- SCADA Security Hacking Story: New York Dam - 24/07/2023
- Phishing Story: Yahoo - 17/07/2023
- SCADA Security Hacking Story: Target Stores - 13/07/2023
What are risk assessment and risk treatment? and what is threat intelligence? is there any difference between the two? if yes, what is the difference? explain it with an example
Risk assessment and Risk Treatment are the major components of a risk analysis process.
Risk analysis is a multi-step process to identify and analyse all possible risks and issues that could be pernicious to the business.
The critical elements of this process are
– Risk Assessment
– Risk Communication and Consultation
– Risk Treatment
– Monitor and Review
– Recording and Reporting
Risk assessment is the organizational process of identifying, analyzing, and evaluating potential risks or hazards inherent to an instance or location and their impact on an organization, project, or activity. It involves assessing the likelihood of a risk occurring and the severity of its consequences. Risk assessment aims to facilitate the creation of efficient risk management plans and informed decision-making.
It comprises of:
— Risk Identification
— Brainstorming
— Checklists
— Interviews
— Delphi Techniques
— Nominal Group
— Causal Factors
— Hazid & RISKID
— Risk Analysis
— What–If Analysis
— Fault Tree
— Event Tree
— Now Tie Analysis
— LOPA
— Stripped Bow Tie
— HACCP
— Risk Evaluation
— Risk Indices
— Risk Matrices
— ALARA/ALARP
— Fault Tree
Risk Treatment: Risk treatment refers to the process of selecting and implementing strategies to manage or mitigate identified risks. It involves actions such as avoidance, mitigation, transfer, acceptance, or exploitation.
This includes:
Hierarchy of Controls
– Cost/Benefit Analysis
– Financial Benefits
– Non-Financial Benefits
– Multi -Criteria Analysis
Let’s take an example of a software development company planning to roll out a brand-new web application. The risk assessment and treatment process could look like this:
Step 1: Identifying the Risk: Potential risks in this situation could include software bugs or errors, data breaches or cybersecurity threats, poor user experience, scalability issues, and regulatory compliance requirements
Step 2: Evaluating the Risk: Evaluate each identified risk’s likelihood and potential consequences. Here, the likelihood of software bugs could be risk evaluated based on the complexity of the application and the development team’s experience. Simultaneously, the outcomes could include reputation damage, financial loss, and loss of customer trust.
Step 3: Analyzing vulnerabilities: Analyzing the vulnerabilities in the software development process that could contribute to the occurrence or severity of the identified risks. In this example, it entails inadequate testing procedures, lack of secure coding practices, insufficient data protection measures, or insufficient resources allocated for scalability testing.
Step 4: Evaluating the existing controls: Evaluate the efficacy of current controls and risk mitigation strategies, such as code review processes, encryption protocols, data backup procedures, and compliance frameworks.
Step 5: Quantifying and Prioritizing Risks: Assign a risk level or score to each identified risk based on its likelihood and impact. Rank the risks based on their scores and prioritize them for further attention.
Step 6: Developing and Implementing risk management strategies: This mitigates the identified risks involving measures such as conducting rigorous testing at each development stage, implementing secure coding practices, enhancing data encryption and access control measures, and establishing regular security audits and compliance reviews.
Step 7: Monitoring and reviewing: Continuously monitor the effectiveness of the implemented risk management strategies involving monitoring security logs, conducting penetration testing, staying updated with relevant industry regulations, and soliciting customer feedback on user experience and functionality.
Threat Intelligence: Threat Intelligence is evidence-based information about cyber attacks that cyber security experts organize and analyze.
These details could consist of:
– Mechanisms of an attack
– How to recognize when an attack is happening
– Ways that various attacks might impact the business
– Action-oriented advice about how to defend against attacks
Threat intelligence (or security intelligence) also helps to mitigate an attack that is in progress. The more information an IT team has about an attack, the better they will be able to decide how to defend against it.
The process comprises the following steps:
– Data collection
– Data analysis
– Threat modelling
– Intelligence sharing
Threat intelligence can be categorised into four main types:
Strategic: Strategic threat intelligence provides high-level information that contextualises threats for presentation to the board of directors. It includes non-technical risk analysis, such as assessing how business decisions could expose the organisation to cyber attacks.
Tactical: Tactical threat intelligence focuses on the details of how threats are executed and defended against. It encompasses information about attack vectors, tools, attacker infrastructure, targeted industries or technologies, and evasion strategies. It helps cyber security professionals make informed decisions about security controls and defence management.
Operational: Operational threat intelligence is used by IT departments for active threat management and response. It includes information about the intent, nature, and timing of specific attacks. Ideally, this intelligence is gathered directly from attackers, although obtaining such information can be challenging.
Technical: Technical threat intelligence involves specific evidence of ongoing attacks or indicators of compromise (IOCs). It comprises information like email content from phishing campaigns, IP addresses of command-and-control (C2) infrastructure, or artefacts from known malware samples. AI-powered threat intelligence tools can scan for these indicators to identify potential threats.
These different types of threat intelligence serve varying purposes and target different stakeholders within an organization, ranging from high-level decision-makers to IT security teams. The collective use of these intelligence types enables organizations to gain insights into the threat landscape, make informed security decisions, and proactively protect their assets from cyber threats.
In the previous example, where a software development company planning to roll out a brand-new web application, it is a technical threat intelligence as it can help the company understand and mitigate potential risks associated with the application’s security. By monitoring and analyzing technical indicators, such as emerging vulnerabilities, exploit techniques, or known attack patterns, the company can proactively identify and address potential security weaknesses in the application.
The Risk Assessment and Treatment Process and Threat Intelligence are different processes comprising distinct differences.
The comparison between the two processes are as below
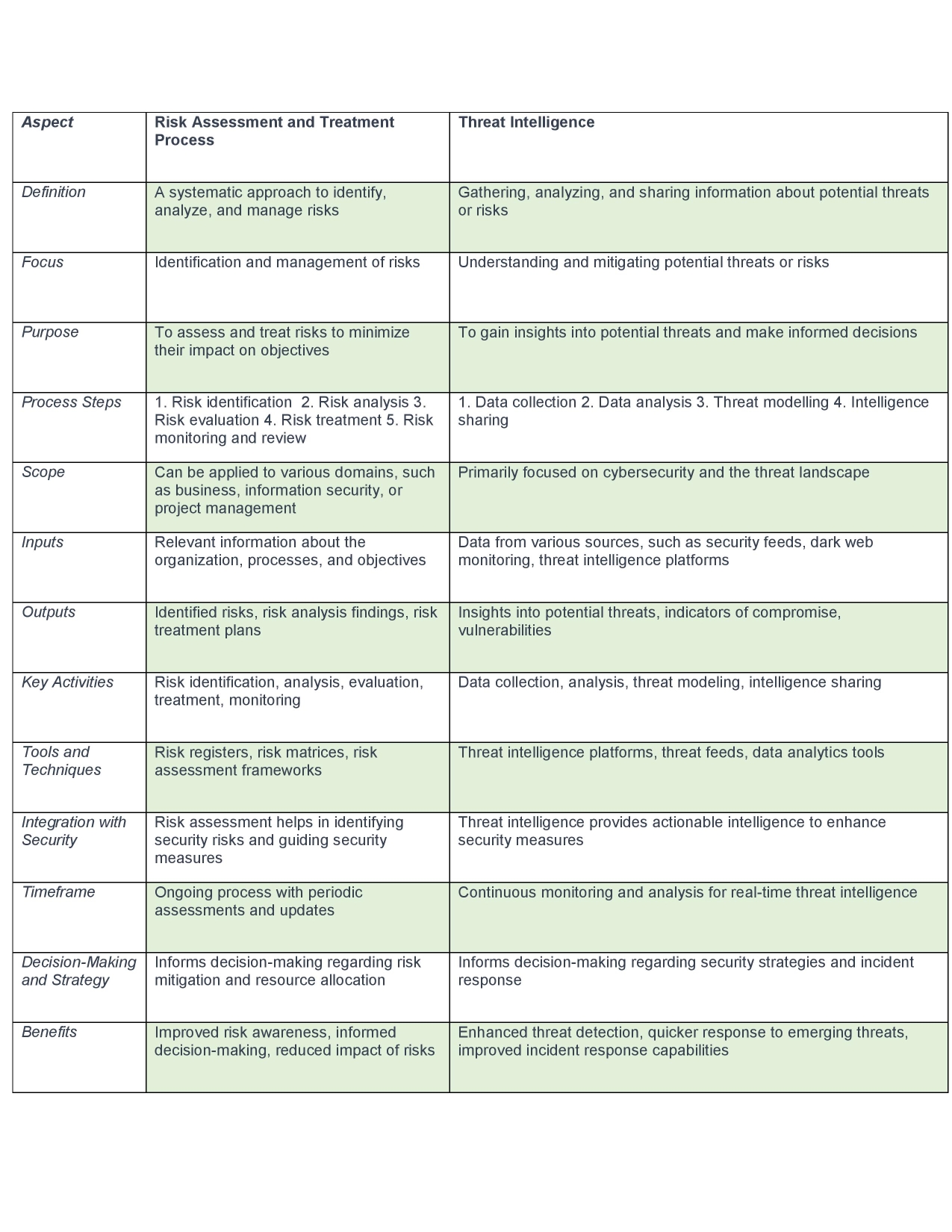
Conclusion: Taking the same example of the software development company planning to roll out a brand-new web application, the risk assessment focuses on identifying and managing risks associated with the web application rollout, whereas the threat intelligence focuses on gathering information about potential threats targeting the application to inform security measures and defenses.
