputing.com/networking/5-benefits-next-generation-firewalls/57886367
https://www.cisco.com/c/en_in/products/security/firewalls/index.html
https://www.barracuda.com/glossary/next-generation-firewall
http://www.cisoplatform.com/profiles/blogs/9-top-features-to-look-for-in-next-generation-firewall
https://www.skyboxsecurity.com/solutions/firewall-security-and-auditing
https://www.fortinet.com/solutions/enterprise-midsize-business/network-security.html
https://www.cisco.com/c/en/us/solutions/enterprise-networks/pci-compliance/index.html
https://searchsecurity.techtarget.com/feature/The-five-different-types-of-firewalls
https://www.esecurityplanet.com/network-security/firewall-types.html
PCI Compliance: Understand and Implement Effective PCI Data Security Standard Compliance 3rd Edition by Branden R. Williams
Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance (Theory in Practice) 1st Edition by Tim Mathe
Integrated Security Technologies and Solutions – Volume I: Cisco Security Solutions for Advanced Threat Protection with Next Generation Firewall, … Security (CCIE Professional Development) 1st Edition by Aaron Woland

